The Evolution of a Threat Intelligence Platform
The ever-evolving threat landscape has put Security Operations Center (SOC) teams on high alert for a while. As the remote workforce tries to keep pace with the demands of a newer working environment, threat actors have been hard at work trying to exploit every vulnerability.
Adding to the complexity is the shortage of a high-quality workforce that leaves SOC teams overburdened with an endless stream of security incidents. What your SOC team needs is a high quality Threat Intelligence Platform (TIP) that is packed with unique capabilities to help them use the power of intelligence to do more with TIP than ever before.
What’s New in Cortex XSOAR Threat Intelligence Management 3.0
Today we are announcing the launch of Cortex XSOAR Threat Intelligence Management 3.0. This release comes with a set of powerful new strategic intelligence capabilities that help an entire organization fight cybercrime with confidence so your security team can focus on what’s important. Remember how TIM 2.0 helped security teams unblock the power of threat intelligence by making it actionable? Now TIM 3.0 is geared to take Threat Intelligence to the next level with advanced capabilities that enable the entire threat intelligence management lifecycle.
What to Expect with Threat Intelligence Management 3.0
Strategic Intelligence Reports
TIM 3.0 enables users to create, share, customize, and export threat intel reports. It also allows users to categorize the report by type and select the layout that is displayed for the report. This is particularly useful as threat intel reports provide a summary of the threat intelligence research, changing the way organizations communicate the current threat landscape to internal and external stakeholders, customizing the report based on the person receiving it. It could be any report ranging from a high-level summary report for C Level executives, to a detailed, tactical report for the SOC and other security stakeholders.
The new Cortex XSOAR Threat Intel Management 3.0 gives you the following out-of-the-box report types:
- Campaign
- Executive Brief
- Malware
- Threat Actor
- Vulnerability
You can also add new report types to support use cases not covered by the out-of-the-box types, which may require different report layouts. In addition, you can customize the layout of an existing out-of-the-box report.
Most Powerful Threat Data from Unit 42
With TIM 3.0, you get fully integrated threat data with real-world intelligence and malware analysis repositories to identify and discover new malware families or campaigns. You can now access threat intel data with “Full View,” which shows the full Cortex XSOAR indicator summary with a lot more details.
This feature helps you understand which malware families, campaigns, or attack techniques are related to your security incidents. It gives analysts unprecedented capability to identify and track new threats as they rise from 30B+ samples collected and analyzed by Palo Alto Networks. billions of malware samples.
The Power of Extended Real-Time Threat Data
The previous release of Threat Intelligence Management helped you gain unique visibility into cyber threat intelligence curated by Unit 42. It enabled analysts to collaboratively build threat actor, campaign, and attack techniques profiles relevant to your industry. Now TIM 3.0 is taking it to the next level, empowering you to act with high confidence. Besides learning about the threat actors, you will also learn about malware families, campaigns, or attack techniques related to your security incidents. This gives analysts unprecedented capability to identify and track new threats as they arise across tens of billions of malware samples.
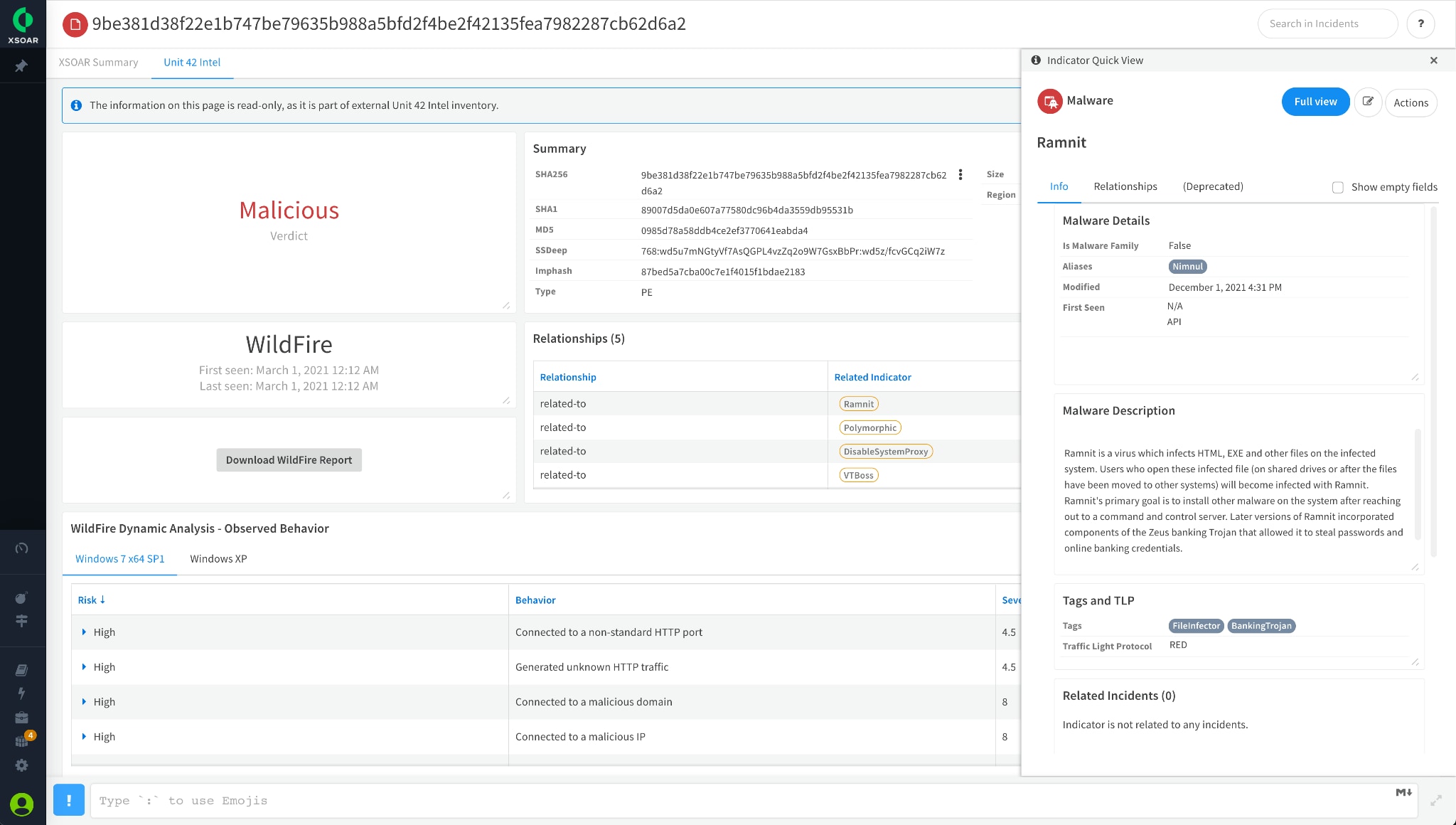
Figure 1: Out of the box intelligence from Unit 42
Get Strategic with Advanced Reporting Capabilities
Strategic threat intelligence provides a big picture of how threats and attacks change over time. Intel may include historical trends, motivations and attributions to who is behind the attack. This gives threat intelligence teams clues to future adversary operations and tactics and helps them decide which defenses will be most effective.
Tim 3.0 release takes our Threat Intelligence Platform to the next level with workflows and a central repository for intelligence analysts to create and share finished intelligence products with stakeholders. Intel analysts will be able to understand trends within threat intelligence using their local/curated intel from Unit 42.
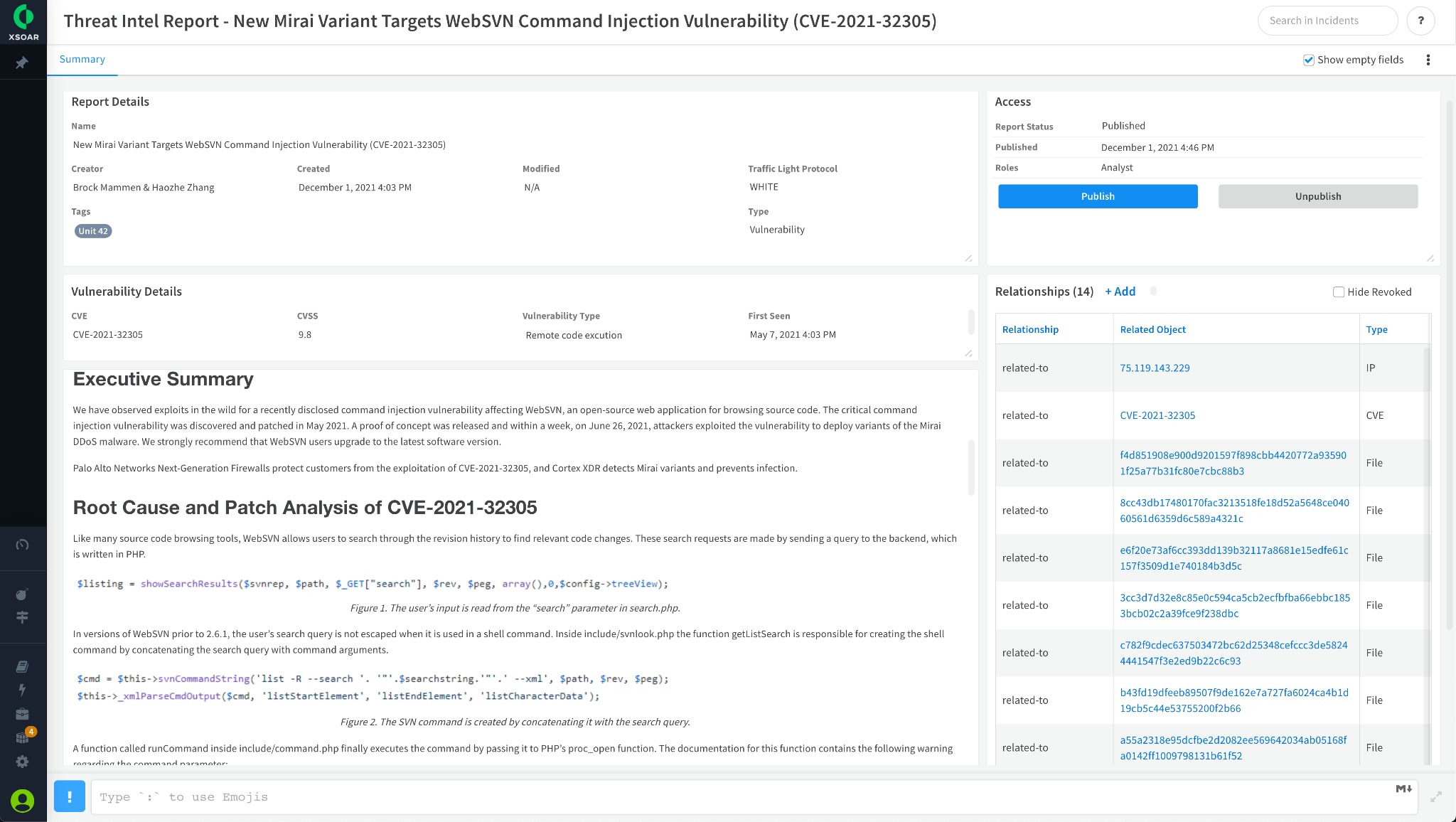
Figure 2: Strategic Threat Intelligence reporting
The Future of Security Operations Lies in Operationalizing with Automation
As we move into 2022, SOC teams continue to battle the shortage of staff and skilled analysts along with budget limitations. The future of security operations will lie in operationalizing the threat data effectively with automation. To truly harness the power of threat intelligence, reduce the data overload experienced by security teams fighting false alarms and enable your SOC teams with the right data and context, you need a threat intelligence platform that:
- Can collect, aggregate, organize, identify and automate responses to frequent threats such as phishing and malware
- Is strategic, builds customized out of the box reports to share with stakeholders
- Has capabilities to support the entire threat intelligence management lifecycle
Want to Know More?
We’ve gathered cybersecurity and threat intelligence experts to share their strategies, best practices, and analysis of the threat intelligence platform.

Join us for the launch event with the world's most famous hacker, Kevin Mitnick, and our guest speaker from Forrester, Joseph Blankesnhip, as we reveal what’s next in Cortex XSOAR Threat Intelligence Management. Register here.
Explore some use cases for a Threat Intel Platform and a technical deep dive of Threat Intelligence Management 3.0 with a demo. Register here.
