- 1. 3 Main Matrices of the MITRE ATT&CK Framework
- 2. Key Components of the MITRE ATT&CK Framework
- 3. Using the MITRE ATT&CK Framework
- 4. Implementing the MITRE ATT&CK Framework
- 5. MITRE ATT&CK Tools and Resources
- 6. Comparing MITRE ATT&CK to Other Models
- 7. Benefits of MITRE ATT&CK Framework
- 8. MITRE ATT&CK for Different Technologies
- 9. What Is MITRE Engenuity?
- 10. What are MITRE Engenuity ATT&CK Evaluations?
- 11. MITRE ATT&CK for CISOs
- 12. History and Evolution of the MITRE ATT&CK Framework
- 13. More Information on MITRE ATT&CK
- 14. The MITRE ATT&CK Framework and Cortex XDR
- 15. MITRE ATT&CK FAQs
- 3 Main Matrices of the MITRE ATT&CK Framework
- Key Components of the MITRE ATT&CK Framework
- Using the MITRE ATT&CK Framework
- Implementing the MITRE ATT&CK Framework
- MITRE ATT&CK Tools and Resources
- Comparing MITRE ATT&CK to Other Models
- Benefits of MITRE ATT&CK Framework
- MITRE ATT&CK for Different Technologies
- What Is MITRE Engenuity?
- What are MITRE Engenuity ATT&CK Evaluations?
- MITRE ATT&CK for CISOs
- History and Evolution of the MITRE ATT&CK Framework
- More Information on MITRE ATT&CK
- The MITRE ATT&CK Framework and Cortex XDR
- MITRE ATT&CK FAQs
What is MITRE ATT&CK?
- 3 Main Matrices of the MITRE ATT&CK Framework
- Key Components of the MITRE ATT&CK Framework
- Using the MITRE ATT&CK Framework
- Implementing the MITRE ATT&CK Framework
- MITRE ATT&CK Tools and Resources
- Comparing MITRE ATT&CK to Other Models
- Benefits of MITRE ATT&CK Framework
- MITRE ATT&CK for Different Technologies
- What Is MITRE Engenuity?
- What are MITRE Engenuity ATT&CK Evaluations?
- MITRE ATT&CK for CISOs
- History and Evolution of the MITRE ATT&CK Framework
- More Information on MITRE ATT&CK
- The MITRE ATT&CK Framework and Cortex XDR
- MITRE ATT&CK FAQs
MITRE ATT&CK is a cornerstone framework that comprehensively understands cyber adversary tactics and techniques. Originating from the MITRE Corporation, this globally recognized knowledge base is an invaluable tool for cybersecurity professionals aiming to fortify their defenses against sophisticated cyber threats.
At its core, MITRE ATT&CK catalogs an extensive array of tactics, techniques, and procedures (TTPs) employed by cyber adversaries, providing a structured approach to cyber threat modeling and defense strategy development.
The framework's architecture is designed ingeniously around various tactics that illustrate how adversaries achieve their objectives within a target network. This hierarchical structure helps defenders mitigate techniques that pose significant environmental risks.
MITRE ATT&CK's dynamic nature ensures the knowledge base stays relevant and up-to-date, providing actionable intelligence to enhance organizations' security posture. By integrating MITRE ATT&CK, professionals can develop effective and resilient defenses against the ever-changing landscape of cyber warfare.
It's important to note that the MITRE ATT&CK framework continuously evolves, and new updates or changes may be introduced. For the most up-to-date information, it's always a good idea to refer to the official MITRE ATT&CK website (https://attack.mitre.org/).
3 Main Matrices of the MITRE ATT&CK Framework
The three main matrices of the MITRE ATT&CK Framework are the Enterprise Matrix, Mobile Matrix, and ICS (Industrial Control Systems) Matrix. Each matrix serves as a roadmap, guiding cybersecurity professionals through the complex landscape of adversary behaviors and attack patterns specific to different environments..
Enterprise Matrix
The Enterprise matrix, the most comprehensive among the three, focuses on tactics and techniques that adversaries use against Windows, macOS, and Linux systems. It outlines a variety of tactics, from initial access and execution to command and control and exfiltration, providing a granular view of potential attack vectors within corporate networks. This matrix is instrumental for organizations in identifying vulnerabilities, enhancing detection capabilities, and fortifying their defenses against sophisticated cyber threats.
Mobile Matrix
Transitioning to the Mobile matrix, the emphasis shifts to threats targeting iOS and Android platforms. This matrix addresses unique mobile-specific concerns, such as exploiting operating system features or apps to gain unauthorized access and information. It is an essential tool for understanding the evolving tactics used in mobile environments, helping security teams develop robust strategies for protecting sensitive data on mobile devices.
ICS Matrix
The ICS matrix highlights cyber threats within industrial environments where operational technology (OT) is prevalent. It highlights adversaries' tactics and techniques to disrupt, control, or damage industrial processes. This matrix is crucial for safeguarding critical infrastructure, as it provides insights into the intersection of cyber and physical security, enabling the implementation of effective countermeasures against threats to industrial operations.
Discover how the MITRE ATT&CK Matrix categorizes tactics, techniques and procedures used by attackers: What is the MITRE ATT&CK Matrix?
Key Components of the MITRE ATT&CK Framework
The MITRE ATT&CK framework is a critical resource in cybersecurity. It provides a comprehensive matrix of threat actors' tactics, techniques, and procedures. Built on the security community's shared knowledge, it helps organizations understand and mitigate rapidly evolving cyber threats, enhancing their security posture.
MITRE Tactics
| Tactic | Attacker(s) Objective |
| 1. Reconnaissance | Gather information they can use to plan future operations |
| 2. Resource Development | Establish resources they can use to support operations |
| 3. Initial Access | Get into your network |
| 4. Execution | Run malicious code |
| 5. Persistence | Maintain their foothold |
| 6. Privilege Escalation | Gain higher-level permissions |
| 7. Defense Evasion | Avoid being detected |
| 8. Credential Access | Steal account names and passwords |
| 9. Discovery | Figure out your environment |
| 10. Lateral Movement | Move through your environment |
| 11. Collection | Gather data of interest to their goal |
| 12. Command and Control | Communicate with compromised systems to control them |
| 13. Exfiltration | Steal data |
| 14. Impact | Manipulate, interrupt or destroy your systems and data |
Tactics represent the “why” of an ATT&CK technique or sub technique. Each tactic represents a specific goal an attacker aims to achieve, such as gaining initial access to a system, executing malicious code, or exfiltrating data.
These tactics are not standalone; they form an interconnected web of potential attack methodologies that adversaries can adapt and combine based on their objectives and the target environment.
The framework categorizes these tactics in a way that mirrors the lifecycle of a cyber attack, starting from the reconnaissance phase, where attackers gather information on potential targets, to the impact phase, where the actual damage is inflicted. This lifecycle approach helps comprehensively understand an attack's progression but also aids in developing layered defense strategies that address vulnerabilities at each stage.
By dissecting each tactic, cybersecurity professionals can dive deep into the techniques and sub-techniques that underpin them, gaining insights into the specific methods attackers use to accomplish their goals. This level of granularity is crucial for developing precise detection mechanisms and tailoring defenses to the unique characteristics of each threat.
The framework's emphasis on real-world applications of these tactics, supported by case studies and incident reports, enriches its practical value. Security teams can leverage this information to simulate attack scenarios, test their defenses, and refine their incident response strategies, ensuring they are prepared to counteract the evolving tactics employed by cyber adversaries.
Enterprise Matrix Tactics (14)
Adversary tactics in the enterprise matrix include trying to do the following:
- Reconnaissance: Gather information they can use to plan future operations.
- Resource Development: Establish resources they can use to support operations.
- Initial Access: Get into a network.
- Execution: Run malicious code.
- Persistence: Maintain their foothold.
- Privilege Escalation: Gain higher-level permissions.
- Defense Evasion: Avoid being detected.
- Credential Access: Steal account names and passwords.
- Discovery: Figure out the target environment.
- Lateral Movement: Move through the target environment.
- Collection: Gather data of interest to their goal.
- Command and Control: Communicate with compromised systems to control them.
- Exfiltration: Steal data.
- Impact: Manipulate, interrupt, or destroy systems and data.
Mobile Matrix Tactics (14)
Adversary tactics in the mobile matrix include trying to do the following:
- Initial Access: Get into a device.
- Execution: Run malicious code.
- Persistence: Maintain their foothold.
- Privilege Escalation: Gain higher-level permissions.
- Defense Evasion: Avoid being detected.
- Credential Access: Steal account names, passwords, or other secrets that enable access to resources.
- Discovery: Figure out the target environment.
- Lateral Movement: Move through the target environment.
- Collection: Gather data of interest to their goal.
- Command and Control: Communicate with compromised devices to control them.
- Exfiltration: Trying to steal data.
- Impact: Manipulate, interrupt, or destroy devices and data.
- Network Effects: Intercept or manipulate network traffic to or from a device.
- Remote Service Effects: Control or monitor the device using remote services.
ICS (Industrial Control Systems) Matrix Tactics (12)
Adversary tactics in the ICS matrix include trying to do the following:
- Initial Access: Get into the industrial control systems environment.
- Execution: Run code or unauthorizedly manipulate system functions, parameters, and data.
- Persistence: Maintain their foothold in the ICS environment.
- Privilege Escalation: Gain higher-level permissions.
- Evasion: Avoid security defenses.
- Discovery: Locate information to assess and identify their targets in the environment.
- Lateral Movement: Move through the ICS environment.
- Collection: Gather data of interest and domain knowledge on the ICS environment to inform their goal.
- Command and Control: Communicate with and control compromised systems, controllers, and platforms with access to the ICS environment.
- Inhibit Response Function: Prevent safety, protection, quality assurance, and operator intervention functions from responding to a failure, hazard, or unsafe state.
- Impair Process Control: Manipulate, disable, or damage physical control processes.
- Impact: Manipulate, interrupt, or destroy ICS systems, data, and their surrounding environment.
MITRE ATT&CK Techniques
Delving deeper into the MITRE ATT&CK framework reveals a sophisticated matrix of techniques and sub-techniques that serve as the building blocks for the tactics outlined in the previous section. Each technique provides a detailed overview of cyber adversaries' methods to achieve their tactical objectives.
These techniques are further broken down into sub-techniques, offering a more granular view of the attacker's arsenal and showcasing the specific actions taken to execute a broader strategy.
For example, under the tactic of "Initial Access," techniques might include spear-phishing emails or exploiting public-facing applications. Sub-techniques detail the nuances of these methods, such as using a malicious attachment or link in the spear-phishing scenario or the specific type of vulnerability exploited in a public-facing application. This layered approach enables defenders to identify the general method of attack and understand the intricacies of how it was carried out.
The framework's comprehensive cataloging of these techniques and sub-techniques is continuously updated to reflect the evolving nature of cyber threats. Each entry is supported by real-world examples, indicators of compromise, and mitigation strategies, providing security professionals with actionable intelligence. This depth of information facilitates a proactive defense posture, allowing teams to anticipate potential attack vectors and fortify their defenses accordingly.
Security practitioners leverage this detailed knowledge to tailor their security measures more precisely, enhancing their ability to detect, respond to, and mitigate threats. The MITRE ATT&CK framework empowers organizations to build a more resilient and responsive cybersecurity posture by mapping out the adversary's playbook in detail.
Discover how MITRE ATT&CK techniques categorize and describe the methods and tactics used by adversaries in cyberattacks: What are MITRE ATT&CK Techniques?
What Are Sub-techniques?
Subtechniques are more specific descriptions of the adversarial behavior used to achieve a goal. They describe behavior at a lower level than a technique, providing details that help security teams craft a precise cybersecurity tactic to mitigate specific risks. For example, an adversary may use keylogging for credential access.
MITRE ATT&CK Procedures
Procedures are the specific implementations adversaries use to execute a technique or sub-technique. To better illustrate this, an adversary using PowerShell to inject into lsass.exe for credential access by scraping LSASS memory on a victim could be a procedure. In the ATT&CK framework, procedures are categorized as techniques observed in the wild in the "Procedure Examples" section of the technique pages.
What Is the Difference Between Subtechniques and Procedures?
Sub techniques and procedures describe different things in ATT&CK. A sub-technique provides a granular explanation of how cyberattacks are executed, and procedures are used to describe techniques in the real world. Furthermore, since procedures are specific implementations of methods and sub-techniques, they may include several additional sub-techniques as part of the description.
For example, an adversary using PowerShell to inject into lsass.exe to dump credentials by scraping LSASS memory on a victim is a procedure implementation containing several sub-techniques covering PowerShell, credential access, and process injection used against LSASS.
Deep dive to determine the difference between subtechniques and procedure in MITRE ATT&ACK: What is the Difference Between MITRE ATT&CK Sub-Techniques and Procedures?
Using the MITRE ATT&CK Framework
Adversary emulation and red teaming exercises leverage the framework to simulate real-world cyber attacks. These simulations help understand the effectiveness of current security measures and identify potential weaknesses within an organization's network. Organizations can develop more robust defenses and response strategies by emulating the behaviors and tactics of actual adversaries.
The development of behavioral analytics is another critical application of the MITRE ATT&CK framework. By analyzing patterns and techniques outlined in the framework, security teams can enhance their detection systems to identify suspicious activities that deviate from normal behavior, mitigating threats early.
The MITRE ATT&CK framework makes assessing the defensive gaps and maturity of Security Operations Centers (SOCs) more structured. It provides a clear benchmark against which SOCs can measure their capabilities in detecting, responding to, and mitigating cyber threats, facilitating targeted improvements in their security operations.
Lastly, the framework enriches cyber threat intelligence by offering a detailed and organized method for categorizing and communicating about cyber adversary behavior. This enrichment supports organizations in understanding the threat landscape more comprehensively, enabling them to prepare more effectively against potential cyber attacks.
Implementing the MITRE ATT&CK Framework
| MITRE Evaluation | Product Evaluated | Resource |
|---|---|---|
| MITRE APT 3 | Cortex XDR | Webinar: Unpack MITRE ATT&CK Results with Forrester |
| MITRE APT 29 | Cortex XDR | White paper: White paper: The Ultimate Guide to the MITRE ATT&CK Round 2 EDR Evaluation |
| MITRE Carbanak FIN 7 | Cortex XDR | Video: MITRE ATT&CK Round 3 Video E-Book: Essential Guide to MITRE ATT&CK Round 3 e-Book Webcast: Carbanak + FIN7: MITRE ATT&CK Round 3 Unpacked |
| MITRE Wizard Spider & Sandworm | Cortex XDR | Webcast: Demystifying the 2022 MITRE ATT&CK® Evaluations Video: 2022 MITRE Engenuity ATT&CK Evaluations – Wizard Spider & Sandworm E-Book: The Essential Guide to MITRE ATT&CK Round 4 Essential Guide to MITRE ATT&CK Round 4 2022 MITRE-4 ATT&CK Guide |
To start using the MITRE ATT&CK framework, see the Getting Started page. Also, check out the Resources section of the website and the blog for related projects, use cases, and other material. The ATT&CK framework presents all adversarial tactics and techniques in an easily understandable manner. In each column, individual techniques are listed at the top, and attack tactics are displayed at the bottom.
ATT&CK forms a matrix in which each attack sequence comprises at least one technique per tactic. A complete attack sequence can be assembled from left to right (Initial Access to Command and Control). Multiple techniques may be used for a single tactic. For instance, if a spear phishing exploit employs both an attachment and a link, the attacker may try both simultaneously.
ATT&CK can be used in several ways to help security operations, threat intelligence, and security architecture. Some of the primary use cases are:
- Adversary emulation
- Red team programs
- Behavioral analytics development
- Defensive gap assessment
- SOC maturity assessment
- Cyberthreat intelligence
MITRE Engenuity ATT&CK evaluations provide assessments for participating vendors to identify areas for improvement, including updating prevention, detection, and response rules that inform cybersecurity policies. While this exercise does not provide overall comparison scores or ranking, it gives a vendor-agnostic summary of the various methodologies employed by security practitioners for identifying and preventing sophisticated attack campaigns.
Learn how to implement and identify MITRE ATT&CK Techniques most relevant to your company’s sensitive data: How Do I Implement MITRE ATT&CK Techniques?
Challenges of Implementing the MITRE ATT&CK Framework
While the MITRE ATT&CK Framework is a powerful tool for enhancing cybersecurity, implementing it can be challenging. One of the primary challenges is the need for proper training and expertise in using the framework. Additionally, the framework requires significant time and resources to implement effectively.
Organizations can overcome these challenges by partnering with a cybersecurity expert who can provide training and guidance on using the framework. By working with an expert, organizations can ensure that they use the framework effectively and maximize its benefits.
MITRE ATT&CK Tools and Resources
Delving into the MITRE ATT&CK framework reveals a treasure trove of tools and resources to enhance cybersecurity defenses. These tools facilitate a deeper understanding of the framework and empower security professionals to implement its strategies effectively.
Among the most notable resources are the ATT&CK Navigator, MITRE Cyber Analytics Repository (CAR), Caldera, and Atomic Red Team. Each serves a unique purpose in the cybersecurity ecosystem, offering insights and capabilities tailored to various threat detection, analysis, and simulation aspects.
Attack Navigator
The ATT&CK Navigator stands out as a visualization tool. It enables users to explore and customize the vast array of tactics, techniques, and procedures (TTPs) documented within the ATT&CK framework. Its interactive interface allows for mapping an organization's defenses against potential threats, highlighting areas of strength and vulnerability.
Cyber Analytics Repository (CAR)
MITRE's Cyber Analytics Repository (CAR) takes a different approach, focusing on the analytical side of cybersecurity. It provides a comprehensive collection of analytics based on ATT&CK techniques that can be applied directly to network and event data. This repository is invaluable for those seeking to enhance their detection capabilities and understand the technical specifics of various attack methods.
Caldera and Atomic Red Team
Caldera and Atomic Red Team offer practical tools for simulating adversary techniques and testing network defenses. Caldera is an automated adversary emulation system that uses the ATT&CK framework to create realistic attack scenarios. Atomic Red Team, on the other hand, provides a library of scripts for executing specific techniques, allowing teams to test their resilience against known threats.
Comparing MITRE ATT&CK to Other Models
MITRE ATT&CK stands out for its comprehensive and nuanced approach to cataloging tactics, techniques, and procedures (TTPs) threat actors use. Its continuous update cycle ensures relevance in the face of evolving threats, distinguishing it from models that may not be as frequently revised.
Other models, such as the Cyber Kill Chain, focus on an attacker's sequential steps to breach a system. This model aids in understanding the progression of an attack, allowing defenders to anticipate and disrupt threats at various stages. While the Cyber Kill Chain offers a linear attack perspective, MITRE ATT&CK covers a broader spectrum by detailing post-exploitation techniques and lateral movements within compromised networks.
Cyber Kill Chain
The Cyber Kill Chain model provides a framework for understanding the anatomy of cyberattacks and breaking them down into manageable segments. This model helps defenders to identify and thwart attacks more effectively by tailoring defensive strategies at each stage, ranging from proactive measures during reconnaissance to email filtering and anti-malware solutions during weaponization.
However, the model's linear progression may not fully capture the multifaceted tactics employed by advanced adversaries. To complement this, the MITRE ATT&CK framework offers a more granular view of the adversary's playbook, providing a comprehensive toolkit for defending against cyber threats.
The choice between MITRE ATT&CK and other models often depends on the specific needs and capabilities of the cybersecurity team. While some prefer the structured approach of the Cyber Kill Chain for its simplicity and focus on prevention, others value the depth and breadth of scenarios covered by MITRE ATT&CK. The decision hinges on whether the priority is to understand the anatomy of an attack or to develop a versatile defense against a wide range of adversarial tactics.
MITRE D3FEND Framework
The MITRE D3FEND framework complements the offensive-focused MITRE ATT&CK framework with defensive cybersecurity countermeasures to proactively detect, mitigate, and prevent cyberattacks. D3FEND stands for Detection, Denial, and Disruption Framework Empowering Network Defense.
D3FEND provides defensive techniques that help security teams understand what countermeasures are most effective when combatting specific adversarial behavior, improving the efficacy of cybersecurity strategies. The insights the MITRE D3FEND framework provides can be used to understand weaponization techniques that an adversary might use in cyberattacks, such as encrypting malware for defense evasion.
Benefits of MITRE ATT&CK Framework
One of the primary benefits of integrating MITRE ATT&CK is the enhancement of threat intelligence and security operations. Teams can leverage the framework to simulate real-world attacks, identifying vulnerabilities within their systems before exploiting them. This proactive approach strengthens security postures and educates security teams on the evolving landscape of cyber threats.
Moreover, the framework facilitates a common language for cybersecurity professionals. By categorizing and describing threats in a standardized manner, it simplifies communication across teams and with external stakeholders, improving collaboration and response times during incidents.
Organizations also benefit from the continuous updates and community contributions to the MITRE ATT&CK database. As new techniques and tactics are observed and documented, the framework evolves, offering an up-to-date resource that reflects the current threat environment.
MITRE ATT&CK for Different Technologies
The MITRE ATT&CK Framework can be applied to any technology or software application that may be targeted by threat actors, including, but not limited to, operating systems, applications, network devices, and cloud services. Organizations can develop effective countermeasures and improve their security posture by understanding attackers' techniques and tactics.
ATT&CK Technologies can include the following:
- Enterprise IT systems covering:
- Windows
- macOS
- Linux
- Network infrastructure devices (network)
- Container technologies (containers)
- Cloud systems covering infrastructure as a service (IaaS)
- Software as a service (SaaS)
- Office 365
- Azure Active Directory (Azure AD)
- Google Workspace
- Mobile devices covering:
- Android
- iOS
- ICS covering industrial control systems
Learn how MITRE ATT&CK addresses real-world adversarial behavior across different technologies: How Does MITRE ATT&CK Apply to Different Technologies?
What Is MITRE Engenuity?
MITRE Engenuity is an organization that collaborates with private companies to address public-interest challenges in cybersecurity, infrastructure resilience, healthcare effectiveness, and next-generation communications. In its first initiative, MITRE Engenuity brings together security experts from leading organizations to strengthen cyber defense by gaining a deeper understanding of cyber adversaries.
To improve organizations' resilience to known adversary behavior, MITRE Engenuity uses the ATT&CK® knowledge base to evaluate cybersecurity products based on three criteria:
- Giving end users objective insight into the functionality of participating security products
- Enabling participants to see the true capabilities of their security products
- Enhancing the capabilities of participants
There is no competitive analysis in these evaluations. Rather than providing a "winner," they illustrate how each vendor approaches threat defense within the context of ATT&CK. There is no universal way to analyze, rank, or score solutions. Their evaluation methodologies are publicly available, and the results are publicly released. They are continually evolving and extending their methodologies and content to ensure a fair, transparent and valuable evaluation process.
What are MITRE Engenuity ATT&CK Evaluations?
It is up to vendors to determine how to detect and protect potential adversary behavior. MITRE Engenuity requires that vendors provide proof of detection, although they may not share all detection details publicly. Vendors may not disclose all detection details in public results. We are responsible for abstracting the data using categories and discussing the products using the information they provide us.
To determine the appropriate category for detection, MITRE Engenuity captures supporting evidence in the form of screenshots and notes taken during the evaluation. A detection or protection can be classified into two types: "Main" and "Modifier." The primary category designation of each detection varies based on the amount of context provided to the user, and the modifier category designation can help describe the event in greater detail as well.
Categories Utilized by MITRE Engenuity for Detection:
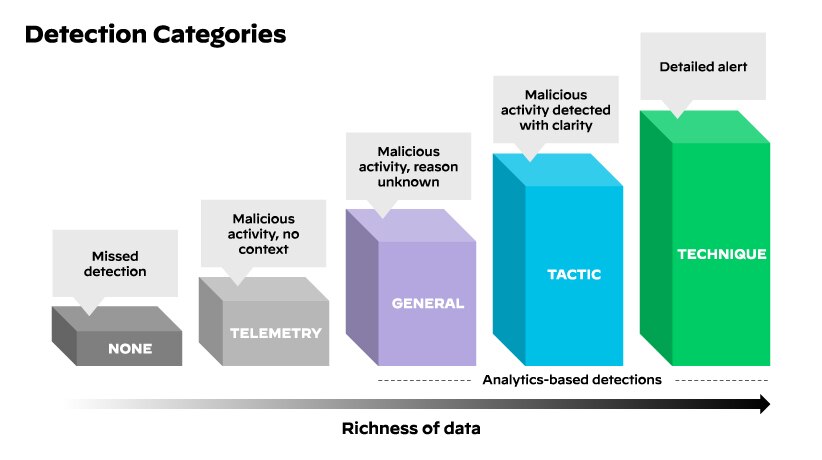
In March of 2022, fourth-round attack evaluations were released, focusing on Wizard Spider and Sandworm threat actors. Wizard Spider is a financially motivated criminal group that has been a threat to major corporations, including hospitals, since August 2018. Sandworm is a destructive Russian threat group that carried out attacks in 2015 and 2016 against UK electrical companies and is well known for the 2017 NotPetya attacks.
Turla is an internationally recognized threat group that has been active since at least the early 2000s. Worldwide, it has infected more than 45 countries. Known targets of the organization include government agencies, diplomatic missions, military groups, and research and media organizations. Turla uses open-source and in-house tools to maintain operational security, including a command-and-control network and various open-source and sophisticated techniques.
According to MITRE Engenuity, this latest round of evaluations showed significant product growth by vendors, including Palo Alto Networks. Emphasis was placed on threat-informed defense capabilities and further prioritization of the ATT&CK framework. Further information on the evaluation results can be found here.
MITRE ATT&CK for CISOs
In the realm of security, the MITRE ATT&CK framework is foundational. Gathering real-world data and use cases, it details adversarial tactics and guidance on countermeasures. The MITRE ATT&CK framework gives CISOs a strategic cybersecurity advantage over threat actors with actionable threat intelligence and tools to improve their organization’s security posture, including the following.
- Comprehensive knowledge base of adversarial tactics and techniques based on real-world observations of cybersecurity threats to help security teams prepare for, detect, and respond to cyberattacks.
- Common language facilitates communication about cybersecurity across security teams and internal and external stakeholders.
- A reference architecture for security operations center (SOC) teams to use as a baseline against which to compare their security posture and identify potential threats and vulnerabilities.
- Insights into the latest attacker malware and other adversarial tactics help CISOs understand complex attack patterns and address real-world use cases.
History and Evolution of the MITRE ATT&CK Framework
MITRE is an unbiased, not-for-profit organization based in Bedford, Massachusetts, and McLean, Virginia. It was established to provide engineering and technical guidance to the federal government.
The MITRE ATT&CK framework was developed as part of an MITRE research project in 2013 to document the TTPs advanced persistent threat (APT) groups use against enterprise businesses. It was created out of a need to describe adversary TTPs that would be used by an MITRE research project called FMX.
FMX's objective was to investigate how endpoint telemetry data and analytics could help improve the post-intrusion detection of attackers operating within enterprise networks. The ATT&CK framework was used to test the efficacy of the sensors and analytics under FMX and served as the common language that both offense and defense could use to improve over time.
As of 2015, MITRE ATT&CK is freely available and globally accessible for download to the public. Today, it helps security teams in organizations of all sectors better understand the threats at play and secure their systems against them.
The MITRE ATT&CK framework has continued to evolve, changing to keep pace with the threat intelligence needs for new cybersecurity use cases. While MITRE ATT&CK was initially developed to address threats against a single target environment (i.e., Windows enterprise systems), it has expanded to include cyberattacks against others, including Linux, macOS, mobile, cloud, network, containers, and industrial control systems (ICS).
Explore the evolution of MITRE ATT&CK’s adaptation and its impact on cybersecurity strategies: How has MITRE ATT&CK Improved, Adapted, and Evolved?
More Information on MITRE ATT&CK
Learn more about the MITRE ATT&CK framework and evaluations with Palo Alto Networks Cortex XDR.
For further information on the ATT&CK framework, visit MITRE.org. Check out the ATT&CK Navigator tool to help you navigate, annotate, and visualize ATT&CK techniques.
The MITRE ATT&CK Framework and Cortex XDR
Cortex XDR helps to stop modern attacks by applying AI and behavioral analytics to endpoint, network, cloud and third-party data. It unifies prevention, detection, investigation, and response in one platform for unrivaled security and operational efficiency.
Cortex XDR provides industry-leading coverage of MITRE ATT&CK techniques and consistently demonstrates stellar performance in independent industry testing, including the MITRE Engenuity ATT&CK Evaluations.
