Defending against cyberthreats requires organizations to test their cloud security posture and detection capabilities. Traditional assessments, though, typically focus on isolated, single-point simulations. Unless you evaluate your organization’s security against comprehensive, multistep attacks, you’re leaving critical vulnerabilities unaddressed.
Real-World Attacks Tower Over Single-Point Simulations
Single-point simulations are a popular starting point for many organizations due to their simplicity and ease of implementation. They allow security teams to focus on specific threats or vulnerabilities, providing a clear and targeted way to test the effectiveness of particular security controls. These simulations are valuable for validating aspects of an organization's security posture — testing a new firewall rule, evaluating the response to a type of malware, ensuring compliance with certain regulations. But real-world attacks aren’t one-dimensional. Moreover, they’re rarely linear.
In the wild, cyberattacks are sophisticated, multistaged and often involve a series of chained exploits targeting different parts of a cloud infrastructure. Attackers meticulously plan their strategies, move laterally across environments, escalate privileges and exploit vulnerabilities at various stages. Single-point simulations can’t adequately capture the complexity and interconnectedness of these attack vectors.
Limitations of Single-Point Simulations
Incomplete Threat Representation
By focusing on individual vulnerabilities or isolated incidents, single-point simulations fail to represent the spectrum of potential threats. They miss the intricate pathways attackers might use to move from one system to another.
False Sense of Security
Organizations relying solely on single-point simulations may develop a false sense of security, believing their defenses are more robust than they actually are. This complacency can lead to undetected vulnerabilities and unpreparedness for sophisticated attacks.
Ineffective Detection and Response
Modern attacks often involve multiple stages, each designed to bypass specific security measures. Single-point simulations do not adequately test an organization’s ability to detect and respond to these complex, multistaged attacks. This results in gaps in detection capabilities and delayed response times during incidents.
Lack of Contextual Insights
Security teams need contextual information to understand how different vulnerabilities can be exploited in conjunction. Single-point simulations don’t provide the necessary context, making it difficult for security teams to prioritize and address the most critical threats.
To effectively assess and enhance security in multicloud environments, there’s a need for tools that can simulate sophisticated multistage attacks.
Introducing Cloud Offensive Breach and Risk Assessment (COBRA)
COBRA is designed to address testing challenges by providing a platform that simulates multistaged, cloud-native attacks. It helps organizations move beyond the limitations of single-point simulations. By mimicking the tactics, techniques, and procedures (TTPs) used by real-world attackers, COBRA empowers teams with an accurate understanding of their security posture and the efficacy of their security tooling.
With COBRA, organizations can:
- Evaluate Security Posture: Understand the interconnectedness of their systems and how vulnerabilities can be exploited in a chain of events.
- Improve Detection Capabilities: Test and enhance their ability to detect and respond to complex attack patterns.
- Prioritize Security Measures: Identify and address the most critical vulnerabilities within the context of real-world attack scenarios.
- Defend Against Advanced Threats: Equip security teams with the knowledge and tools to anticipate and mitigate sophisticated threats.
Key Features of COBRA
Simulating Multistaged Cloud-Native Attacks
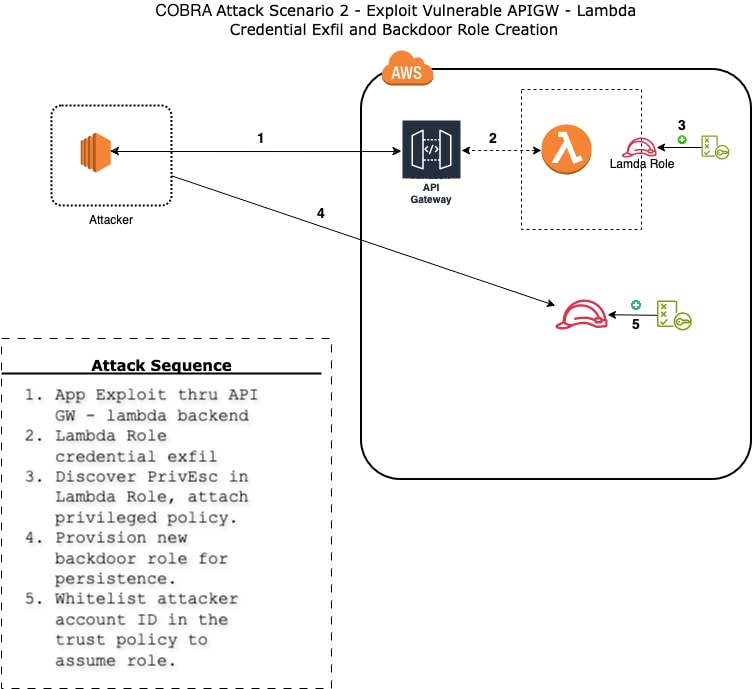
COBRA simulates complex, multistaged attack scenarios that mirror real-world tactics used by cyberattackers. This includes lateral movement, privilege escalation and data exfiltration across various cloud services. Additionally, it demonstrates how individual vulnerabilities can be linked to create sophisticated attack chains, providing a more comprehensive assessment of security weaknesses.
Comprehensive Coverage Across Major Cloud Providers
COBRA supports major cloud platforms, including AWS, Azure and Google Cloud, enabling organizations to assess their security posture across different environments. Integrating seamlessly with cloud-native services and tools, it ensures accurate simulations within the specific contexts of each provider.
Detailed Reporting and Analysis Tools
COBRA generates detailed reports that highlight vulnerabilities, attack paths and potential impacts. These reports provide actionable insights for improving security measures. Reports include:
- Details of the attack
- Sequence of the attack
- Architecture diagram
- Resource metadata
- List of controls to evaluate
The tool offers visual representations of attack chains and vulnerabilities, making it easier for security teams to understand and communicate findings.
Open-Source and Community-Driven Development
Being open-source, COBRA encourages contributions from the security community, fostering collaboration and continuous improvement. It’s designed to be extensible, allowing users to add new features, integrations and attack scenarios based on evolving security needs and threats.
Architecture Overview/Technical Details
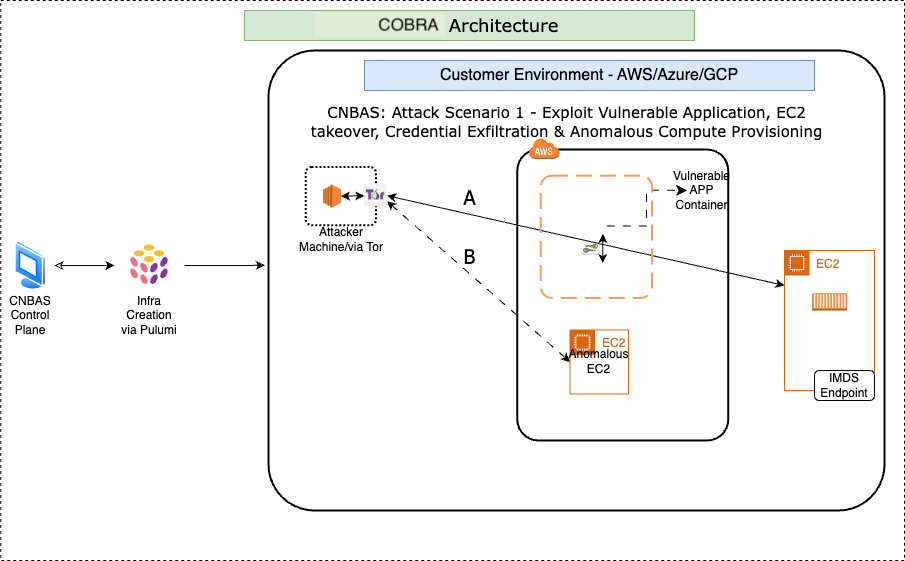
COBRA is designed with a robust and flexible architecture that leverages modern technologies to simulate realistic attack scenarios in multicloud environments. Let’s briefly explore its core components and architecture.
Attack Simulation with Python
Using Python, COBRA simulates various stages of an attack, such as reconnaissance, exploitation, lateral movement and data exfiltration. Python scripts define the sequence of actions an attacker might take, ensuring that the simulations are both realistic and customizable to specific environments.
Infrastructure Deployment with Plulumi
Pulumi is used to define and manage cloud infrastructure as code, which allows COBRA to automatically roll out the necessary infrastructure components required for the simulations. Pulumi’s multicloud capabilities enable COBRA to consistently and efficiently deploy and configure resources across different cloud providers (AWS, Azure, Google Cloud).
Pulumi scripts handle the dynamic setup and teardown of cloud environments, ensuring that the infrastructure is provisioned only for the duration of the simulation.
Extensible & Modular Design
COBRA's architecture is modular, allowing users to easily extend its capabilities by adding new attack modules or integrating additional cloud services.
The open-source nature of COBRA encourages community contributions, making it easy for users to enhance and customize the tool according to their specific needs.
COBRA Use Cases
- Identify and exploit vulnerabilities in applications to take over EC2 instances, extract sensitive credentials, and detect irregular provisioning of computing resources.
- Target and exploit REST API vulnerabilities, including command injection, to exfiltrate credentials from a backend Lambda function, escalate privileges, and illicitly create persistent, rogue identities.
- Compromise a web application hosted in a Google Kubernetes Engine (GKE) Pod, access Pod secrets, escalate privileges within the cluster, and ultimately achieve cluster takeover.
Learn More
Whether you are a security professional, a solution architect or part of a DevOps team, COBRA provides the tools you need to test your cloud infrastructure security controls. We encourage you to try out COBRA to see for yourself how it can transform your approach to cloud security.
Going Forward: We are committed to continually improving COBRA and expanding its capabilities. Future developments include adding support for more cloud services, refining attack scenarios and enhancing the user interface for better usability. Stay tuned for upcoming features and updates that will further empower you to secure your cloud environments.