I recently presented to the 2016 Cyber Defence and Network Security (CDANS) conference in the United Kingdom. As I was preparing remarks for senior U.S. and European military leadership, I began pondering 2015 in network security and what I would advocate to these leaders.
Entering 2016 with the Ukraine attacks weighing heavily on our minds, what follows are my observations and thoughts for using 2016 to course-correct with both the recognizable patterns and greater attention to best practices to ensure our Defense in Depth strategies are agile.
What’s New
In 2015, as we do every year, Palo Alto Networks assessed application usage and threats seen on our customers’ networks. We also analyzed some of the larger attacks against government networks. From this analysis, we can learn from the patterns to help advocate for appropriate threat prevention. These trends specifically jumped out:
- SaaS is everywhere. SaaS application use has grown 46 percent since 2012. Using SaaS leads to many benefits for organizations in both the public and private sectors. At the same time, attackers can use SaaS, like anything that is popular, as a potential vector into our networks. It’s our goal to ensure organizations use it smartly. (More on that later.)
- Remote access application usage is growing. This is troubling given the access it can provide attackers to help themselves to our networks, if not adequately “provisioned.” Seventy-nine unique remote access applications were found in use worldwide, with more than 4,400 organizations using five or more different remote access applications.
- “Weaponization” of local, regional and international events. Again, the sheer fact that attackers use those topics that get our attention as a way to phish us to attack our networks is neither a surprise nor new. But the speed in which they’re doing it – within 6 hours on average from the time the event hits headlines – is increasing.
- “Attacks to attack.” Yes, hitting our partners, contractors and anyone else with “outside-in” access to our networks is not new, although in some cases the victims – such as the perhaps overlooked healthcare insurers to our government employees – might be new. Think of these attacks as intelligence-gathering expeditions. Consider that the “intelligence” or information gleaned from such attacks, including the government healthcare providers attacked in 2015, and increasingly from open source, can be helpful in attacks on target government agencies. Such intelligence on your government employees can and is being used to make spear phishing campaigns, used in subsequent attacks on government agencies, increasingly more realistic. This is intelligence gathering, or spycraft, against your targets in the modern digital age. The availability of public records, and the temptation for government employees to do what almost every other “digital” citizen anywhere in the world does – fully leveraging social media and other online services – can make operational security (OPSEC) increasingly more difficult. This information can be used to socially engineer our employees as vectors into our networks and, even worse, for other harm. The time to rethink our OPSEC approach and educate our employees about discretion in what they openly share online has never been more urgent.
- Macros: Yes, we know that macros in Office products have been an opportunity for attackers in years past. What is new this year is the resurgence of the macro. In just a few months after our 2015 report, we’re now discussing the Ukraine attacks and the Excel document macro that helped establish the initial foothold for that SCADA network attack.
New Attacks
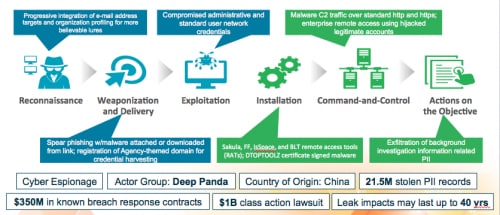
There are new attacks to be studied from which we must learn some hard lessons. Our government agencies and critical national infrastructure (CNI) were repeated targets in 2015. Looking across three major government attacks, there were new “victims” as well as similar themes from the past. Using the cyberattack lifecycle as our guide, the attackers often used either an exploit to a well-known vulnerability or malware in spear phishing campaigns to establish their initial beachhead. Other callouts to note:
- Several spear phishing attacks appeared to use progressive integration of the intelligence on the targeted agency’s employees, increasing the likelihood of success.
- In at least one attack, an agency-themed domain was used with legitimate pre-positioned documents to lure targeted employees for credential harvesting.
- In another attack, personal information was used to overcome a knowledge-based authentication system.
- The networks were exploited with the compromised administrative and other user network credentials previously stolen; and, in at least two attacks, the hijacked accounts were used to gain remote access to the network.
- In another tactic, the attackers employed an encrypted (SSL) link, embedded in email or an attachment, to deliver a malicious payload.
- In the Lotus Blossom attack, discovered in 2015 by Unit 42 but likely underway for three years prior, attackers lured ASEAN military with potentially legitimate documents – exploiting a well-known vulnerability in Office – all to plant a custom Trojan and presumably extract information from these nations.
- Finally, in December’s Ukraine power grid attack, evidence suggests that, once again, a macro in an Excel document was used to deliver a more advanced variant of Black Energy, which ultimately, together with other factors, led to the disruption of the power grid.
Repeat Offenses
These attacks serve as a reminder that we are still making the same mistakes across the people-process-technology triad, including:
- The same leadership archetypes: Where an agile, proactive 3-5 year cyber plan is needed at all management levels, many plans are still:
- Compliant and reactive, focused on checking boxes for compliance and dealing with security issues on a “reactive” basis.
- Resistant to change: convinced that their legacy approach is either working fine or would be too difficult to change, even for improved security.
- An uncoordinated technological approach to the problem: While technology can solve many of today’s security challenges, organizations still lack a cohesive, correlated security approach that reduces response time, increases manual effort, possibly increasing the risk to the organization. Increased complexity and cost are byproducts.
- No comprehensive attack lifecycle approach to the problem.
- Lack of good cyber hygiene that must be incorporated into our everyday processes.
The Way Forward
What can we learn from the 2015 application usage patterns and the government and CNI attacks?
- Be a proactive leader with a 3-5 year cyber plan:
- Be agile for changing developments: New enemies, new conflict targets, new technology enablers.
- Learn from proactive commercial, civilian government and military leadership – log on to SecurityRoundtable.org and talk to your peers, and download our leadership guide to reducing risk.
- Understand your cyber ranks and processes:
- Demand accountability: Reassess roles and responsibilities, and ensure there is clear responsibility and authority when it comes to matters of cybersecurity typically shared across your network from endpoints to the data center to the SCADA operations in your operational network.
- Test and evaluate to ensure your teams are working together to address cybersecurity. Use tests to model how your teams respond during incidents. Note that the behavioral patterns between teams and their ability to work together on the solution are just as important as the technical controls. Address any conflicts between organizations immediately.
- Ensure your Defense in Depth strategy can meet the challenges of today’s swiftly changing threat environment.
- Visibility: Start with understanding which applications are running on your network, who is using them, and why. Visibility is important groundwork.
- Reduce the attack surface: Once you understand which applications are being used in your environment and have validated those that are justified, establish security rules tying those applications to the users and user groups who need them. You can also decide which applications’ services you want to allow. As noted previously, SaaS and remote access is growing swiftly. You can decide which SaaS and remote access applications you want to allow, by which teams or individuals, what specific actions your users are allowed to take when using each one, and ensure the safety of the files in SaaS applications such as Box. These same practices reduce the risk of vulnerable applications, macros, and malware I noted previously. Reducing unnecessary applications is an important step in reducing your network’s attack surface.
- Account for the entire cyberattack lifecycle: All of the government- and CNI-focused attacks we examined used several stages of the cyberattack lifecycle to meet their goal, any one of which could have been detected and thwarted. Preventing any one important step in this chain likely could have prevented attackers from achieving their ultimate goal.
- Integrate network security controls to improve threat prevention and reduce response time: By integrating the core network security functions – firewall, IPS, web filtering, endpoint and advanced attack capabilities in our platform approach – you can automatically prevent attacks from previously seen malware and from endpoint exploits, and prevent advanced, zero-day threats within 15 minutes.
- Use the Zero Trust approach: Establish virtual segmentation based upon these user groups, ensuring access only to those who have justified access and scanning the communications entering and exiting the virtual segment for authorized access and use. This practice would mitigate the impact of attempted lateral movement if an attacker were to successfully establish a beachhead.
- Decrypt SSL communications: As noted in one of the attacks above, attackers also use SSL to hide their communications from suspicion. Ensure you have a plan to decrypt SSL.
- Measure: Measurement means so much more than compliance. Evaluate the controls you’ve put in place above to continuously measure the effectiveness. Red teaming and incident response exercises are important, using the knowledge gained to identify behavioral gaps as well as those solvable with technology. As always, test your IT as well as your OT network and personnel.
- Establish other good cyber hygiene in your everyday processes:
- System hardening, integrity assurance and software version / patch management must have higher priority. The attacks noted would have likely been prevented with such practice.
- Inbound, outbound and internal network traffic need to be controlled and monitored – including SSL communications. As we have seen from most successful attacks against government in 2015, the attacker is leveraging every “door” in and out of the network to successfully carry out their attacks.
- Anti-malware and exploit controls capable of detecting previously unknown threats are a modern necessity.
Next Steps and Resources
- Leaders: Visit SecurityRoundtable.org to download Navigating the Digital Age, and hear how your peers and other leaders are approaching their digital age risks.
- Technologists: If you haven’t already:
- Schedule a Security Lifecycle Review. Understand the gaps in your network’s security so that you have actionable information to ensure 2016 will mean less risk to your organization.
- Consider a cyberattack lifecycle gap analysis. Look at each step of the cyberattack lifecycle – from the initial foothold to lateral movement, command and control, and exfiltration – and how well you are protecting against each step from your endpoints to your network perimeter to the heart of your data center.
- Learn more about what motivates and de-motivates an average attacker by reading our latest report, Flipping the Economics of Attacks.
We don’t have to repeat the mistakes of 2015 [and, for that matter, those mistakes we have tended to repeat]. Threat prevention is possible. Let’s use 2016 as a banner year for being more thoughtful in our cybersecurity and modernize our Defense in Depth strategies to reduce the risk to our governments and critical infrastructure and ensure the resiliency of our digital way of life.
Special thanks to Rob Downs, Unit 42, for his government attack analysis.