- 1. Endpoint Security Antivirus Management and Deployment
- 2. Endpoint Security Antivirus Support and Compatibility
- 3. Future Proofing and Innovation
- 4. Endpoint Security Antivirus FAQs
- 5. The Importance of Endpoint Security Antivirus Solutions
- 6. Endpoint Antivirus vs. Endpoint Security
- 7. Features of Modern Endpoint Security Antivirus Solutions
- Endpoint Security Antivirus Management and Deployment
- Endpoint Security Antivirus Support and Compatibility
- Future Proofing and Innovation
- Endpoint Security Antivirus FAQs
- The Importance of Endpoint Security Antivirus Solutions
- Endpoint Antivirus vs. Endpoint Security
- Features of Modern Endpoint Security Antivirus Solutions
What is Endpoint Security Antivirus?
- Endpoint Security Antivirus Management and Deployment
- Endpoint Security Antivirus Support and Compatibility
- Future Proofing and Innovation
- Endpoint Security Antivirus FAQs
- The Importance of Endpoint Security Antivirus Solutions
- Endpoint Antivirus vs. Endpoint Security
- Features of Modern Endpoint Security Antivirus Solutions
Endpoint security and antivirus form the cornerstone of protecting business digital assets in today's interconnected world. Endpoint security encompasses the strategies and solutions deployed to secure endpoints, or end-user devices such as desktops, laptops, and mobile devices, from cybersecurity threats. This includes managing antivirus software, firewalls, intrusion detection systems, and more, aiming to detect, analyze, and respond to security incidents.
Antivirus software, a subset of endpoint security, specifically targets malware detection and removal, safeguarding devices against virus attacks. The distinction between endpoint antivirus and endpoint security lies in their scope and functionality, with the former focusing on combating malware and the latter providing a comprehensive security framework.
The Importance of Endpoint Security Antivirus Solutions
As the digital world advances, so do the threats associated with it. Cybercriminals are continuously developing new ways to penetrate computer systems, making it imperative for endpoint antivirus solutions to keep up with the evolution of malware.
The traditional signature-based detection method is no longer enough to combat advanced persistent threats (APTs), zero-day attacks, and polymorphic malware. Endpoint antivirus solutions have evolved to incorporate more sophisticated techniques, such as behavior-based and heuristic analysis, to identify and prevent these threats from infiltrating systems.
Endpoint security antivirus is important for several reasons:
Preventing Malware Infections
Antivirus software is designed to prevent, detect, and remove malware. With the ever-increasing variety and complexity of malware, it's important to have robust antivirus protection to defend against viruses, worms, spyware, ransomware, and other malicious software.
Data Security
Endpoints often store or access sensitive data. Antivirus software helps protect this data from being compromised by malware that could lead to data breaches, loss, or theft.
Network Protection: Infected endpoints can spread malware across a network, leading to widespread damage. Antivirus helps prevent the spread of infections, safeguarding the entire network.
Productivity
Malware infections can slow down systems, cause crashes, and lead to data loss. By protecting endpoints, antivirus software helps maintain productivity by ensuring systems run smoothly.
Compliance: Many industries have regulations that require protection of sensitive data. Antivirus software helps organizations comply with these regulations by securing endpoints against threats that could lead to data breaches.
Cost Savings
Dealing with the aftermath of a malware attack can be costly. Antivirus software helps mitigate these costs by proactively preventing such attacks.
Reputation
A company's reputation can be severely damaged if it falls victim to a cyber attack. Effective antivirus protection helps maintain trust with customers and partners by safeguarding data and systems.
Endpoint Antivirus vs. Endpoint Security
Endpoint antivirus detects and eliminates known threats. Endpoint security offers a wider range of protection, including advanced technologies like machine learning and behavioral analysis to prevent various cyber threats. It provides a more comprehensive approach that includes traditional antivirus capabilities along with firewall management, intrusion prevention, and data encryption.
The key difference is that endpoint security addresses vulnerabilities beyond malware, such as phishing, ransomware, and zero-day exploits, creating a more resilient defense mechanism against modern cyber threats.
Organizations often use both endpoint and antivirus solutions to provide comprehensive endpoint protection within their cybersecurity strategy. Following is a deeper dive into the differences between the two:
Scope of Protection
Endpoint security software provides comprehensive protection for individual devices within a network. It encompasses various security features beyond antivirus, including firewall, intrusion detection and prevention, behavioral analysis, application control, device control, data loss prevention (DLP), and more. Antivirus software has a narrower focus, specializing in detecting and removing known malware threats, such as viruses, Trojans, worms, and spyware.
Features and Capabilities
Endpoint security solutions offer broader security features and capabilities, making them suitable for addressing various threats, including advanced and emerging ones. Antivirus software focuses on signature-based malware detection and removal.
Advanced Threat Protection
Endpoint security solutions are better equipped to handle advanced threats, including zero-day vulnerabilities, targeted attacks, and insider threats. They often include intrusion detection and prevention features, behavioral analysis, and endpoint detection and response (EDR) for advanced threat detection and response. Traditional antivirus solutions may struggle to detect and mitigate advanced threats, particularly those without known signatures.
Additional Security Controls
Endpoint security solutions typically include a range of additional security controls, such as firewall, application control, device control, and data loss prevention. These controls help organizations enforce security policies and mitigate various security risks. Antivirus software centers on malware prevention and removal, usually not including additional security controls like firewall and application control.
Centralized Management
Many endpoint security solutions offer centralized management consoles that allow administrators to configure, monitor, and enforce security policies across endpoints. While some antivirus solutions offer centralized management capabilities, they usually do not provide the same granularity and control as endpoint security platforms.
Features of Modern Endpoint Security Antivirus Solutions
Endpoint security systems are equipped with a variety of features and capabilities designed to protect businesses from a wide range of digital threats. These systems go beyond traditional antivirus measures by incorporating multiple layers of defense to ensure robust protection.
Antivirus and antimalware protection form the core of endpoint security. This fundamental feature scans, detects, and removes malicious software and viruses from devices, safeguarding them against common threats. By continuously updating databases with the latest malware signatures, endpoint security systems can quickly identify and neutralize newly emerging threats.
Modern endpoint security antivirus solutions have evolved significantly, integrating advanced technologies and strategies to combat the ever-growing spectrum of cyber threats. Nowadays, comprehensive features like the following are provided to ensure systems are adequately protected against cyberthreats.
Antivirus and Antimalware Protection
Antivirus and antimalware protection serve as the frontline defense in endpoint security, actively scanning and purging harmful software from devices. These systems leverage real-time scanning to intercept potential threats before they infiltrate the network, coupled with heuristic analysis to predict and counteract evolving malware types not yet cataloged in signature databases. This dual approach ensures that both known viruses and emerging variants are swiftly addressed, minimizing potential damage.
Regular updates to antivirus engines and malware definitions remain critical, enabling the detection of the latest threats and reinforcing the security perimeter. Additionally, integration with cloud-based analytics enhances the detection capabilities, allowing for a more dynamic response to threats as they arise. This integration not only bolsters the system's ability to learn from new threats but also shares intelligence across networks, improving overall security posture.
Advanced Threat Protection
Building on the foundation of antivirus and antimalware tools, advanced threat protection (ATP) systems introduce a more dynamic layer of defense, designed to detect, analyze, and respond to sophisticated attacks that may bypass traditional security measures.
ATP solutions employ a combination of network traffic analysis, behavior-based detection, and sandboxing technologies to identify anomalous activities indicative of advanced persistent threats (APTs) or zero-day exploits. By monitoring endpoints and communications within the network, these systems can quickly isolate and neutralize threats, even in encrypted traffic.
Sandboxing allows potentially dangerous code to execute in a secure, controlled environment, away from the main network, enabling detailed analysis without risking the integrity of the system. This proactive approach not only prevents disruptions but also provides invaluable insights into attack techniques, helping refine ongoing security strategies.
Web and Network Protection
Protecting web and network interfaces is crucial in maintaining robust endpoint security. Antivirus solutions now integrate features that scan and filter incoming internet traffic to thwart web-basedthreats before they infiltrate the network. This includes blocking malicious URLs and phishing sites, which are often the launch points for complex cyberattacks.
Real-time monitoring of network traffic ensures that any unusual data transfer or communication pattern is flagged and analyzed promptly, reducing the risk of data breaches. Employing deep packet inspection, security systems can scrutinize the header and payload of each packet that travels across the network, identifying anomalies that may indicate the presence of malware or an active cyberattack.
This level of scrutiny extends to encrypted traffic as well, where advanced decryption capabilities allow for the inspection of SSL/TLS encrypted communications without compromising the data's security. This comprehensive web and network protection strategy forms a critical barrier against the ever-evolving landscape of cyber threats.
Data Loss Prevention (DLP)
Data loss prevention (DLP) features in endpoint security aim to protect sensitive information from unauthorized access or exfiltration. DLP policies can be configured to control data transfer, encrypt sensitive files, and prevent users from performing risky actions that could lead to data breaches.
Device and Application Control
Device and Application Control safeguards business operations by managing and restricting the use of unauthorized devices and applications. These controls ensure that only approved software runs on network endpoints, significantly reducing the risk of malware infections from rogue applications.
Administrators can enforce policies that block or restrict software based on various criteria, including the publisher's identity, software behavior, and known security vulnerabilities. This capability extends to external devices such as USB drives, which are common carriers of malicious software.
By controlling access to these devices, organizations prevent potential security breaches that could arise from data theft or the introduction of malware into the network. The system also monitors application behavior in real-time, allowing for the immediate detection and containment of actions that deviate from typical patterns, thus maintaining continuous operational security.
Data Encryption and Protection
By transforming readable data into encrypted code, endpoint security antivirus systems ensure that even if data is intercepted during transmission, it remains unintelligible to hackers. Key management practices are essential, as they govern how encryption keys are generated, distributed, stored, and destroyed, thereby enhancing data protection.
Additionally, endpoint security solutions employ various encryption algorithms, each with different strengths and suited to specific types of data. For example, AES (Advanced Encryption Standard) is widely recognized for its resilience and efficiency in securing large volumes of data.
This data encryption capability is seamlessly integrated with device and application control measures, ensuring that all data remains protected both at rest and in transit, maintaining the integrity and confidentiality of business information as it flows across networks.
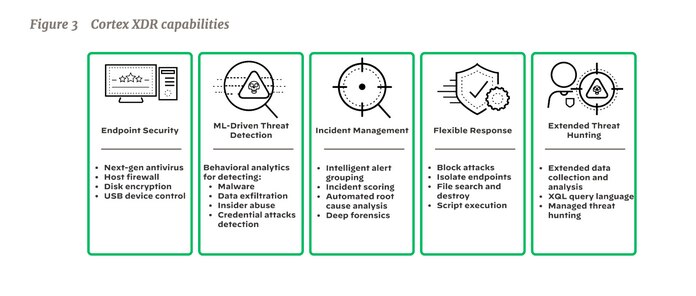
Cortex XDR Capabilities
Cortex XDR Capabilities include advanced threat detection, automated incident response, threat hunting, endpoint detection and response (EDR), network detection and response (NDR), Cloud security
Endpoint Security Antivirus Management and Deployment
Centralized management consoles play a pivotal role in the management and deployment of endpoint security antivirus by allowing IT administrators to oversee and control security measures across all endpoints from a single interface. This centralized approach simplifies the administrative burden and enhances the consistency of security policies applied throughout the organization.
Deployment options and integration capabilities significantly influence the effectiveness of endpoint security systems. Businesses must choose between on-premises, cloud-based, or hybrid deployment models based on their specific security needs, infrastructure, and regulatory compliance requirements.
Integration with existing IT environments is crucial to ensure seamless operation and minimize potential security gaps. Effective integration enables real-time data exchange and threat intelligence sharing, bolstering the overall security posture.
Centralized Management Consoles
Centralized management consoles streamline the oversight of endpoint security by providing IT administrators with a unified platform to monitor, update, and enforce security policies across all devices. These consoles facilitate rapid response to emerging threats by enabling quick updates to antivirus definitions and security protocols directly from a central point of control.
They also allow for detailed tracking of security incidents and system vulnerabilities, which is critical for timely and effective threat mitigation. The ability to remotely configure and manage endpoint security settings reduces the complexity and cost associated with manual administration across multiple devices and locations.
Moreover, centralized consoles support scalability by simplifying the addition of new endpoints as the organization grows, ensuring consistent application of security measures without the need to individually configure each new device. This centralization not only enhances security but also improves operational efficiency by reducing downtime and streamlining administrative tasks.
Deployment Options and Integration
Selecting the right deployment model for endpoint security antivirus is crucial for any business. Options range from on-premises solutions, which offer control over physical servers and direct management of the security infrastructure, to cloud-based services that provide flexibility and scalability without the need for extensive hardware investments. Hybrid models combine both, leveraging on-premises control with the scalability of cloud services.
Integration of antivirus solutions into existing IT environments is equally important. Effective integration ensures that antivirus systems work seamlessly with other security tools like firewalls, intrusion detection systems, and data loss prevention software. This synergy enhances the overall security posture by enabling real-time data sharing and threat intelligence across platforms.
Businesses must ensure that their chosen antivirus solution can integrate smoothly with their current IT setup to maximize protection and minimize potential gaps in security coverage.
Policy Management and Reporting
Effective policy management in endpoint security antivirus systems is essential for maintaining protection across all devices. Administrators must establish clear security policies that dictate the handling of threats and the responsibilities of users. These policies should be easily accessible and regularly updated to reflect the latest cybersecurity practices and threat intelligence.
Reporting mechanisms play a critical role in the ongoing assessment of an antivirus solution’s effectiveness. They provide vital insights into threat patterns, attack types, and the overall health of the IT environment. Detailed reports help in pinpointing vulnerabilities and assessing user compliance with security policies.
For optimal management, reports should be automated and customizable to suit different stakeholder needs, from IT staff to executive management, ensuring all parties are informed and can make data-driven decisions to fortify defenses.
Endpoint Security Antivirus Support and Compatibility
Support and compatibility are critical factors in the effective deployment of endpoint security antivirus solutions. Businesses must ensure that the antivirus software they choose is compatible with all the platforms and devices in their network. This includes everything from traditional desktop computers running various operating systems to mobile devices and IoT devices.
Additionally, the antivirus solution should seamlessly integrate with existing security solutions within the organization. This integration enhances the overall security posture by allowing different tools to share information and respond more effectively to threats.
Supported Platforms and Devices
Endpoint security antivirus software must support a wide array of operating systems, including Windows, macOS, Linux, and increasingly popular mobile platforms such as Android and iOS. This broad compatibility ensures that businesses can protect all endpoints, regardless of the underlying technology.
For organizations employing IoT devices, it's crucial to select antivirus solutions that cater to less common operating systems like ARM-based architectures or proprietary platforms used in specialized equipment.
The software should offer flexible deployment options to cover both on-premises and remote devices, adapting to various network configurations and ensuring consistent protection across all points of entry.
Compatibility with virtual environments and cloud infrastructures is also essential, allowing businesses to secure virtual machines and cloud-based applications effectively. This comprehensive platform support prevents gaps in security coverage, crucial for defending against sophisticated cyber threats targeting diverse and dynamic digital ecosystems.
Integration with Other Security Solutions
Seamless integration with existing security frameworks is critical for enhancing the effectiveness of endpoint security antivirus solutions. By ensuring compatibility with other security tools such as firewalls, intrusion detection systems (IDS), and security information and event management (SIEM) systems, businesses can create a multi-layered defense against cyber threats. This integration allows for the sharing of threat intelligence and security alerts, enabling quicker detection, analysis, and response to potential vulnerabilities or attacks.
For instance, when an antivirus detects a new threat, it can immediately inform the SIEM system, which then correlates this information with data from other sources to assess the threat's impact and scope more accurately. Collaborative defense mechanisms like these significantly reduce the time to respond to threats, minimizing potential damage.
Additionally, compatibility with network security tools ensures that security policies are uniformly enforced across all devices, maintaining a high level of protection without disrupting business operations.
Future Proofing and Innovation
Future-proofing in the realm of endpoint security necessitates a proactive approach to innovation, especially as cyber threats evolve in complexity and frequency.
Companies must prioritize adapting to emerging threats by staying abreast of the latest cybersecurity trends and threat intelligence. This involves not only updating and patching systems but also training employees to recognize and respond to new types of cyberattacks.
Equally critical is the focus on research and development. Investing in cutting-edge technologies and methodologies enhances a business’s ability to anticipate and mitigate potential vulnerabilities before they can be exploited.
By integrating advanced predictive analytics and artificial intelligence, organizations can refine their threat detection capabilities and improve their overall security posture, ensuring that their defenses evolve in tandem with the shifting digital landscape.