Introduction
The Cortex XSIAM Response and Remediation Pack is essential to modern security operations centers (SOCs). It enables organizations to proactively address security alerts and automate response actions in alignment with the vision of an autonomous SOC. This blog introduces the playbook "A mail forwarding rule was configured in Google Workspace", designed to address risks associated with unauthorized email forwarding configurations.
Threat Overview
Attackers can exploit email forwarding rules to siphon sensitive information from corporate email accounts to unauthorized destinations. These rules, especially when configured to forward emails to uncommon or suspicious domains, represent a significant security threat.
Beyond data exfiltration, attackers may use email forwarding rules as a commandand control (C2) mechanism to issue instructions or maintain persistent access to compromised accounts. Such activity may signal account compromise or insider threats and requires swift investigation and remediation.
Detecting and neutralizing these configurations is crucial to preserving organizational data integrity and preventing unauthorized access to sensitive information.
Purpose of the Playbook
The "A mail forwarding rule was configured in Google Workspace" playbook is designed to:
- Investigate alerts related to the configuration of email forwarding rules.
- Identify potential malicious intent by analyzing caller IPs, forwarding domains, and rule configurations.
- Automate and guide response actions to contain and remediate threats.
This playbook is a vital resource for SOC teams, equipping them with the tools to efficiently and swiftly address email forwarding-related incidents. It ensures thorough oversight and documentation, enabling teams to maintain control and respond effectively to potential threats.
Alerts Addressed by the Playbook
This playbook addresses the following alerts:
- "A mail forwarding rule was configured in Google Workspace."
- "A mail forwarding rule was configured in Google Workspace to an uncommon domain."
Stages of the Playbook
The "A mail forwarding rule was configured in Google Workspace" playbook follows these stages:
Triage:
-
- Retrieves the caller’s IP address, forwarding email address, and filters associated with the forwarding address.
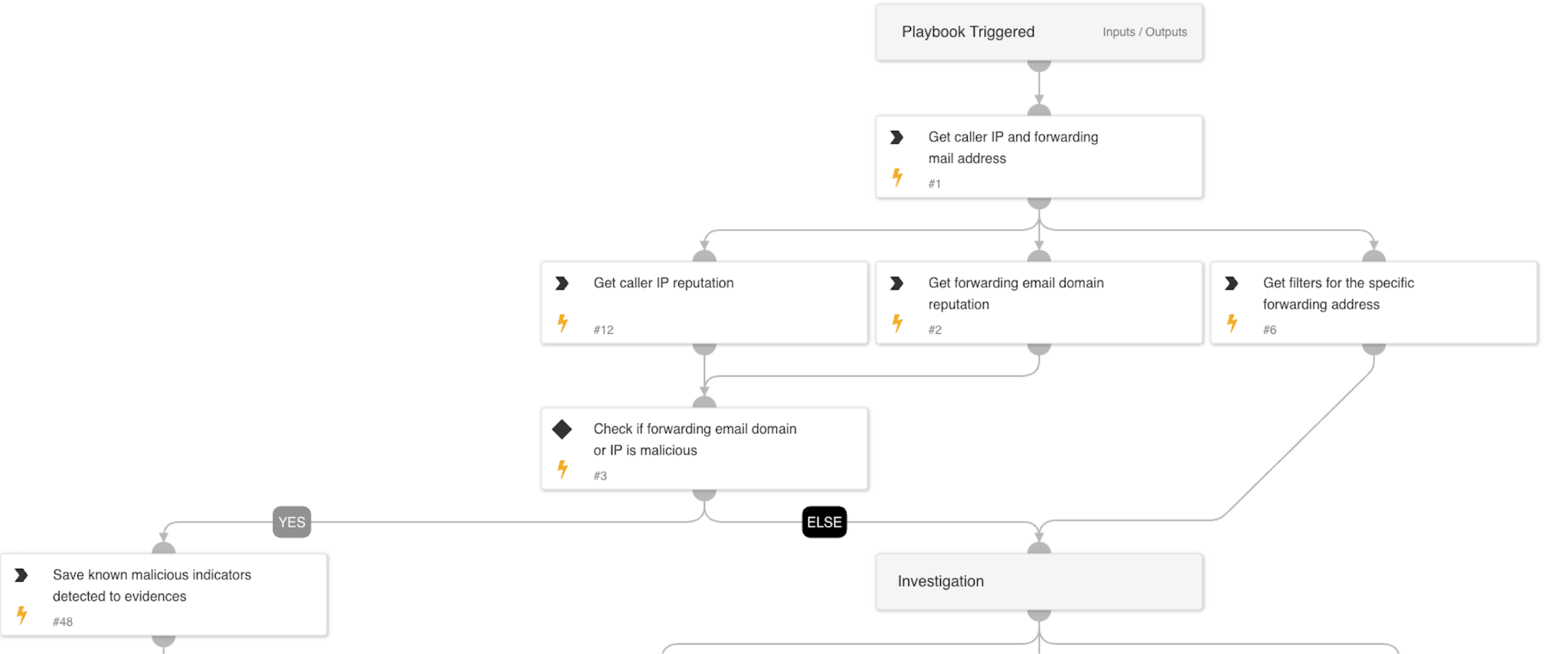
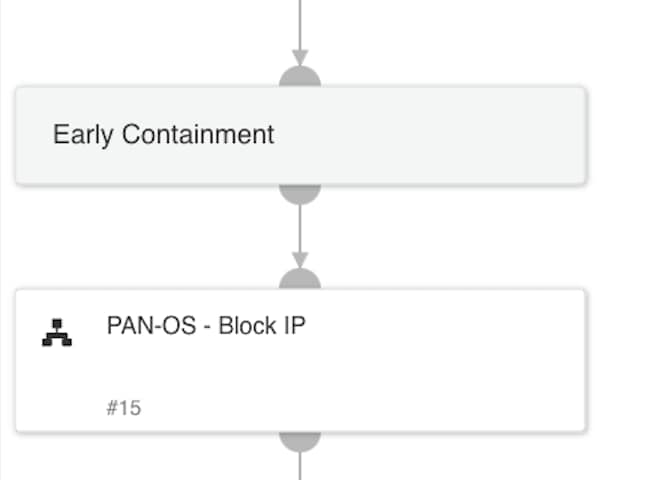
Early Containment:
-
- Check if the IP or domain of the forwarding email address is malicious.
- Suggests blocking the IP address using PAN-OS while continuing the investigation.
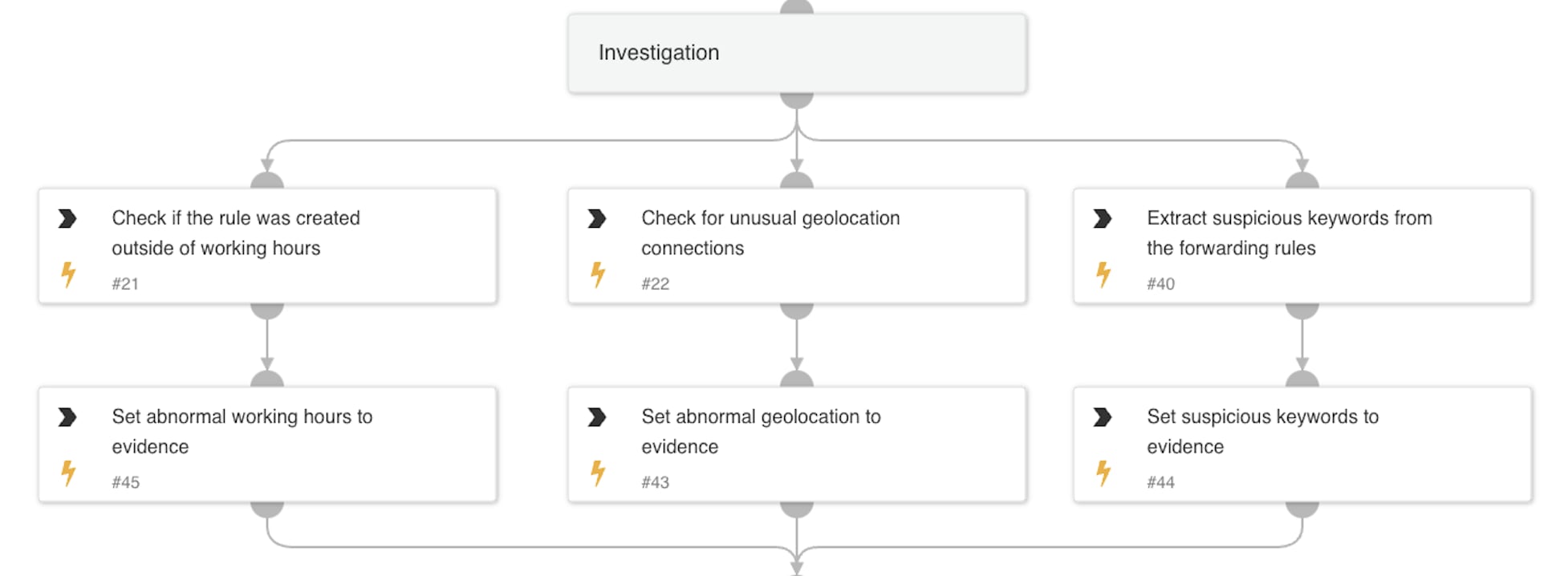
Investigation:
-
- Verifies if the rule was created outside working hours or from an unusual geolocation.
- Extracts suspicious keywords from the forwarding rule filters.
- Aggregates all evidence collected during the investigation.
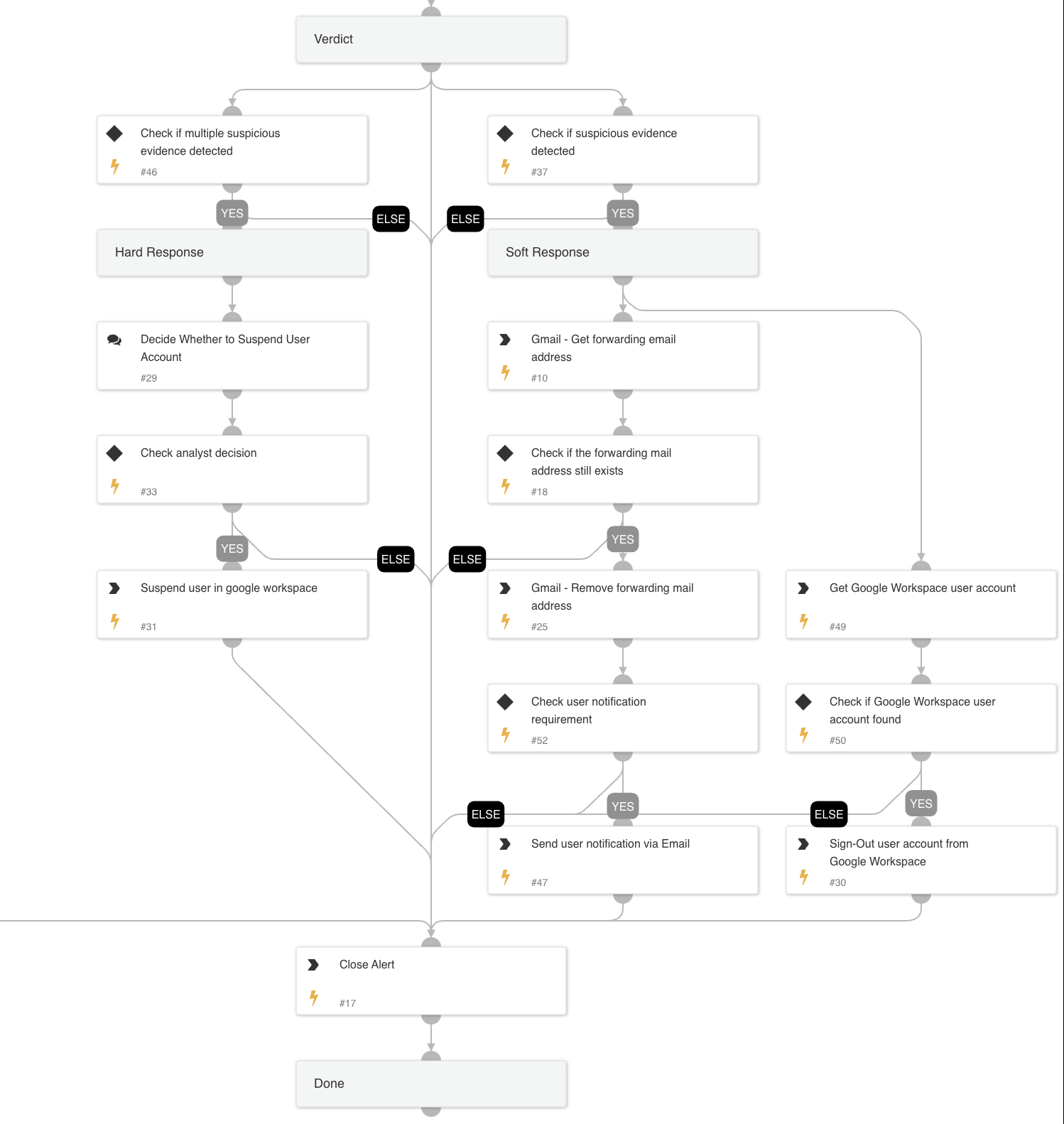
Containment:
-
- If a single suspicious evidence is found, it executes soft response actions, including:
- Signing the user out of Google Workspace.
- Deleting the forwarding email address from the user’s mailbox. As a result of deleting the forwarding address, the associated forwarding rule filters will also be removed.
- Notifying the user via email of the actions taken.
- If multiple suspicious pieces of evidence are found, the system combines soft response actions with hard response actions, recommending the suspension of the user account. The list of detected evidence will be presented to the user in the hard response data collection task.
- If a single suspicious evidence is found, it executes soft response actions, including:
Security Challenges Addressed
This playbook addresses key challenges in managing email forwarding rule configurations:
- Swift Detection: Quickly identifies potentially malicious email forwarding rules.
- Automated Containment: Provides rapid response actions to neutralize threats.
- Comprehensive Investigation: Aggregates evidence and provides context to inform decisions.
- Flexible Remediation: The system balances automation with analyst input to ensure effective threat mitigation, providing reassurance about the adaptability of the system.
Conclusion
Unauthorized email forwarding rules pose a significant security risk that requires immediate attention. The 'A mail forwarding rule was configured in Google Workspace' playbook is a powerful tool that empowers SOC teams to efficiently detect, investigate, and remediate these threats. By leveraging the Cortex XSIAM Response and Remediation Pack, organizations can significantly enhance their incident response capabilities and protect their critical email communications.
Learn More
Discover more about the Cortex XSIAM Response and Remediation Pack and its powerful playbooks on the Cortex Marketplace.