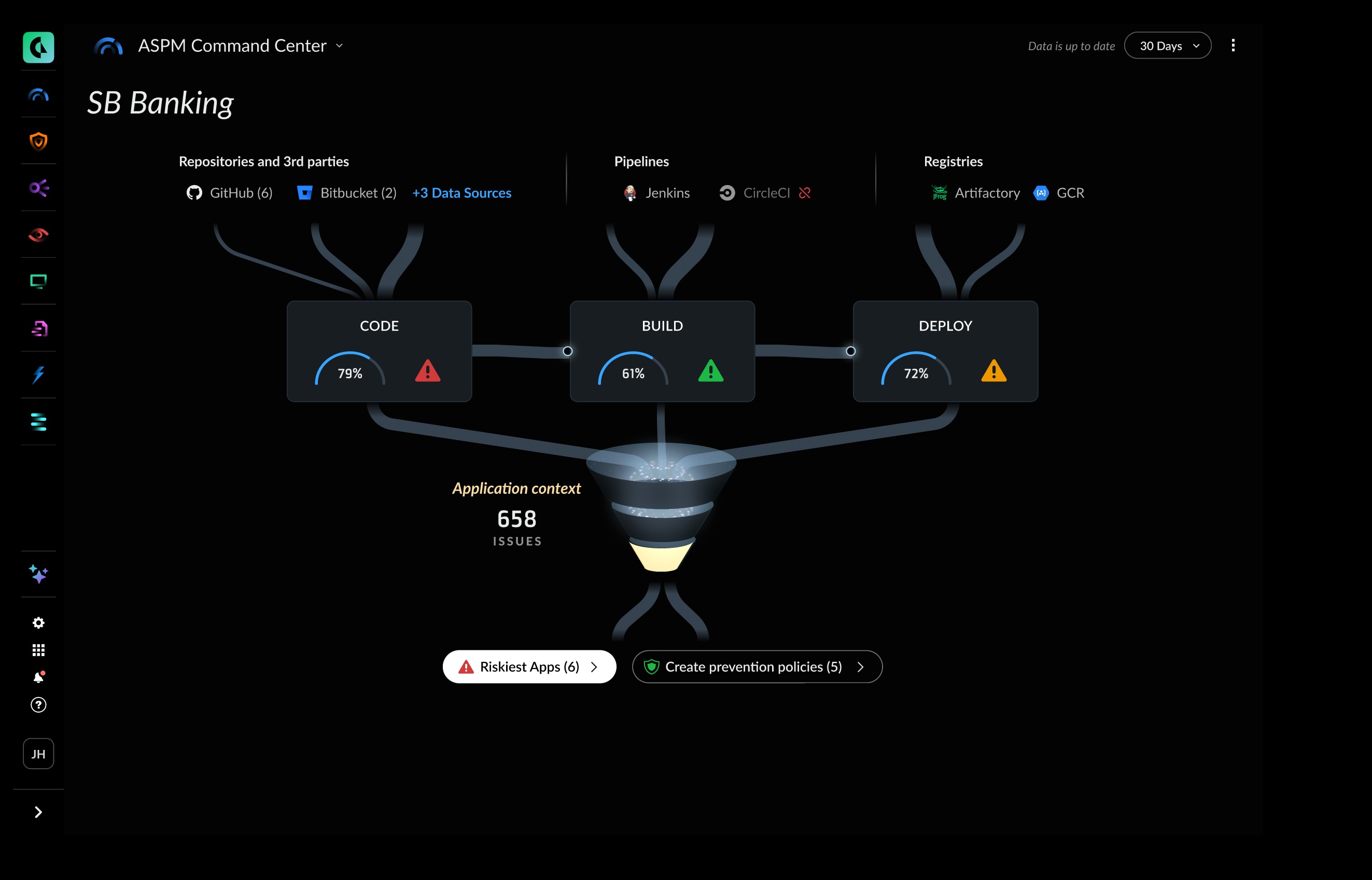
Comprehensive Visibility
Cortex Cloud centralizes visibility by integrating findings across code, build, deploy, and runtime. The platform ingests data from both native scanning tools, third-party scanners and runtime for consistent security across the lifecycle. With Cortex Cloud, AppSec teams can secure the entire engineering ecosystem—code, supply chain, and tools—from a single platform.
Single source of truth
Consolidate AppSec capabilities—from code to runtime—into a single platform to minimize tool console switching and streamline DevSecOps workflows.
Ingest 3rd Party Data
Connect any AppSec tool for centralized visibility and prioritize risk based on comprehensive runtime and application context.
Comprehensive risk context
Bring code, pipeline and runtime context together to manage risks based on probability of exploitation and potential business impact.
Consistent policy enforcement
Apply consistent security policy across the SDLC to ensure that security standards are maintained throughout development and deployment.
Generate a software bill of materials (SBOM)
Generate an SBOM containing open-source packages, libraries and IaC resources, along with associated security issues, to track and understand application risk.