Code to Cloud Visibility
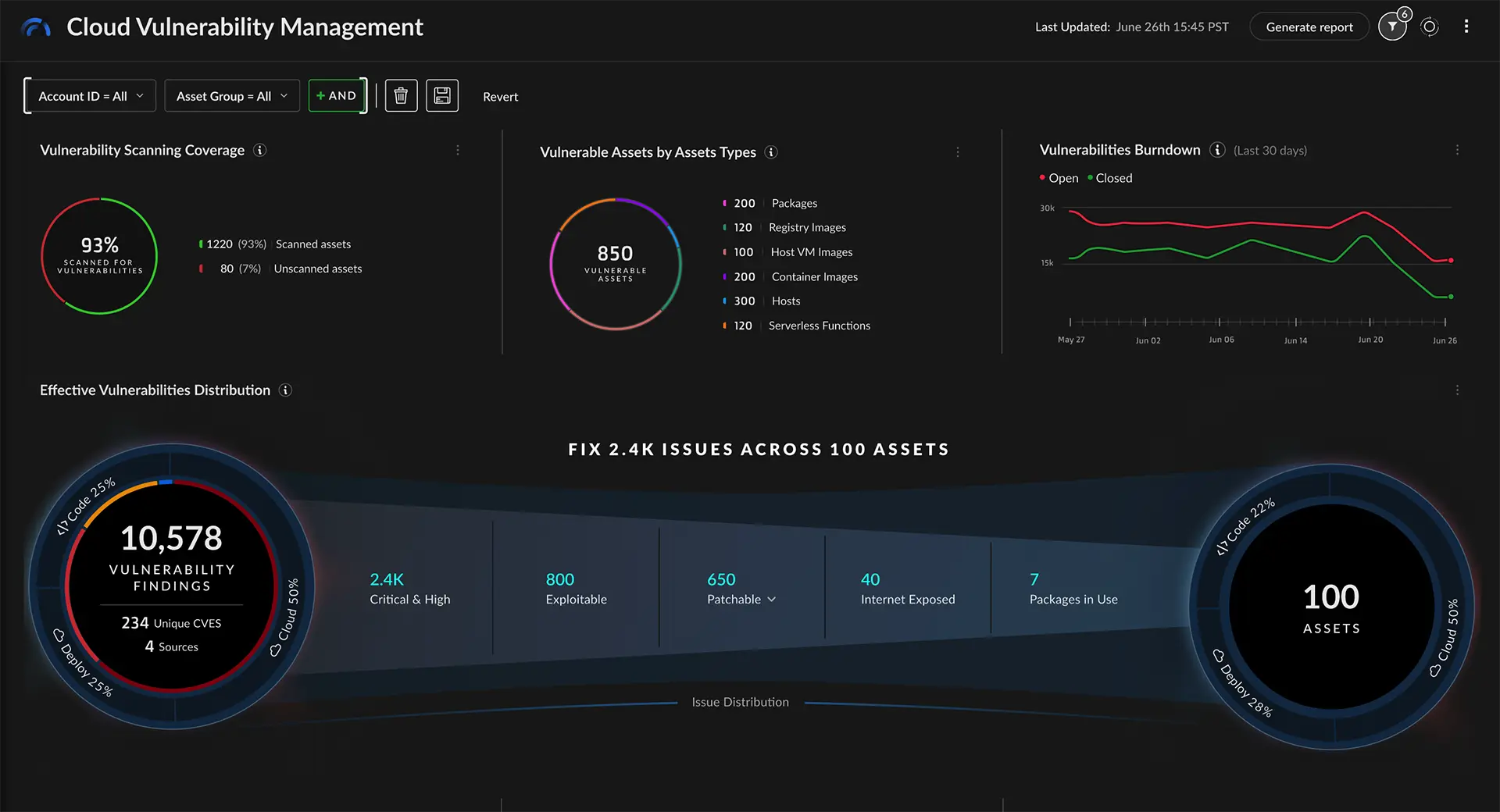
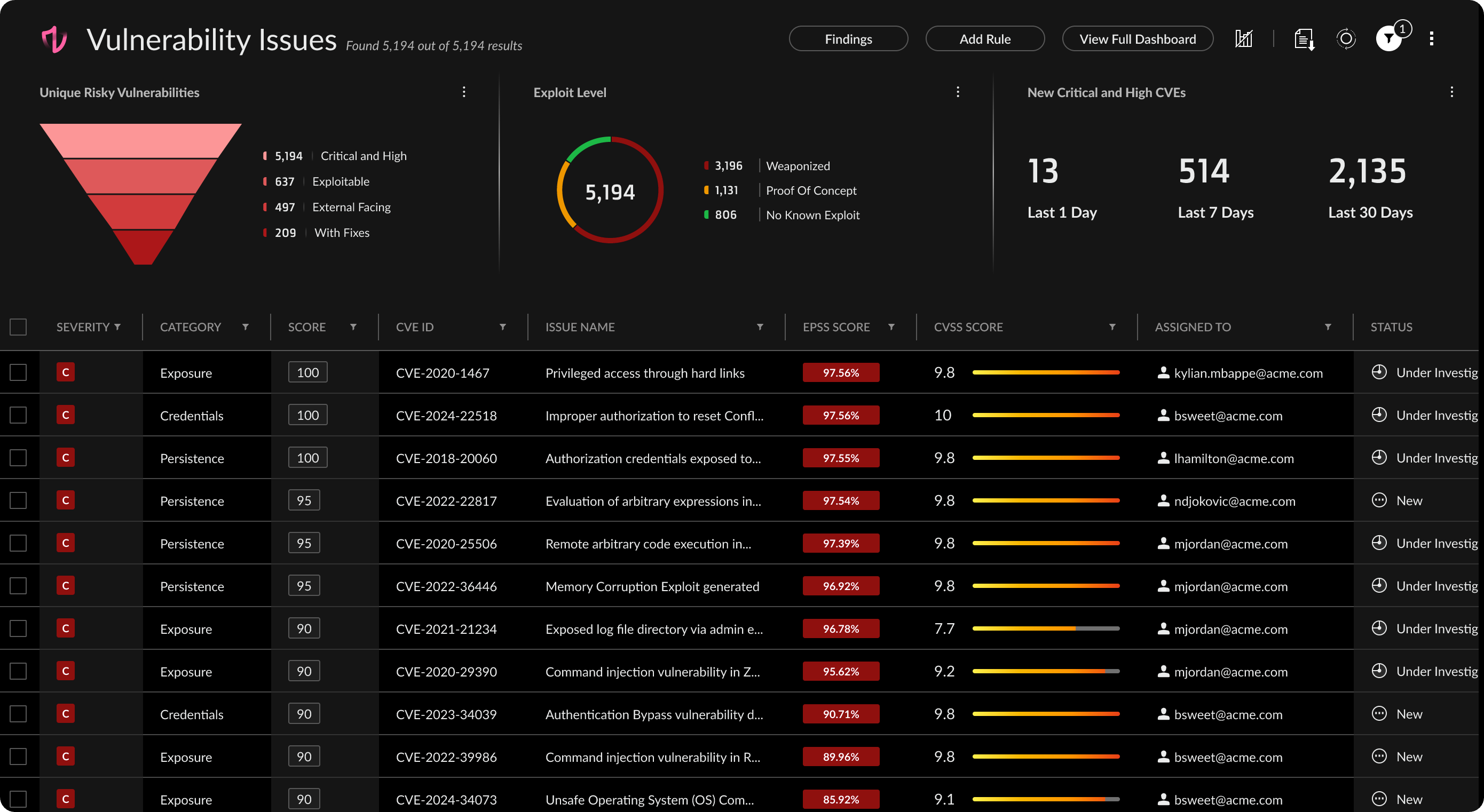
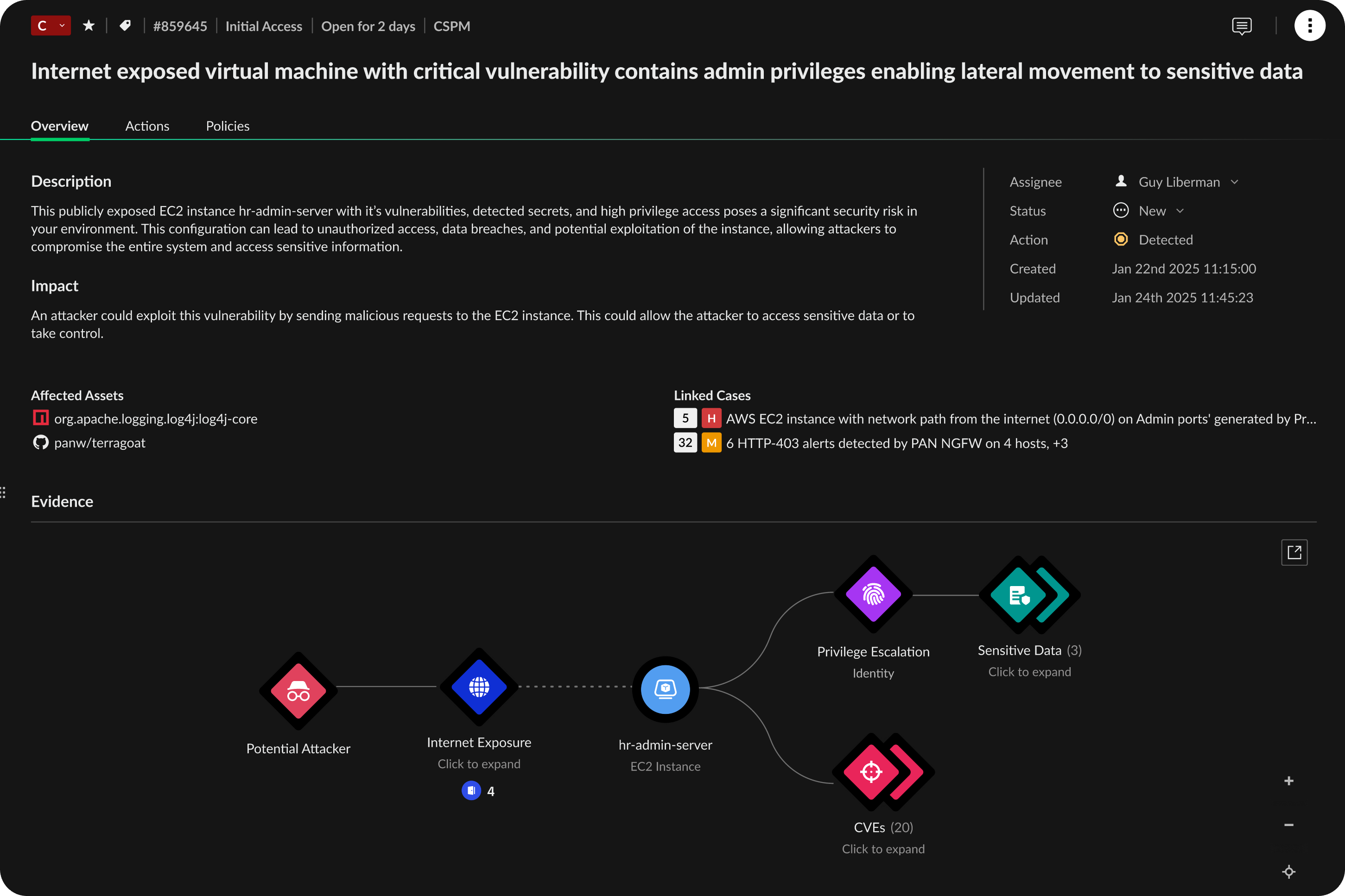
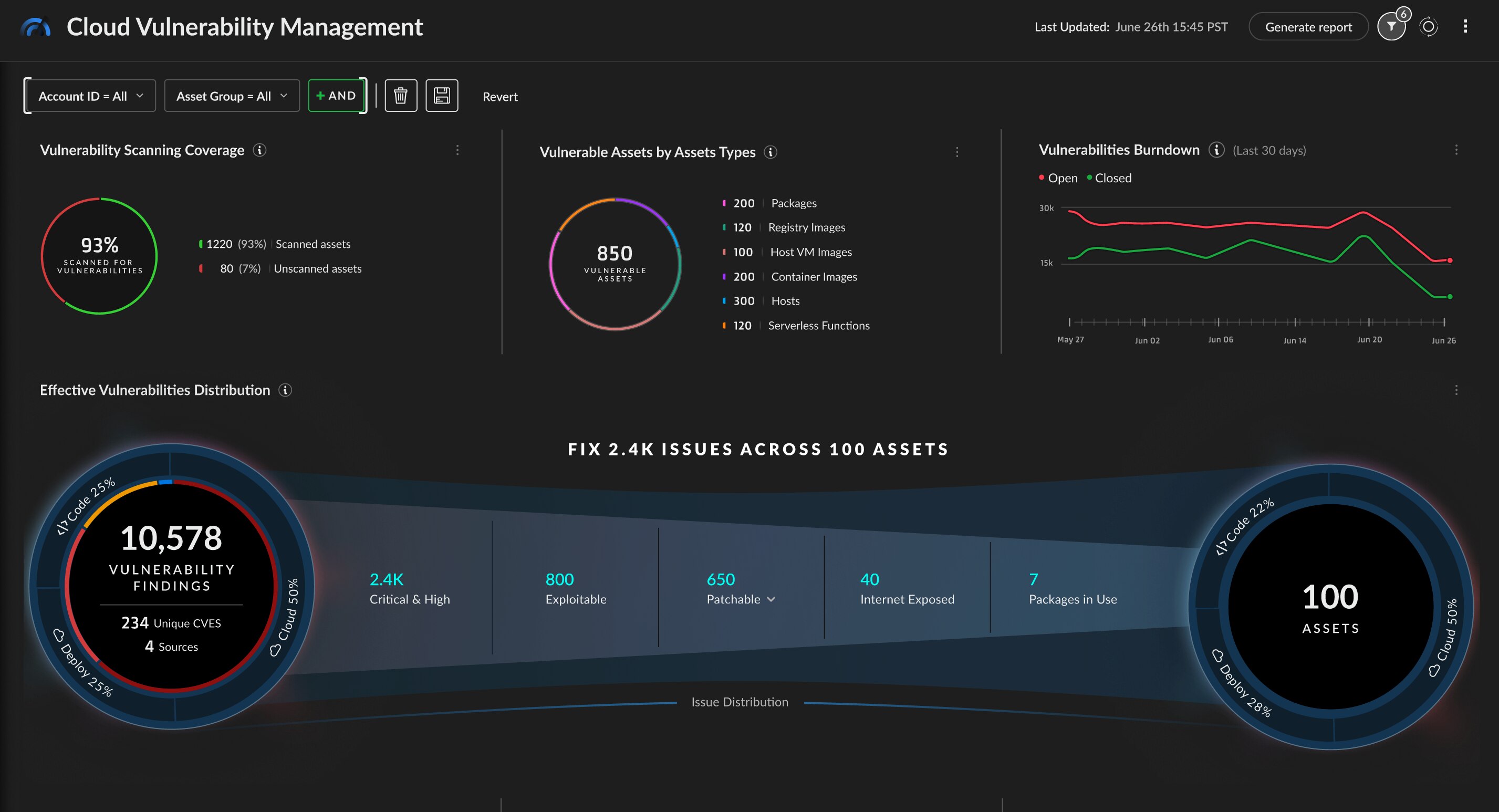
Securing cloud-native applications requires a comprehensive view into vulnerabilities across the application lifecycle. Cortex Cloud delivers a centralized view into vulnerabilities across public cloud, private cloud and on-premises environments for every host, container and serverless function.
Code to cloud visibility
Gain visibility into all vulnerabilities across your environment — source packages, git repos, registries, deployed images, hosts and running applications.
Flexible deployment options.
Gain visibility into vulnerability across virtual machines, containers, kubernetes and serverless functions with agents and agentless scanning.100% continuous coverage for any application in any cloud environment.
Manage risk from a single UI.
Visualize risk across host OS, container images and serverless functions with intelligent risk scoring.