- 1. Why Attackers Use Lateral Movement
- 2. How Do Lateral Movement Attacks Work?
- 3. Stages of a Lateral Movement Attack
- 4. Techniques Used in Lateral Movement
- 5. Detection Strategies for Lateral Movement
- 6. Tools to Prevent Lateral Movement
- 7. Best Practices for Defense
- 8. Recent Trends in Lateral Movement Attacks
- 9. Industry-Specific Challenges
- 10. Compliance and Regulatory Requirements
- 11. Financial Impact and ROI Considerations
- 12. Common Mistakes to Avoid
- 13. Lateral Movement FAQs
- Why Attackers Use Lateral Movement
- How Do Lateral Movement Attacks Work?
- Stages of a Lateral Movement Attack
- Techniques Used in Lateral Movement
- Detection Strategies for Lateral Movement
- Tools to Prevent Lateral Movement
- Best Practices for Defense
- Recent Trends in Lateral Movement Attacks
- Industry-Specific Challenges
- Compliance and Regulatory Requirements
- Financial Impact and ROI Considerations
- Common Mistakes to Avoid
- Lateral Movement FAQs
What Is Lateral Movement?
- Why Attackers Use Lateral Movement
- How Do Lateral Movement Attacks Work?
- Stages of a Lateral Movement Attack
- Techniques Used in Lateral Movement
- Detection Strategies for Lateral Movement
- Tools to Prevent Lateral Movement
- Best Practices for Defense
- Recent Trends in Lateral Movement Attacks
- Industry-Specific Challenges
- Compliance and Regulatory Requirements
- Financial Impact and ROI Considerations
- Common Mistakes to Avoid
- Lateral Movement FAQs
Lateral movement is a technique used by cyber attackers use to navigate through a compromised network or system. They move from one host or device to another in search of valuable data, higher privileges, or critical assets. Unlike initial access, which involves breaking into a system, lateral movement is about expanding control within the environment.
Lateral movement is dangerous because attackers can escalate their attack from an initial compromise to widespread network infiltration. Detecting lateral movement is challenging since attackers often mimic legitimate user behavior, making it a key focus in cybersecurity defense strategies and network monitoring solutions.
Why Attackers Use Lateral Movement
Lateral movement is a means to an end, which varies depending on the cybercriminal. By moving laterally across an environment undetected, attackers can perpetrate and facilitate many types of malicious activities. The following are examples of what an attacker can do with lateral movement capabilities.
- Escalate access privileges
- Exfiltrate high-value data, such as intellectual property, banking information, personally identifiable information (PII), credit card data, and sensitive communications.
- Identify system vulnerabilities for future or expanded attacks
- Steal user account credentials
- Support sophisticated cyberattacks, such as advanced persistent threats (APTs)
How Do Lateral Movement Attacks Work?
Lateral movement attacks begin with an initial breach, after which the attacker moves across internal systems. These attacks can be conducted manually, with the threat actor navigating the network and taking direct actions, or through a fileless malware approach, such as a worm that spreads automatically.
During the lateral movement process, the attacker can observe the security measures within the environment. If detected, attackers often establish backdoors that allow them to re-enter the network after a security incident response has taken place to remove them. In doing so, they can use the information they previously gathered to refine their tactics, enabling them to evade detection upon reentry.
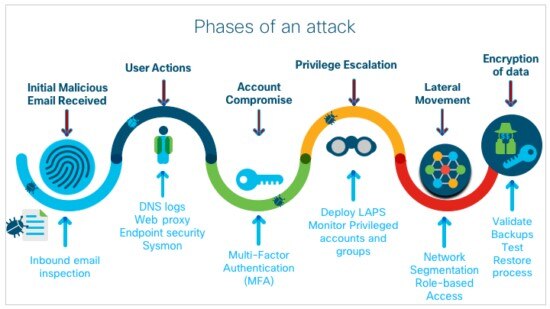
Stages of a Lateral Movement Attack
Although lateral movement attacks are motivated by different objectives, most follow a common framework. They involve several deliberate steps that allow attackers to move within a network to reach high-value assets or critical systems.
External Reconnaissance
Before executing a lateral movement attack, threat actors explore the network from the outside to identify vulnerabilities. This phase includes external network scans, password dumps, social engineering, and researching public records to gather detailed information about the organization's systems and security.
Infection and Compromise
A lateral movement attack begins by compromising a point of entry. Usually, this is done by infecting a system with malware that connects to a threat actor's command-and-control server, which is used to issue undetected instructions to the infected machine.
Internal Reconnaissance Using Lateral Movement
Once inside the network, threat actors start reconnaissance to determine the next best steps for the lateral movement attack. During this phase, they learn as much as possible about the internal systems. This phase starts with assessing what the compromised device has access to and, if they have compromised a user's account, what privileges the user has.
After the initial assessment, the attacker starts exploring and mapping the network, devices, and users from the inside. This allows them to determine host naming conventions and network hierarchies, identify operating systems, locate potential payloads, and gather intelligence to help determine the most effective paths for lateral movement, achieving objectives, and evading detection.
Credential Theft
Attackers must gather login credentials to begin moving laterally. Several methods are commonly used for credential theft. Tools like keyloggers and Windows Credential Editor are used for credential dumping. Alternatively, threat actors use social engineering and brute-force attacks to steal credentials.
Privilege Escalation
Privilege escalation is where lateral movement gains momentum, and the potential threat increases significantly. Threat actors use several tactics to enhance their access privileges. The following section details several common approaches: internal spear phishing, pass-the-hash or pass-the-ticket attacks, and PowerShell attacks.
Executing Objectives and Covering Tracks
The final step in a lateral movement attack is to execute the objectives. Since many of these attacks are persistent, multiple attacks often spread over some time. Threat actors cover their tracks to evade detection and ensure they can continue conducting malicious activities.
Among the tactics used to remove traces of their presence are:
- Deleting logs
- Using rootkits
- Modifying timestamps
These steps are meant to make it harder for security teams to detect their presence, know what they did, and identify the root cause, as the ploy will likely be used again if it is successful.
Techniques Used in Lateral Movement
Threat actors use lateral movement techniques to navigate a compromised network after gaining initial access. The following examples demonstrate how attackers exploit vulnerabilities to achieve their objectives.
Internal Spear Phishing
After an attacker has access to a legitimate user's account, they use spear phishing attacks on specific people or groups within the organization to obtain their credentials and access codes. Spear phishing is highly effective because the targets trust the account sending the malicious messages. This tactic is one of the ways that attackers escalate their privileges to expand their access.
Mimikatz
Mimikatz is a tool initially developed to demonstrate weaknesses in Windows systems. Like many powerful tools, It has been co-opted by threat actors who use it to collect users' credentials from the memory of Windows computers. Attackers use Mimikatz to extract plaintext passwords, hashes, PIN codes, and Kerberos tickets.
Pass-the-Hash (PtH) Attacks
Pass-the-hash attacks allow threat actors to authenticate and gain access without having a user's password. To do this, the attacker captures a valid password hash from one system and uses it to authenticate on other systems with the hash rather than a plaintext password.
Pass-the-Ticket (PtT) Attacks
With pass-the-ticket attacks, threat actors steal tickets from the default Windows authentication protocol, Kerberos. Once the attacker has the ticket, they can access the system's domain controller and create a "golden ticket," which allows them to impersonate any account. These golden tickets remain valid indefinitely, even after a password reset, making them a powerful and dangerous threat when in the hands of a cybercriminal.
PowerShell Attacks
After accessing internal systems, attackers use Microsoft's PowerShell scripting language to execute commands, change configurations, steal passwords, run malicious scripts, bypass security controls, and move laterally within a network. PowerShell helps attackers evade detection because it is a trusted tool and can be used without writing files to disk.
PsExec
PsExec is a remote administration tool that allows users to execute commands on remote systems without installing software. Attackers exploit this capability to run scripts and launch processes on multiple computers to facilitate lateral movement.
RDP (Remote Desktop Protocol)
The Remote Desktop Protocol (RDP) is a proprietary protocol co-opted by cybercriminals. RDP is used to remotely control systems within the network, enabling attackers to execute commands and run applications to support their malicious activities.
Remote Services Exploitation
Once attackers have gained entry to a system, they can probe for vulnerabilities and misconfigurations in remote services (e.g., remote communication and collaboration tools like Zoom). These services can be hacked and used as a hopping-off point to gain access to other internal resources.
Secure Shell (SSH) Hijacking
Attackers hijack SSH sessions, which enable remote access for macOS and Linux systems. This tactic allows attackers to deploy a legitimate user's SSH session laterally to infect other users or systems through the encrypted SSH tunnel.
Windows Admin Shares
Windows admin shares are hidden network shares automatically created by Windows to enable system administrators to access file systems and perform administrative functions remotely. Attackers steal Windows admin shares and exploit them to manage and access other hosts, expediting and facilitating their lateral movement.
Detection Strategies for Lateral Movement
As with all cybersecurity, awareness plays a vital role in defense. Remaining vigilant for signs of lateral movement helps security teams prevent or quickly respond to active lateral movement. Several common indicators of lateral movement are:
- Anomalous login patterns include logging in at unusual times, accessing systems outside of typical workflows, and logging in from unexpected geographic locations.
- Detection of known tools for network discovery, credential dumping, or privilege escalation.
- Increased alerts from intrusion detection systems (IDS) and intrusion prevention systems (IPS).
- Multiple login attempts across systems, mainly when the same credentials are used on various systems (i.e., credential stuffing).
- Unexpected or unusual network traffic, such as substantial data transfers, communications between systems with no prior relationship, or spikes in network traffic.
- There has been unusual use of administrative tools from unexpected endpoints, such as the use of remote desktop protocols from suspicious external endpoints.
Although it is notoriously elusive, lateral movement can be detected. The following are several proven strategies and tools that can help security teams identify suspicious activities indicative of lateral movement:
- Map lateral movement paths (LMPs)
- Leverage analytics and reporting tools
- Investigate and analyze user and entity behavior
- Monitor all network traffic and devices, including BYOD
- Investigate abnormal administrative tasks and file sharing
- Identify port scans and abnormal network protocols
- Inspect log files
- Regularly review service account and privileged account activity
Tools to Prevent Lateral Movement
The following are examples of security tools proven to be highly effective in combatting lateral movement attacks. The most successful defenses combine these tools to create a powerful multi-layered approach preventing lateral movement.
Endpoint Detection and Response (EDR)
EDR solutions monitor online and offline endpoints to enable real-time detection of cyberattacks that lead to lateral movement attacks. In addition, historical endpoint events can be used to identify trends and optimize security systems to prevent lateral movement.
Identity and Access Management (IAM)
IAM helps security teams limit potential damage from lateral movement by tightly controlling users’ access. This includes multi-factor authentication, which stops attackers from accessing systems even if users’ credentials are compromised.
Intrusion Detection Systems and Intrusion Prevention Systems (IDS/IPS)
IDS tools monitor network traffic and alert security teams when suspicious activities, such as unauthorized access or policy violations, are detected. IPS can automatically block threats and initiate incident response tactics when an issue is identified.
User and Entity Behavior Analytics (UEBA)
Although elusive, lateral movement attacks do result in unusual behaviors. UEBA solutions leverage machine learning and advanced analytics to detect abnormal behavior by users and systems within a network that could indicate lateral movement.
Best Practices for Defense
Coupling security tools with best practices further enhances organizations’ security posture and helps prevent lateral movement. The best practices noted below are several of the many steps that organizations can take to avoid or minimize an attacker’s undetected dwell time and the consequences of lateral movement.
Backup and Encrypt Critical Data and Systems
A robust backup system minimizes the damage that can be done if an attacker breaches security and moves laterally across an organization’s digital systems. Backups of sensitive information should always be encrypted to ensure they are protected even during data exfiltration.
“Golden images” of critical systems (e.g., operating systems and software applications) should also be maintained and stored securely to restore compromised systems quickly.
It is also highly recommended that copies of all critical backups be stored offline, making them inaccessible to attackers moving laterally across systems.
Conduct Threat Hunting for Advanced Threats
Threat hunting is critical for identifying and stopping lateral movement associated with advanced persistent threats (APTs). Since lateral movement often goes undetected, human threat hunters are needed in conjunction with security tools.
These expert security analysts adopt the mindset of a threat actor and work on the assumption that attackers have already successfully breached systems.
Threat-hunting frameworks guide deep investigations. TaHiTI (Targeted Hunting integrating Threat Intelligence framework) and the MITRE PRE-ATT&CK and MITRE ATT&CK frameworks are the most widely used.
Enforce the Principle of Least Privilege (PoLP)
Employ the principle of least privilege (PoLP) for access controls to minimize exposure by limiting users' access to only what they need to perform their tasks. PoLP gives users the access they need when they need it but eliminates overprovisioning, which increases the potential scale of lateral movement if an account is compromised.
Implement Password Management Policies
Password management at the user and admin level helps prevent user account exploitation for lateral movement attacks. Password controls should include strong and unique passwords across all privileged systems and accounts. In addition, administrators should follow protocols for account management hygiene, such as updating the KRBTGT password regularly (i.e., implementing Kerberos, the default Microsoft Windows authentication protocol).
Install Software Updates and System Patches Regularly
Malware exploits software and system vulnerabilities to enable lateral movement and provide a cyberattack's initial entry point. To eliminate this attack vector, all software, operating systems, and firmware should be updated regularly, and security patches should be installed as soon as possible.
Segment Networks
Network segmentation plays a critical role in mitigating the potential threat of lateral movement by dividing networks into smaller segments with limited access based on PoLP. Microsegmentation takes this step further by creating granular segments that isolate workloads and sensitive data. In addition to restricting an attacker’s lateral movement area, network segmentation and micro-segmentation make identifying unusual behavior and traffic patterns associated with cyber attacks easier.
Use Allowlisting
Create allowlists of software approved for installation, and establish and enforce IT policies that require any application not on the allowlist to be carefully scanned for malware. As demonstrated by a number of cyber attacks (e.g., NotPetya), legitimate software can be compromised and infected with malware that enables lateral movement.
Recent Trends in Lateral Movement Attacks
The landscape of lateral movement attacks has evolved significantly in recent years, with attackers adopting more sophisticated and stealthy approaches. Supply chain compromises have emerged as a preferred initial access vector, with attackers targeting managed service providers and software vendors to simultaneously gain access to multiple downstream customers. This trend was exemplified by the notorious SolarWinds attack, which affected thousands of organizations globally.
Machine learning and artificial intelligence are increasingly being weaponized for lateral movement. Attackers use AI-powered tools to analyze network patterns and mimic legitimate user behavior more effectively. These tools can automatically identify the most promising paths for lateral movement while minimizing detection risks.
Industry data shows a concerning trend in dwell time—the duration attackers remain undetected within networks. According to recent cybersecurity reports, the average dwell time for lateral movement attacks has decreased to 21 days, indicating that attackers are becoming more efficient in achieving their objectives. However, sophisticated state-sponsored attacks often persist for several months before detection.
Regarding impact, lateral movement attacks have shown a 47% increase in successful data exfiltration compared to previous years. Organizations report more significant data breaches, with an average of 1.5 times more systems compromised per incident than in previous years.
Industry-Specific Challenges
Healthcare organizations face unique challenges in preventing lateral movement due to their complex networks of connected medical devices and the critical nature of their operations. Legacy medical equipment often runs on outdated operating systems that cannot be easily patched or updated, creating permanent vulnerabilities that attackers can exploit. Additionally, the necessity for immediate access to patient data often leads to security compromises in access controls.
Financial services institutions must contend with sophisticated attackers targeting high-value trading systems and payment processing networks. The interconnected nature of economic systems, including connections to third-party service providers and global payment networks, creates numerous potential paths for lateral movement. These organizations typically process millions of transactions daily, making it challenging to distinguish malicious lateral movement from legitimate activity.
Government agencies face persistent threats from state-sponsored actors who utilize lateral movement techniques in long-term espionage campaigns. These organizations must protect classified information while maintaining interoperability between agencies and external partners. The challenge is compounded by strict procurement processes that can delay the implementation of new security tools.
Critical infrastructure protection presents unique challenges due to the convergence of IT and operational technology (OT) networks. Attackers targeting these systems often use lateral movement to bridge the gap between IT and OT networks, potentially gaining control of industrial control systems. The consequences of such attacks can be severe, potentially affecting essential services and public safety.
Compliance and Regulatory Requirements
Global Data Protection Regulation, or GDPR has significant implications for lateral movement detection and response. Organizations must maintain detailed audit trails of data access and movement, with the ability to demonstrate compliance within 72 hours of a breach detection. The regulation requires organizations to implement appropriate technical measures to ensure data security, including network segmentation and access controls that limit lateral movement opportunities.
Health Insurance Portability and Accountability Act, or HIPAA compliance requires healthcare organizations to implement technical safeguards restricting lateral movement capabilities. This includes maintaining detailed access logs, implementing role-based access control, and ensuring that protected health information (PHI) is appropriately segregated and secured. Organizations must be able to track and report any unauthorized access or movement of PHI within their networks.
Payment Card Industry Data Security Standard, or PCI DSS guidelines specifically address lateral movement risks in cardholder data environments. Requirements include maintaining network segmentation, implementing strict access controls, and regularly testing security systems and processes. Organizations must maintain clear boundaries between cardholder data environments and other network segments, with controls to prevent unauthorized lateral movement between these zones.
SOX (Sarbanes-Oxley Act) compliance requires public companies to maintain effective internal controls over financial reporting systems. This includes implementing controls that prevent unauthorized lateral movement within financial systems and maintaining audit trails of all system access and changes. Organizations must demonstrate that they can detect and prevent unauthorized access to financial systems and data.
To learn more about the SEC’s 2023 cybersecurity disclosure rules and how CISO’s can prepare, read our e-book “A New Regulatory Era for Cybersecurity”.
Financial Impact and ROI Considerations
The financial impact of lateral movement attacks can be substantial, with recent studies indicating an average breach cost of $4.88 million. This figure increases significantly when considering successful lateral movement incidents, where attackers gain access to multiple systems and sensitive data. Organizations in regulated industries face additional costs related to compliance violations and mandatory reporting requirements.
Investment in lateral movement prevention typically requires a multi-layered approach. Organizations should expect to invest between 10% and 15% of their IT budget in security measures, with approximately 30% allocated to preventing and detecting lateral movement. This includes investments in technology, personnel, and training.
Cyber insurance providers are increasingly scrutinizing organizations' capabilities to detect and prevent lateral movement when determining coverage and premiums. Organizations with robust security controls and demonstrated ability to detect lateral movement often qualify for lower premiums, while those with inadequate controls may face higher rates or coverage limitations.
Recovery costs following a successful lateral movement attack can be substantial. Beyond the immediate incident response costs, organizations must often invest in system remediation, security improvements, and reputation management. The average time to fully recover from a sophisticated lateral movement attack is 280 days, with associated costs accumulating throughout this period.
Common Mistakes to Avoid
Organizations frequently make critical errors in their approach to preventing lateral movement. A common mistake is focusing solely on perimeter security while neglecting internal network monitoring and segmentation. This "hard shell, soft center" approach leaves organizations vulnerable once an attacker gains initial access.
Configuration oversights often create opportunities for lateral movement. These include using default passwords for service accounts, failing to segment networks properly, and maintaining overly permissive access controls. Organizations frequently overlook the importance of regular security assessments and penetration testing to identify these misconfigurations before they can be exploited.
Security gaps frequently arise from incomplete implementation of security controls. For example, organizations may implement multi-factor authentication, or MFA, for external access but still need to require it for lateral movement between internal systems. Similarly, network segmentation is often implemented inconsistently, exposing critical systems to lateral movement through less-protected segments.
Response mistakes can compound the impact of lateral movement attacks. Common errors include failing to properly scope the compromise, rushing to restore systems without fully understanding the attack path, and not implementing proper controls to prevent reinfection. Organizations often focus on removing the immediate threat without addressing the vulnerabilities that enabled the lateral movement.
Lateral Movement FAQs
- APT29 (Cozy Bear)—used lateral movement techniques in Russian state-sponsored cyber-espionage operations targeting U.S. government agencies and corporations.
- Maze ransomware attack—used lateral movement techniques to access multiple systems within victim networks, exfiltrating data before deploying ransomware to encrypt the systems.
- NotPetya—leveraged lateral movement techniques to propagate through networks, causing extensive damage and disruption to critical infrastructure, primarily in Ukraine.
- Operation Aurora—employed lateral movement techniques to infiltrate and steal intellectual property from Google and other high-profile companies.
- SolarWinds supply chain attack—used lateral movement techniques to target high-profile government and corporate networks.
- WannaCry ransomware attack—spread laterally across networks, encrypting data and demanding ransom payments.
