This post is also available in: 日本語 (Japanese)
How can you and your organization deploy effective network security for containers? This question has become top of mind for network security teams as they sort through the complexities of traditional applications becoming increasingly containerized – and as they see cloud native applications rely on containers, serverless and platform as a service (PaaS) technologies. Last week’s general availability of the Palo Alto Networks CN-Series container firewall answers these concerns, based on a deep understanding of customer challenges with Kubernetes.
Consistent Security Remains a Big Kubernetes Security Concern
More and more organizations are discovering how Kubernetes and containers can be attractive options for application development. Containers can simplify development as they enable DevOps teams to move fast, deploy software efficiently and save compute resources.
Kubernetes plays a critical role in these environments by orchestrating application development in an automated way using containers. But network traffic across hosts and between container pods can also present opportunities for attackers. What’s more, containers frequently need to connect to mission-critical applications, which always need comprehensive network security.
The 2019 Cloud Native Computing Foundation (CNCF) survey indicates 78% of respondents are using Kubernetes in production – and security continues to be one of their key concerns. That overall concern was something I heard over and over from more than 50 customers I spoke with over the course of last year. They talked about their challenges in coming up with a consistent strategy for securing containers in public and private clouds.
In particular, customers were loud and clear about three primary container security challenges:
- DevOps teams deploying containers in infrastructure that network security teams are responsible for protecting – while having limited visibility into containers. This concern topped the list.
- Containers are increasingly being used with other workload types (such as virtual machines) and they need consistent network security to protect their workloads.
- Orchestrating security and firewalls with the rest of their containerized application stacks.
Network Security in Kubernetes Has Unique Requirements
Ensuring comprehensive security for Kubernetes starts with understanding how networking in Kubernetes works. Container Network Interface (CNI) is a CNCF project that defines a specification for allowing communication between containers. Kubernetes supports CNI plugins for the communication between pods. Firewalls need to be placed optimally in the network path so they can see the relevant traffic for inbound, outbound and east-west flows to and from the application pods, as seen below.
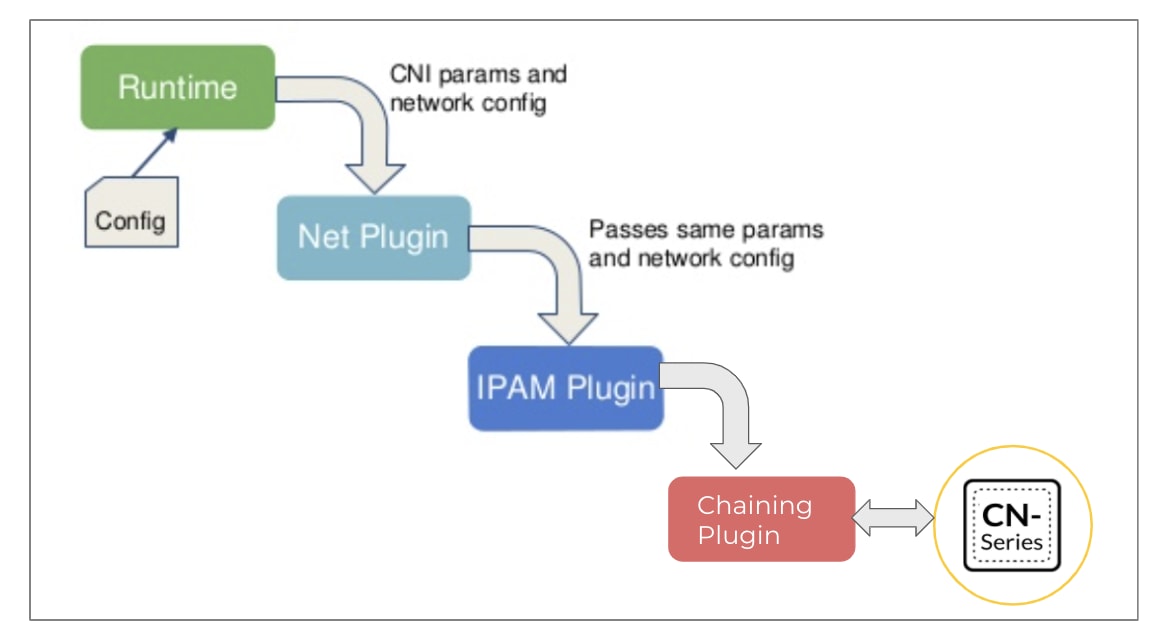
Source: Modified from CNCF CNI Documentation
This is where Palo Alto Networks CN-Series firewalls come in and leverage the CNI chaining capabilities. It’s the industry’s first containerized NGFW, and has been built so it can protect containerized applications in most Kubernetes-based environments like AWS EKS, Azure AKS, Google GKE and Openshift.
CN-Series firewalls leverage deep container context to protect inbound, outbound and east-west traffic between container trust zones along with other components of enterprise IT environments. To keep pace with DevOps speed and agility, the CN-Series makes the most of native Kubernetes orchestration and is directly inserted into continuous integration/continuous development (CI/CD) processes.
Understanding the identity of each application is key here: CN-Series has been tailored to fit into Kubernetes network architecture in ways that enable app-id, threat inspection, DNS security, WildFire, URL filtering and other critical security services. Please refer to the CN-Series data sheet for a complete list of supported environments.
Security Should Follow Kubernetes Native Security Automation
One of the primary benefits of containers is their automation capabilities. Because CN-Series firewalls are themselves containerized, ensuring that security extends to containers becomes very easy and network security teams can better work with their DevOps counterparts to plan for firewall provisioning in Kubernetes environments.
For example, most Kubernetes experts use the command-line tool Kubectl directly. DevOps teams have also started using the Helm package manager extensively as it helps them define, install and upgrade complex Kubernetes
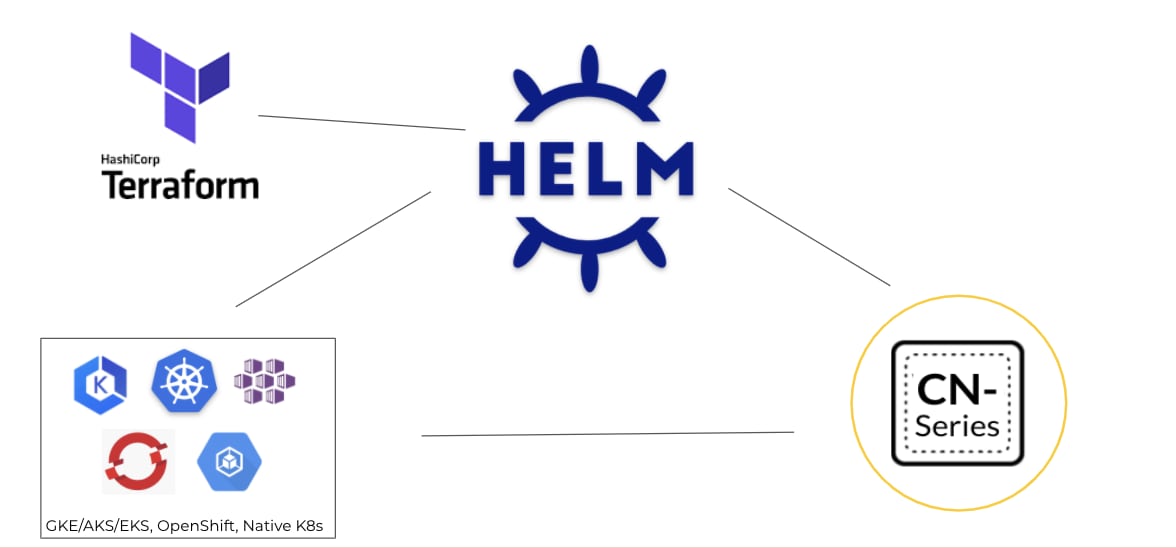
applications. Customers already familiar with Terraform software can also use it in conjunction with Helm if they use Terraform for the rest of their infrastructure as code (IaC templates). To ease lifecycle management of firewalls for our customers, Palo Alto Networks has published community-supported Helm Charts and Terraform templates.
In the cloud and containerized application space, selective traffic steering, which can be automated easily, is critical for ongoing operation and security. With CN-Series, application teams can indicate which apps need security with a single annotation in an app’s YAML files. Checks can be added in the CI/CD pipeline to make sure apps handling PCI data or that have other stringent network security requirements have NGFW security enabled. This allows for better coordination between DevOps and network security teams.
It's All About Consistent Security Policies and Threat Prevention
Most large enterprises have applications running in different workload form factors (VMs, bare metal, containers and so on) on the network – and want the ability to apply consistent policies for applications, regardless of hosting workload type.
Our customers have built security policies for their existing firewalls and are excited about CN-Series allowing them to extend these policies to containerized workloads by leveraging labels from Kubernetes. Policies can be built using labels attached on namespaces, services, replicasets and pods. This means that policies don’t need to be updated when apps scale.
It’s important to understand that most containerized apps have known and unknown vulnerabilities, both of which can be exploited on the network. The rich set of threat prevention capabilities in CN-Series helps reduce needed resources, complexity and latency by automatically blocking known malware, vulnerability exploits and C2 traffic. We continue to add threat coverage for components of containerized infrastructure such as Kubernetes, Docker and Openshift, as well as for most containerized apps including Redis, MongoDB, WordPress and Nginx. Automation of policies can be accomplished using the integration of Palo Alto Networks Cortex XSOAR and PAN-OS, as seen below.
Palo Alto Networks strongly believes container adoption demands comprehensive protection all the way from scanning container registries in the CI/CD pipeline to network security in production deployments. We have built the most comprehensive suite of products in Prisma Cloud and in CN-Series firewalls to ensure security concerns do not remain a hindrance as you embark on the container adoption journey.
So how can you and your organization deploy effective network security for containers? To discover in-depth technical details about how CN-Series has been designed to resolve burning container security questions, visit CN-Series TechDocs.