Amp Up Your SOC Automation with Cortex XSOAR 8.5
XSOAR 8.5 continues the evolution of XSOAR 8 which started with a SaaS platform and tight integration with the Cortex suite of products.
Our XSOAR roadmap continues to focus on these three key pillars to ensure our customers get maximum value out of their XSOAR investment:

Highlights of Cortex XSOAR 8.5 include the following:
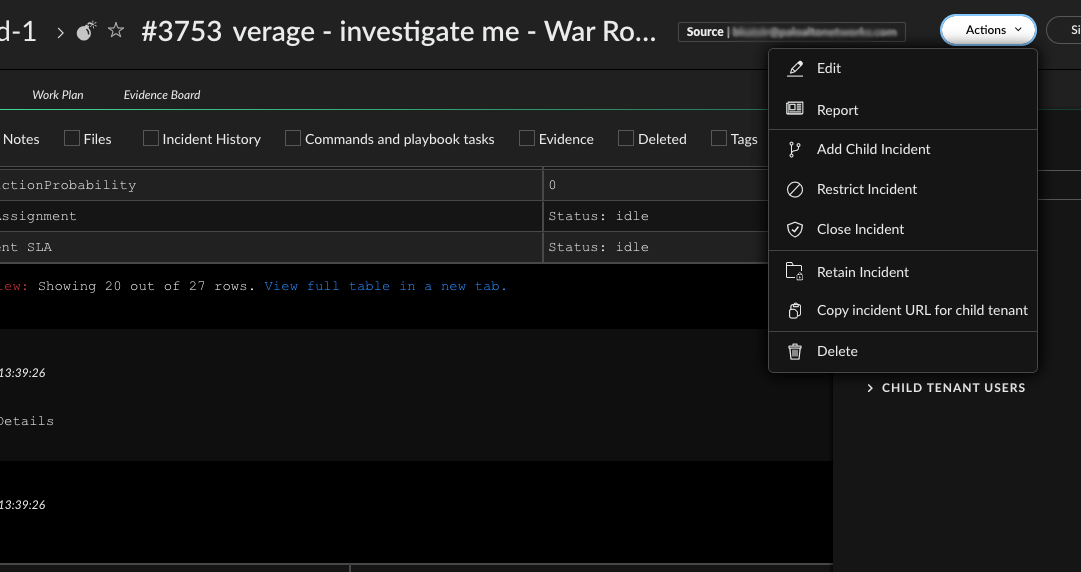
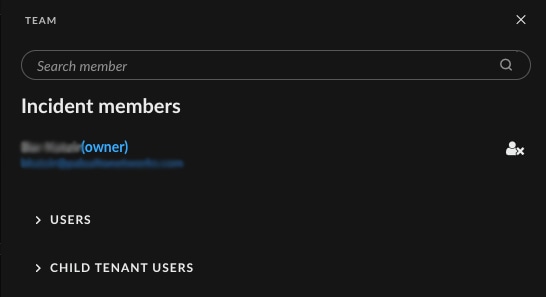
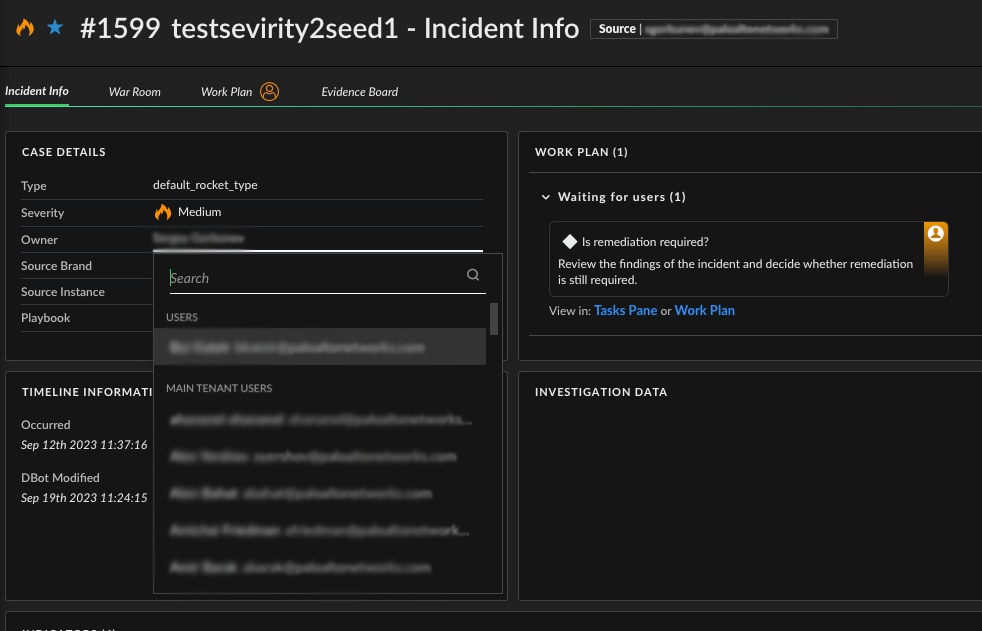
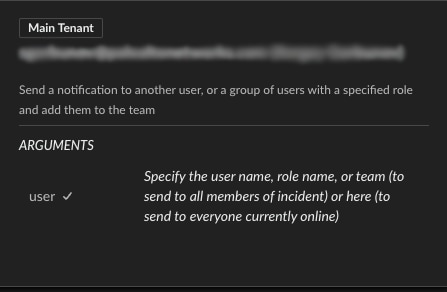
- Multi-tenant bi-lateral communication (MSSP) - You can now easily invite users from main and child tenants to incident investigations (including tasks, CLI and War Room). You can share investigation links with end-customers via email, Slack or Microsoft Teams. This enhancement allows managed security service providers (MSSPs) to improve service delivery and optimize customer satisfaction.
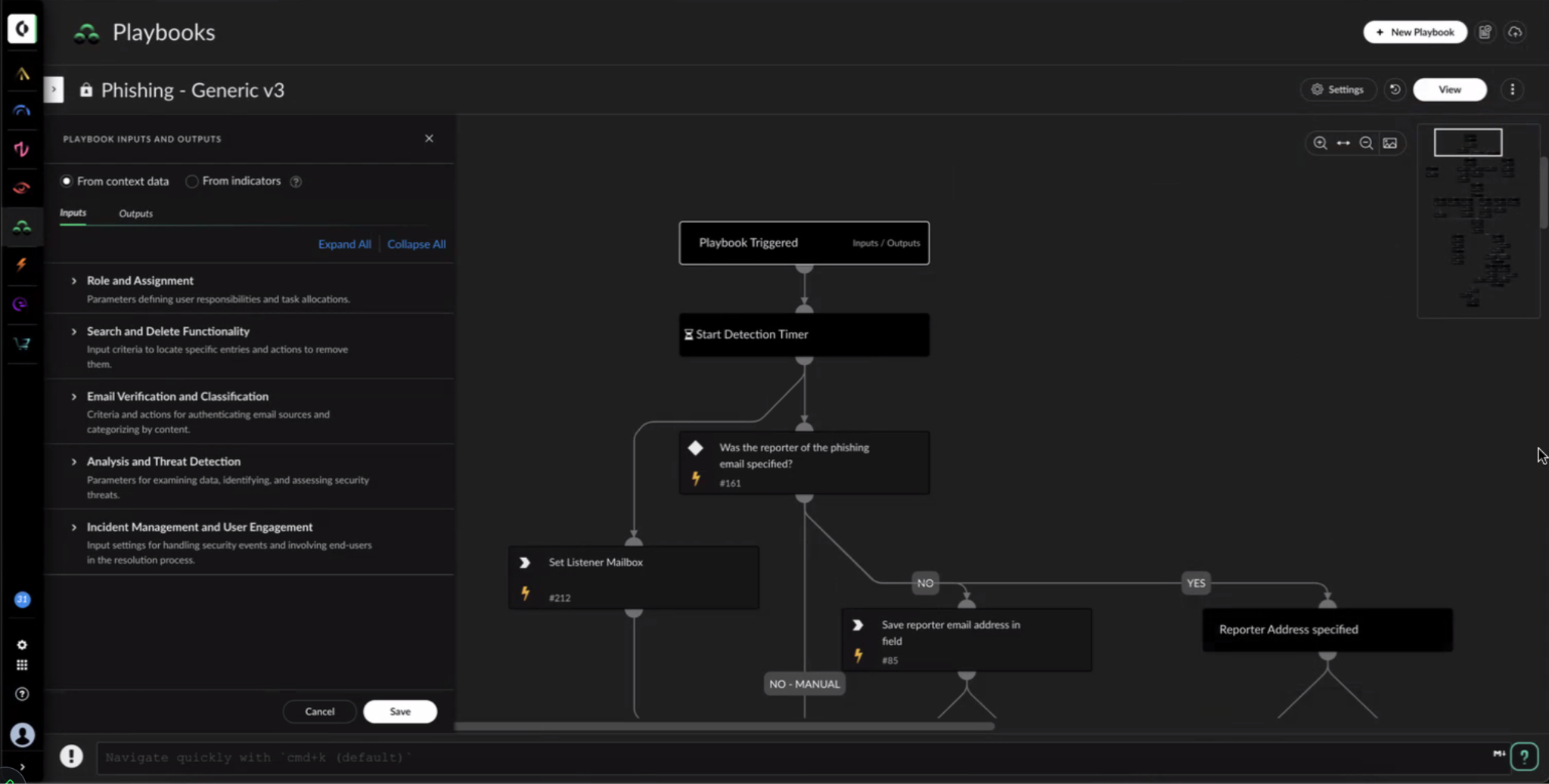
- Playbook inputs grouping - You can now group playbook inputs and outputs, making it easier to manage and understand the inputs required for different stages of the playbook. Grouping enhances playbook clarity, reduces the likelihood of errors, and facilitates a more streamlined and efficient incident response workflow.
- Content Repository Enhancement - Easier configuration and management of your content repository in the Cortex Gateway and Cortex XSOAR. You can switch between repository types and choose the initial synchronization setup, enabling you to develop and maintain Cortex XSOAR content that is aligned with your development process.
- Improved Incident Navigation & Search
- For SOC analysts working on multiple incidents, next/previous navigation buttons provide the ability to navigate between incidents without returning to the Incidents page, saving time and facilitating analyst workflow efficiency.
- You can now do searches on War Room notes using the Incidents search bar. This new search option enables SOC analysts to query historical incident data for improved incident response and knowledge sharing.
- System Email Customization - You can now customize a wide range of system emails sent to users, including notifications when a user is mentioned, a task is assigned or completed, an integration has failed to fetch incidents, an engine is disconnected, and more. Customized emails give you the flexibility to include specific details about incidents, relevant data, and other information needed for prompt incident response.
- XSOAR Content Packs and Integrations (Oct 2023 to Feb 2024)
- AWS Organizations - Manage your AWS accounts and resources via Cortex XSOAR. You can list and create new accounts, view details, modify Organizational Units, invite and tag accounts.
- HashiCorp Terraform - Get policy check results and support more commands.
- Email Hippo - Validate email addresses and domains directly in Cortex XSOAR using Email Hippo’s intelligence services.
- XSOAR Capture the Flags - An interactive and fun way for your users to get familiar with Cortex XSOAR. Two playbooks guide participants through a series of tasks as they compete against each other to “capture the flag”. The first playbook walks participants through the platform while the second playbook introduces them to investigating an incident within XSOAR.
- XDR Lite Playbook - This new playbook is easy to deploy, with no additional integration needed. It can significantly reduce the time your analysts spend remediating XDR incidents.
- LOLBIN Command Execution Alerts - Automated investigation and response for PsExec-like LOLBIN command execution alerts from Cortex XDR. This new playbook enriches relevant data and performs actions such as command-line analysis and remediation.
- Microsoft Graph Security - This integration has been updated to support creating and retrieving email, files, and URL threat assessments directly from within Cortex XSOAR.
- Azure Log Analytics - Now allows you to run Log Analytics search jobs and retrieve results in Cortex XSOAR.
- PAN-OS Policy Optimizer - Enhanced to support pagination and allow the fetching of more rules when analyzing firewall policies.
- SplunkPy - Enhanced to enrich user and asset fields via lookups in Splunk from within Cortex XSOAR.
- Prisma Cloud Compute Audit Alert v3 playbook - Help SOC and DevOps teams better streamline their investigations of cloud incidents with new remediation and enrichment features that provide rich contextual information for better decision-making.
For a complete list of new features, please see the Cortex XSOAR 8.5 release notes.
Take our SOC Automation Tour
See how Palo Alto Networks’ SOC leverages automation to help keep your networks secure. Get an inside look at using automation to hunt threats as well as process and triage incidents. Watch now!