Cybercriminals are evolving, and their latest technique for stealing sensitive data is nearly invisible to traditional defenses. Instead of breaking in through conventional methods, attackers now use a slow and stealthy approach, exfiltrating data by hiding inside host headers of web requests. To stop this, we’re introducing a new feature, Exfiltration Shield, that prevents data exfiltration via DNS relay attacks.
How Attackers Are Bypassing Defenses
Imagine a thief trying to smuggle stolen jewelry out of a high-security building. If they walk out the front door with a bag of stolen goods, security will stop them immediately. Instead, they hide small pieces of jewelry inside everyday mail, letters, invoices, or packages, going to well-known, trusted companies. Since security doesn’t usually check these types of outgoing mail, the stolen jewelry passes through unnoticed.
How does the thief get the stolen jewelry back? The mail is first sent to trusted companies, which then unknowingly forward it to an address controlled by the thief. Once intercepted, the thief collects and reassembles the stolen pieces, completing the heist without ever being detected.
This is exactly how relayed data exfiltration via HTTP headers works. Instead of sending stolen data in large chunks, which might raise red flags, attackers break it into tiny pieces and hide it inside web traffic that goes to trusted websites. Many security tools only focus on the most obvious threats, like hacking attempts or malware. Still, they don’t inspect the details inside web traffic, especially the host headers, which are a behind-the-scenes part of web communication.
Why Relayed Data Exfiltration via HTTP Headers Is Dangerous
The reason this is such a huge problem is that traditional security tools don’t catch it.
- Most security systems don’t check host headers in HTTP and TLS requests, meaning attackers can hide stolen data in plain sight.
- The attack leverages trusted domains, so security tools don’t flag the traffic as suspicious.
- New websites are created every day, giving attackers an ever-growing pool of domains to exploit, making it nearly impossible to manually block every potential threat.
A recent study tested one million top websites and found that attackers were leveraging many of them for data exfiltration, exploiting trusted domains to evade detection. That means even web traffic that looks benign could be leaking sensitive data without you ever realizing it.
How Exfiltration Shield Stops It
To combat this stealthy and highly evasive attack, we’ve developed Exfiltration Shield, an industry-first feature that combines relay detection in Advanced Threat Prevention (ATP) with FQDN validation in Advanced DNS Security (ADNS) to extract hostnames in web requests and verify those domains in real time. Unlike traditional security solutions that rely on limited header inspection and outdated signature-based detection, Exfiltration Shield automates detection and blocking with no manual configuration required.
Attackers take advantage of millions of trusted host websites, using them to exfiltrate data without validation. Our solution cuts them off at the source, stopping exfiltration before it can begin. Here’s how:
- Unmatched Visibility: Analyzes every HTTP and TLS request, ensuring attackers can’t hide stolen data where traditional security tools aren’t looking.
- Real-Time Blocking: Automatically detects and stops malicious traffic, eliminating the need for security teams to track every possible website attackers might exploit manually.
- Adaptive Protection: Uses AI-powered analysis to instantly identify and block emerging threats without relying on outdated, signature-based security.
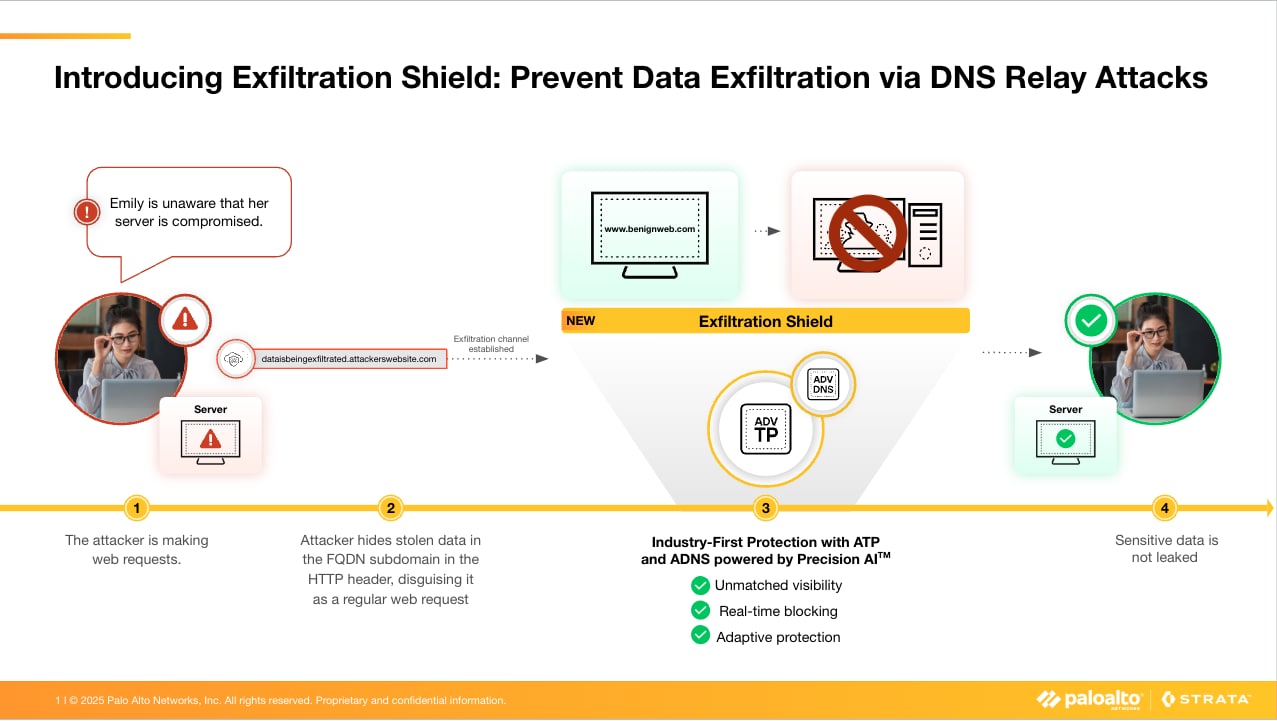
Exfiltration Shield blocks data exfiltration by preventing DNS relay attacks via HTTP headers.
This isn’t just another feature, it’s a key part of our ongoing mission to provide consistent, best-in-class protection everywhere. By combining the strengths of two of our security subscriptions, ATP and ADNS, we deliver best-in-class protection that works seamlessly to stop even the most sophisticated threats. This is the power of platformization.
Protecting Against the Latest Attack Techniques: The Proof Is in the Data
And the data speaks for itself. Our latest advancements in Cloud-Delivered Security Services (CDSS) show the real impact of our continuous innovation:
- We’ve seen an 18% increase in events – analyzed daily, from an average ≤4.6 billion to now ≤5.43 billion, which includes benign and malicious activity across files, URLs, domains and network sessions.
- What’s most troubling is that new and unique attacks have increased by ~4X – every day (increasing from ≤2.3 million to ≤8.95 million). This includes detections of new threats like relayed attacks.
- Of all these threats, we’re blocking ~3X more attacks inline – Jumping from ≤11.3 billion to ≤30.9 billion each day, stopping them in real-time before they reach the network, endpoint or user, preventing damage before it even starts.
Now Available: Get Industry-Leading Protection Today
Exfiltration Shield is now generally available. If you’re a current ATP customer, you can enable inline cloud analysis in your configuration to start protecting your organization from data exfiltration immediately.
If you are not an ATP customer yet, now is the time to upgrade. Contact a sales representative today to learn how you can get best-in-class security that stops evasive threats before they cause harm.