- 1. Why do businesses today need SASE?
- 2. What is SASE architecture?
- 3. What are the components of SASE?
- 4. What are the use cases for SASE?
- 5. What are the benefits of SASE?
- 6. What are the potential SASE implementation challenges?
- 7. How to choose a SASE provider and what to look for
- 8. How to execute a successful SASE implementation in 6 steps
- 9. What are the most common SASE myths?
- 10. How SASE works with complementary technologies
- 11. Comparing SASE with other security and technology solutions
- 12. What is the history of SASE?
- 13. SASE FAQs
- Why do businesses today need SASE?
- What is SASE architecture?
- What are the components of SASE?
- What are the use cases for SASE?
- What are the benefits of SASE?
- What are the potential SASE implementation challenges?
- How to choose a SASE provider and what to look for
- How to execute a successful SASE implementation in 6 steps
- What are the most common SASE myths?
- How SASE works with complementary technologies
- Comparing SASE with other security and technology solutions
- What is the history of SASE?
- SASE FAQs
What Is SASE (Secure Access Service Edge)? [Starter Guide]
- Why do businesses today need SASE?
- What is SASE architecture?
- What are the components of SASE?
- What are the use cases for SASE?
- What are the benefits of SASE?
- What are the potential SASE implementation challenges?
- How to choose a SASE provider and what to look for
- How to execute a successful SASE implementation in 6 steps
- What are the most common SASE myths?
- How SASE works with complementary technologies
- Comparing SASE with other security and technology solutions
- What is the history of SASE?
- SASE FAQs
Secure access service edge (SASE) is a cloud-native architecture that unifies SD-WAN with security functions like SWG, CASB, FWaaS, and ZTNA into one service.
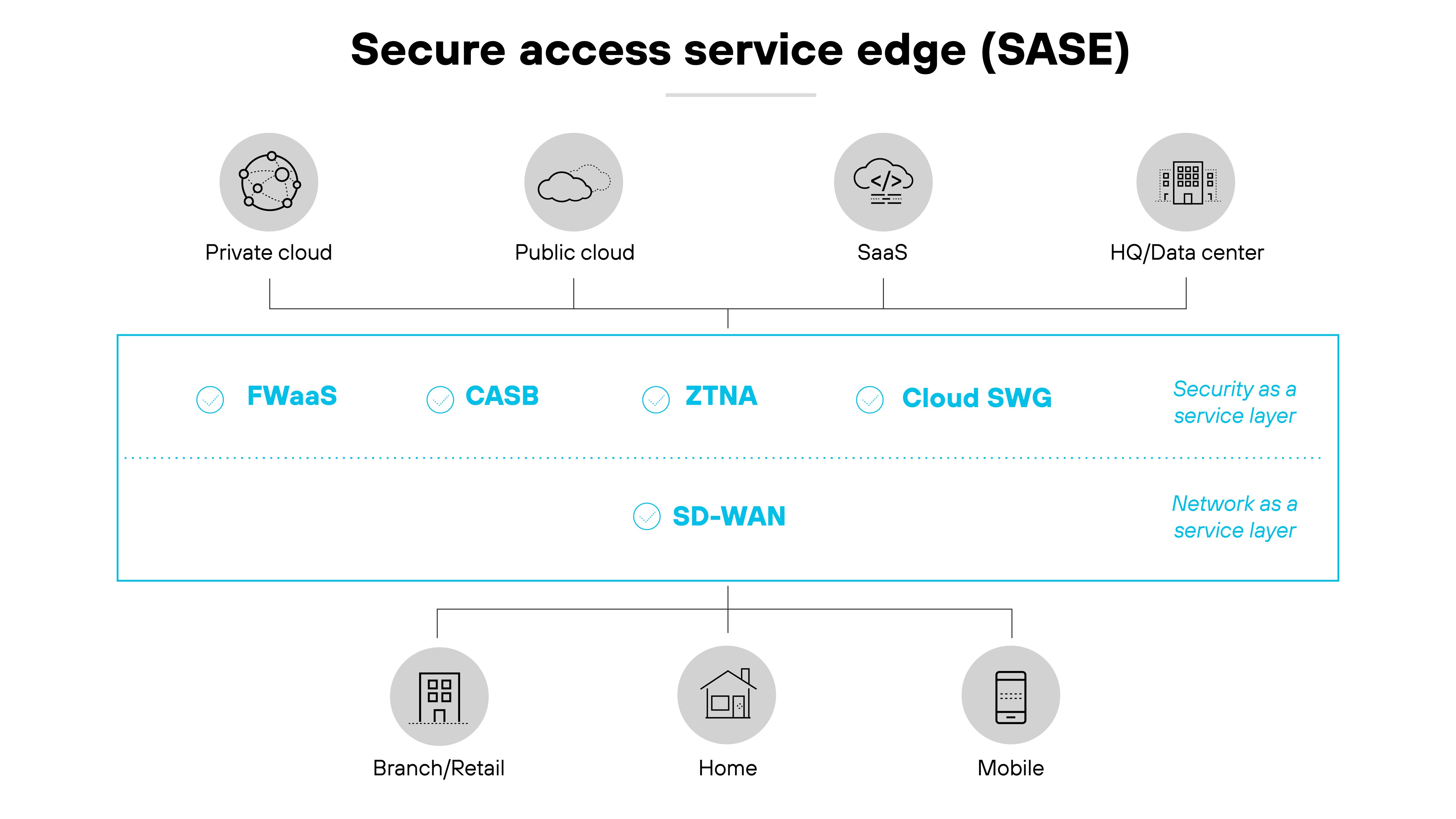
By consolidating networking and security functions into a single, cloud-delivered service, SASE simplifies network management and enhances security.
The architecture supports the dynamic needs of modern organizations by providing scalable, unified access and protection for distributed environments.
Why do businesses today need SASE?
Businesses today are navigating a very different landscape from the traditional, centralized IT environments of the past.
That’s why the secure access service edge (SASE) framework has emerged: to solve for modern security and connectivity demands.
Here's why businesses need SASE now more than ever:
Secure access service edge responds to the decentralization brought on by increased cloud adoption, mobile access, and remote working.
This shift means that both data and users are no longer confined to the office. Which has rendered traditional perimeter-based security models less effective.
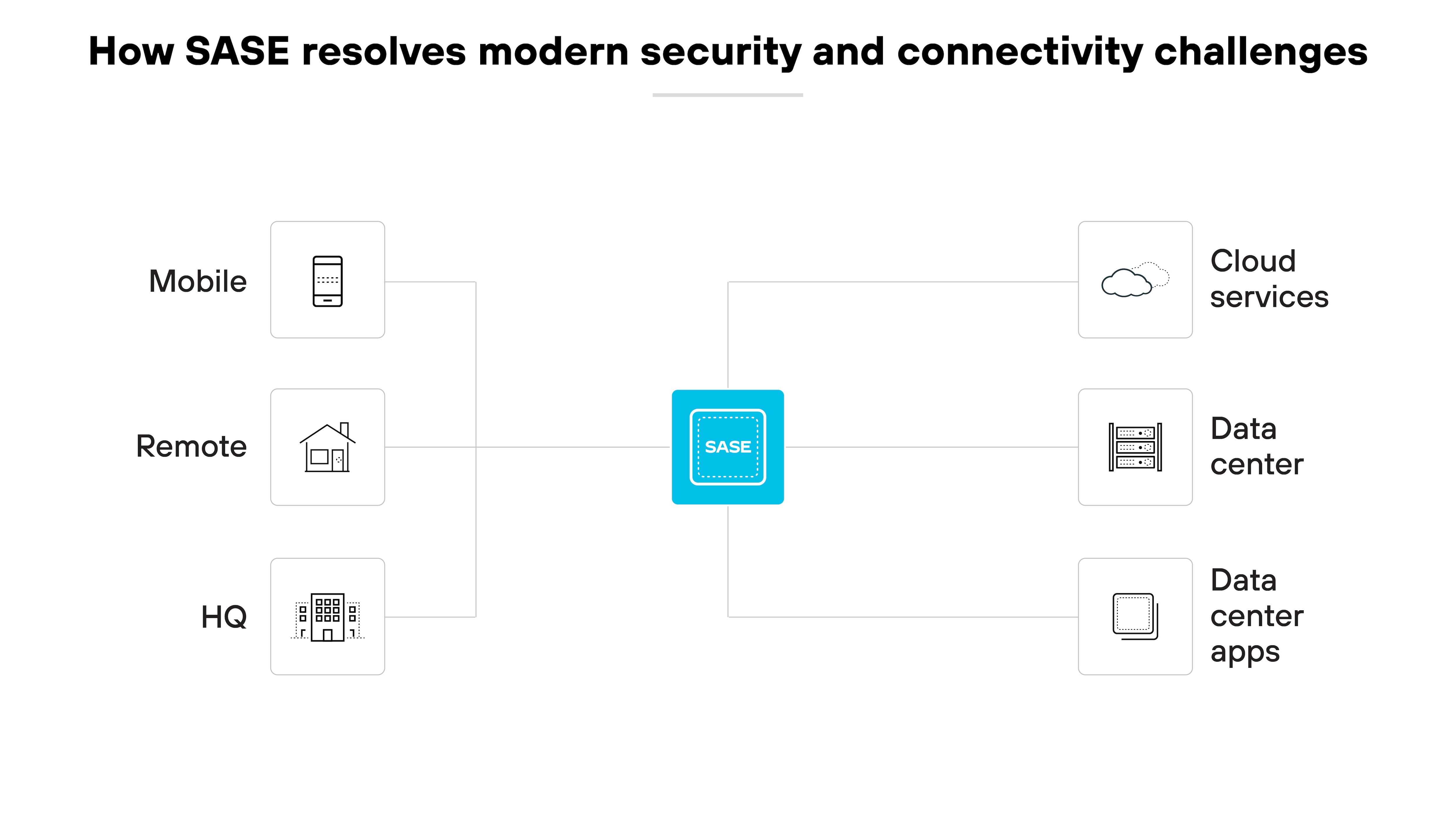
SASE integrates comprehensive security services directly into the network fabric. Which means that security teams can securely, efficiently manage every access request, regardless of origin.
Plus: The integration of security functions within the SASE framework allows businesses to manage their security policies more uniformly.
Taking a unified approach simplifies the administrative burden.
Not to mention, it enhances security by providing consistent, real-time threat prevention and data protection across all environments.
Organizations will continue to transform digitally. And SASE's flexibility and scalability make it indispensable for protecting distributed resources.
What is SASE architecture?
As we’ve established, SASE (secure access service edge) architecture combines networking and security as a service functions into a single cloud-delivered service at the network edge.
Like this:
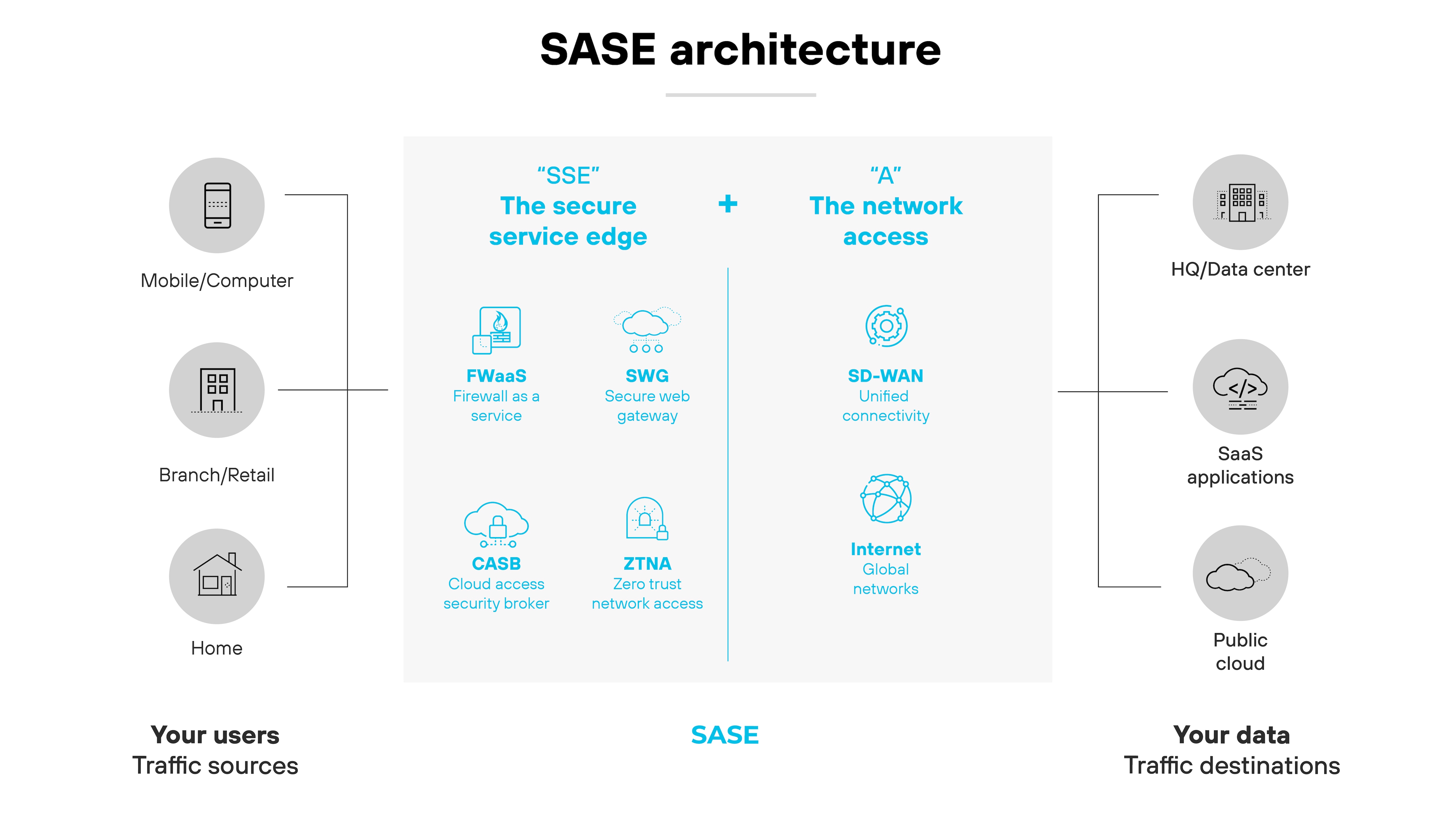
SASE architecture allows an organization to support dispersed remote and hybrid users automatically by connecting them to nearby cloud gateways—as opposed to backhauling traffic to corporate data centers.
It also provides consistent secure access to all applications. Meanwhile, security teams maintain full visibility and inspection of traffic across all ports and protocols.
The model radically simplifies management and reduces complexity, which are two of the main goals of secure access service edge.
It transforms the perimeter into a consistent set of cloud-based capabilities that can be deployed where and when they’re needed. And that’s a far more streamlined alternative to establishing a perimeter around the data center using a collection of disparate, point-product security appliances.
Plus, because it’s cloud-based, secure access service edge allows for a more dynamic, high-performing network. A network that adapts to changing business requirements, the evolving threat landscape, and new innovations.

Five essential technologies are fundamental to secure access service edge deployments:
Secure web gateway (SWG)
Firewall as a service (FWaaS)
Cloud access security broker (CASB)
Zero Trust network access (ZTNA)
Software-defined wide area network (SD-WAN)
Secure web gateway (SWG)
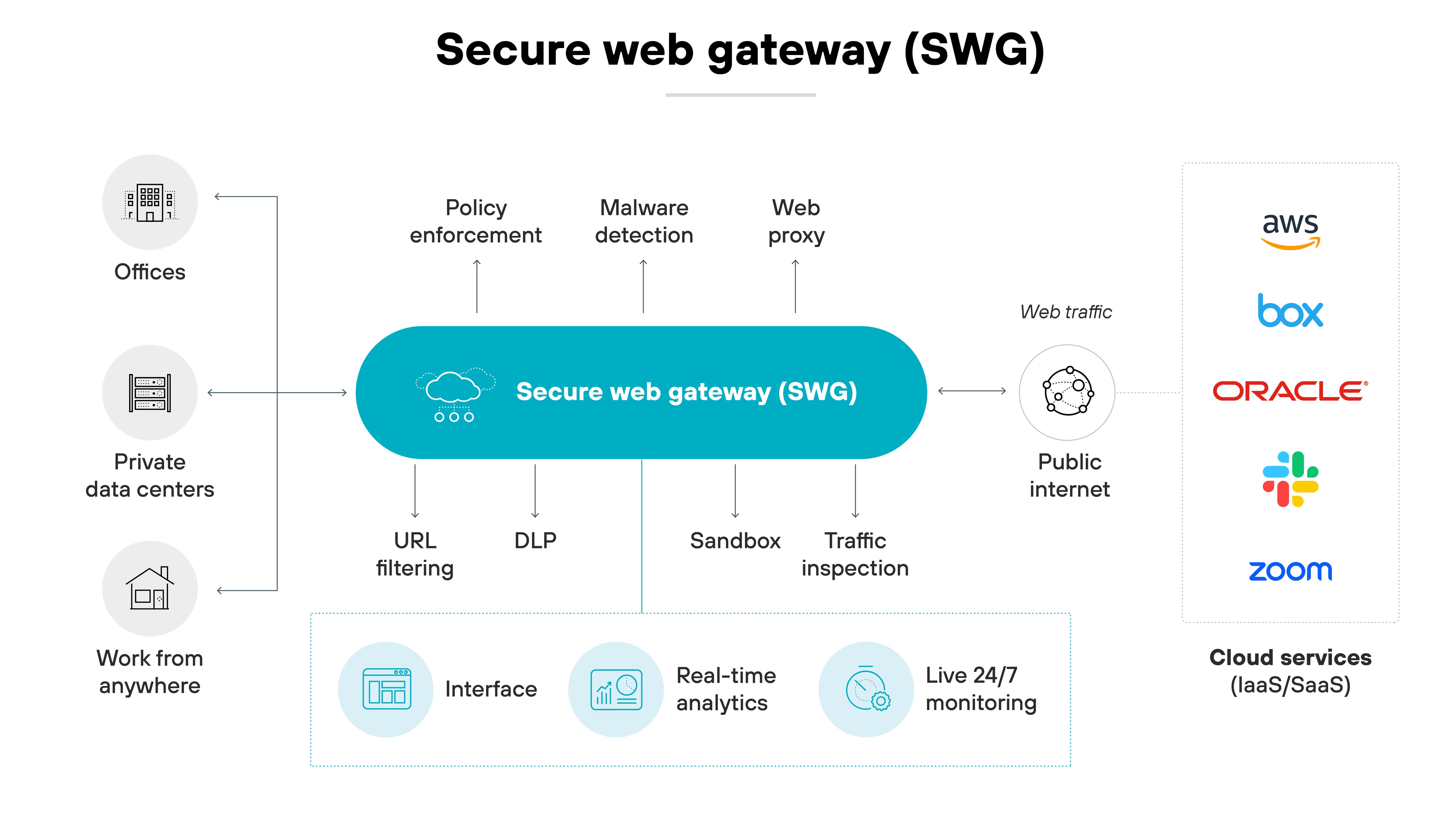
The secure web gateway (SWG) provides URL filtering, SSL decryption, application control, and threat detection and prevention for user web sessions.
Firewall as a service (FWaaS)
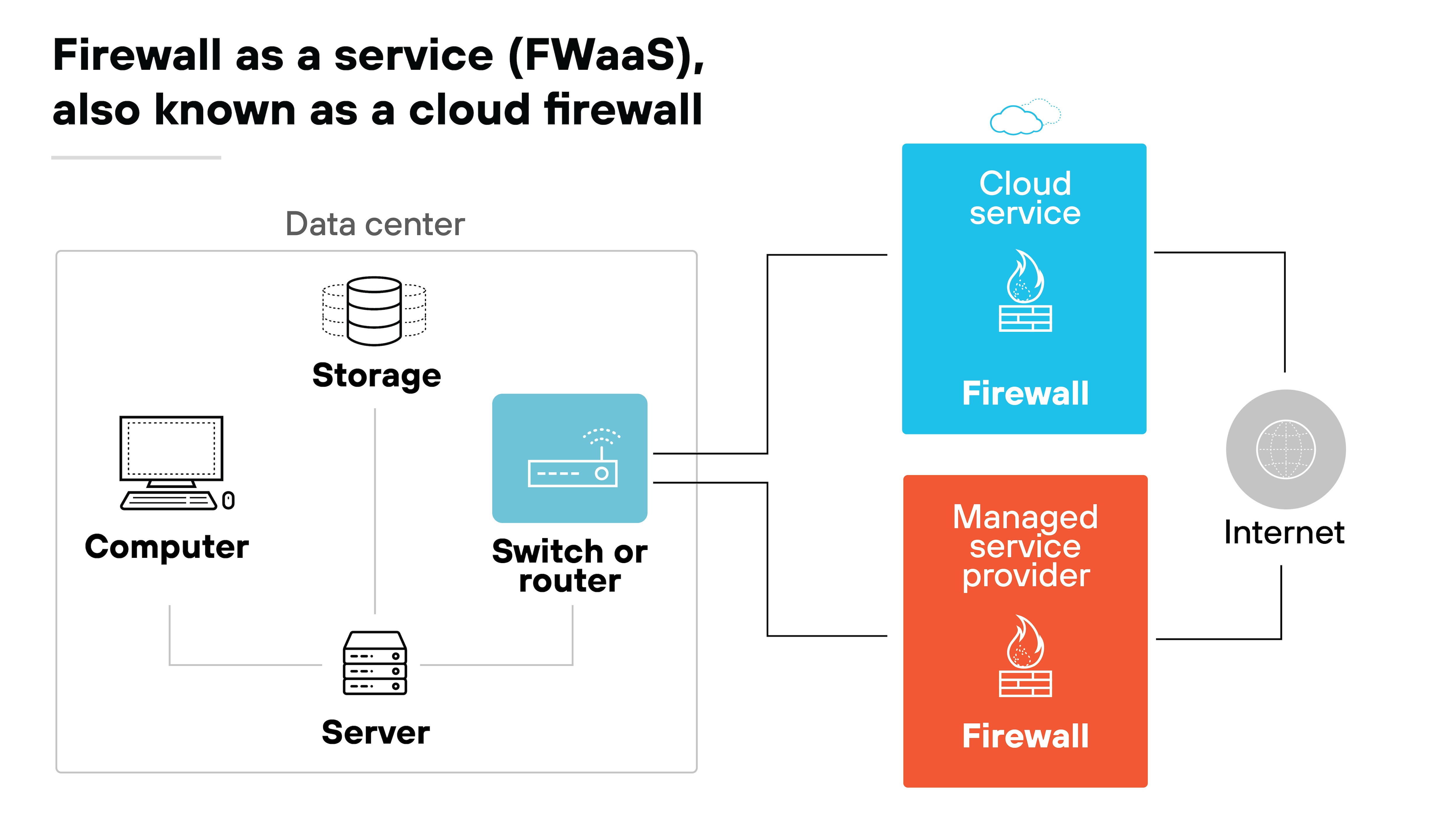
FWaaS delivers a cloud-native, next-generation firewall, providing advanced Layer 7 inspection, access control, threat detection and prevention, and other security services.
Cloud access security broker (CASB)
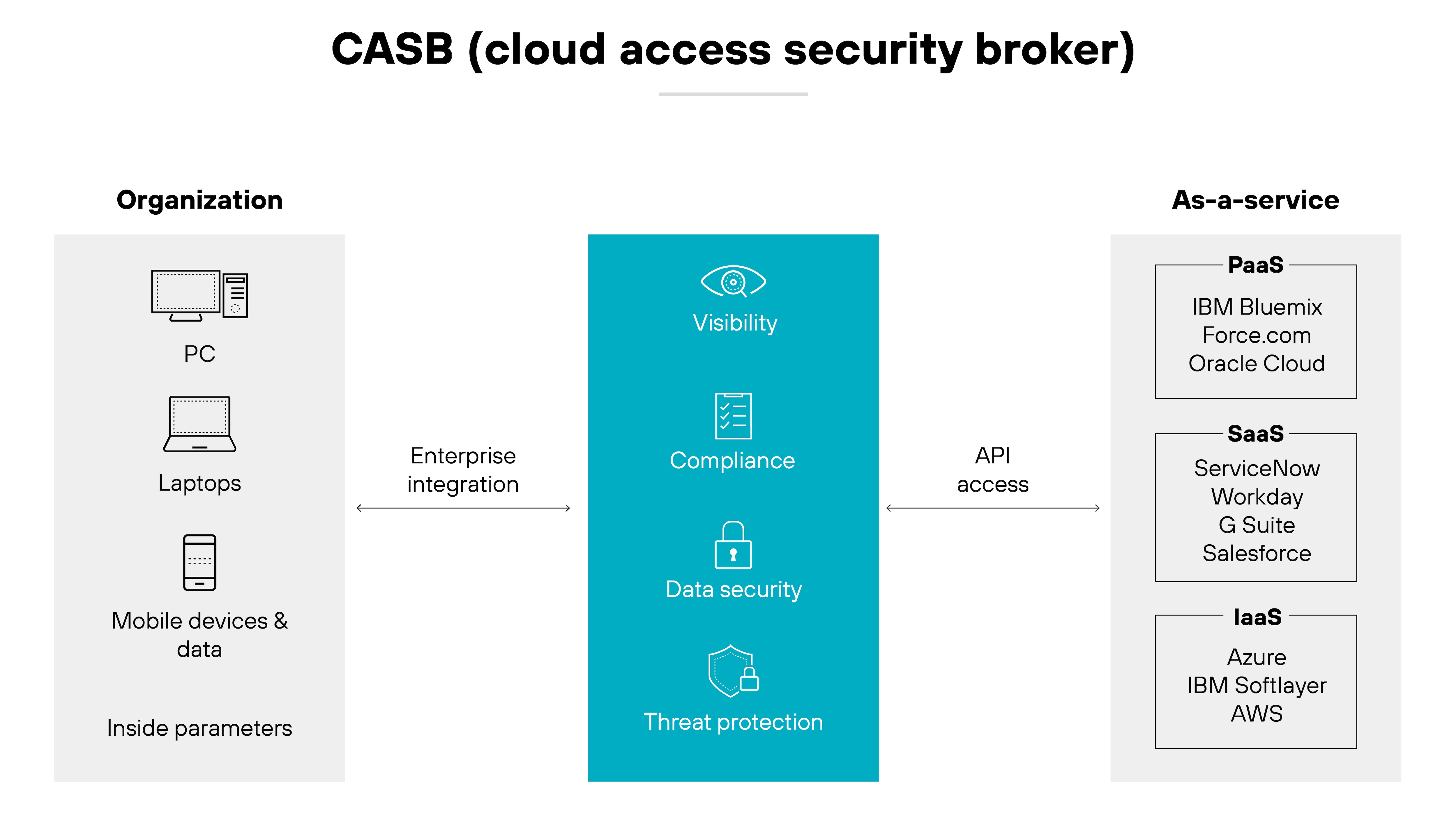
A cloud access security broker (CASB) oversees sanctioned and unsanctioned SaaS applications and offers malware and threat detection.
As part of a DLP solution, it ensures visibility and control of sensitive data in SaaS repositories.
Zero Trust network access (ZTNA)
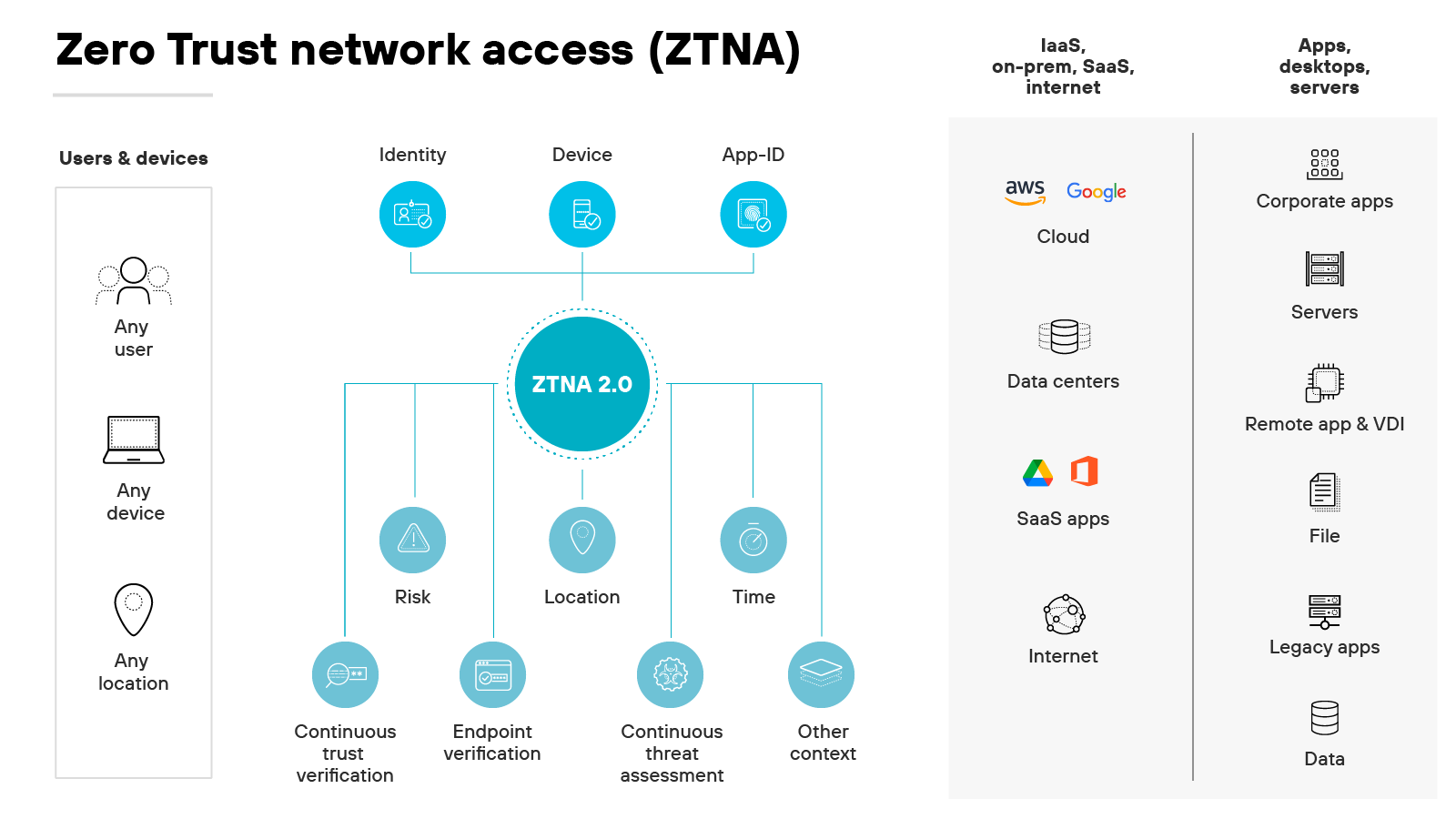
Zero Trust network access (ZTNA) provides continuous verification and inspection capabilities.
It delivers identity-based and application-based policy enforcement for access to an organization’s sensitive data and applications.
SD-WAN
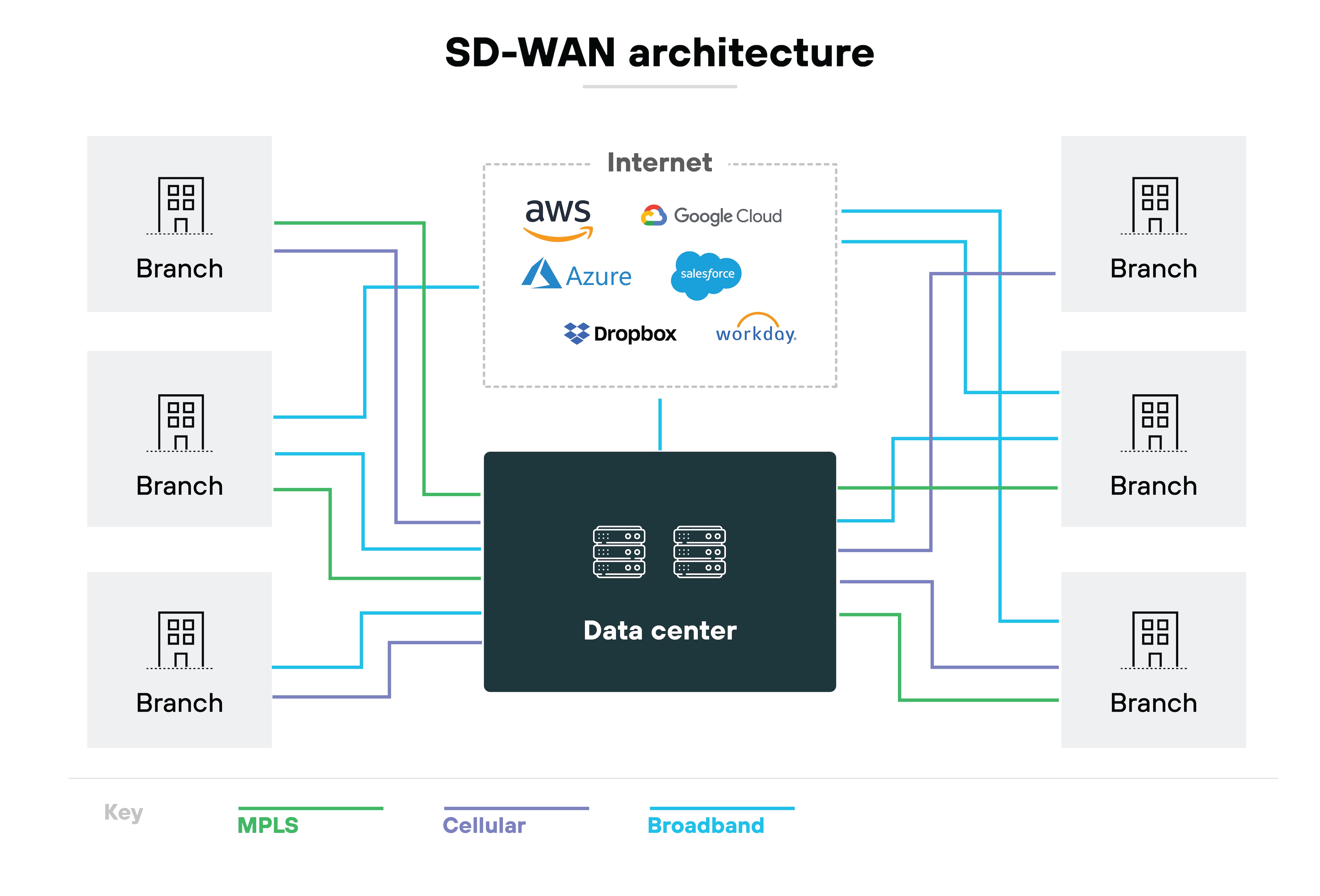
An SD-WAN provides an overlay network decoupled from the underlying hardware, providing flexible, secure traffic between sites and direct to the internet.
What are the use cases for SASE?
The primary SASE use cases include:
Powering hybrid workforces
Connecting and securing branch and retail locations
Supporting cloud and digital initiatives
Global connectivity
MPLS migration to SD-WAN
Powering hybrid workforces
For the hybrid workforce, a cohesive approach to network performance and security is essential.
A secure access service edge architecture emphasizes scalability, elasticity, and low latency, catering directly to this need.
Its cloud-based framework is optimized to deliver application-specific performance. Also, integrated digital experience monitoring (DEM) offers precise visibility for everything affecting user performance.
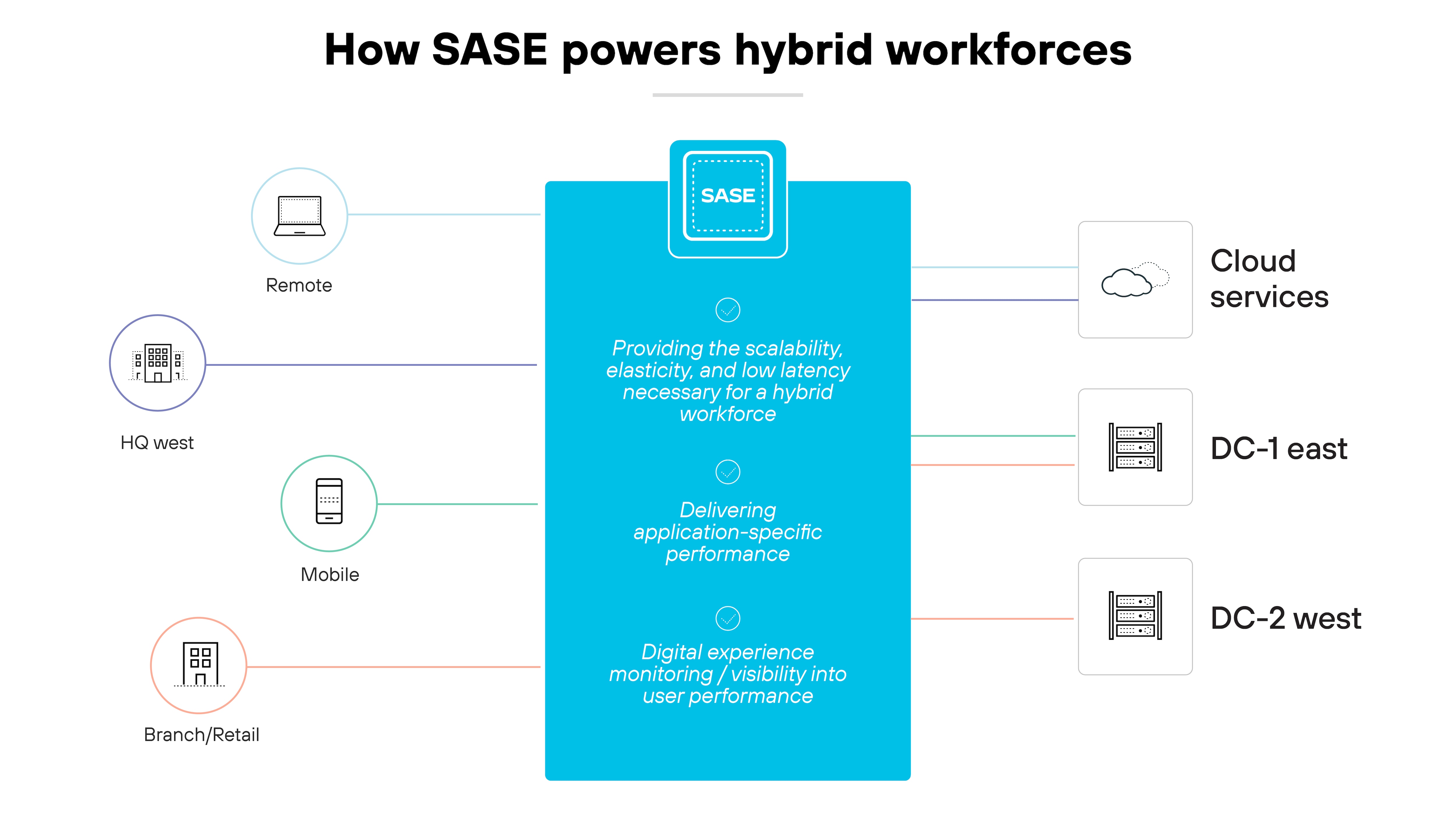
The main advantage of SASE lies in the fusion of networking and security. This combination enhances threat monitoring and detection while filling in security gaps.
The result is streamlined network governance and simplified management.
This is why secure access service edge is a hugely foundational tool for supporting a hybrid work environment.
Connecting and securing branch and retail locations
The SASE model is vital for organizations using SaaS and public cloud services because it addresses performance and security challenges.
Using next-generation SD-WAN, secure access service edge optimizes bandwidth and ensures dynamic security, outperforming traditional data center approaches.
And again, the integration of DEM guarantees an enhanced user experience.
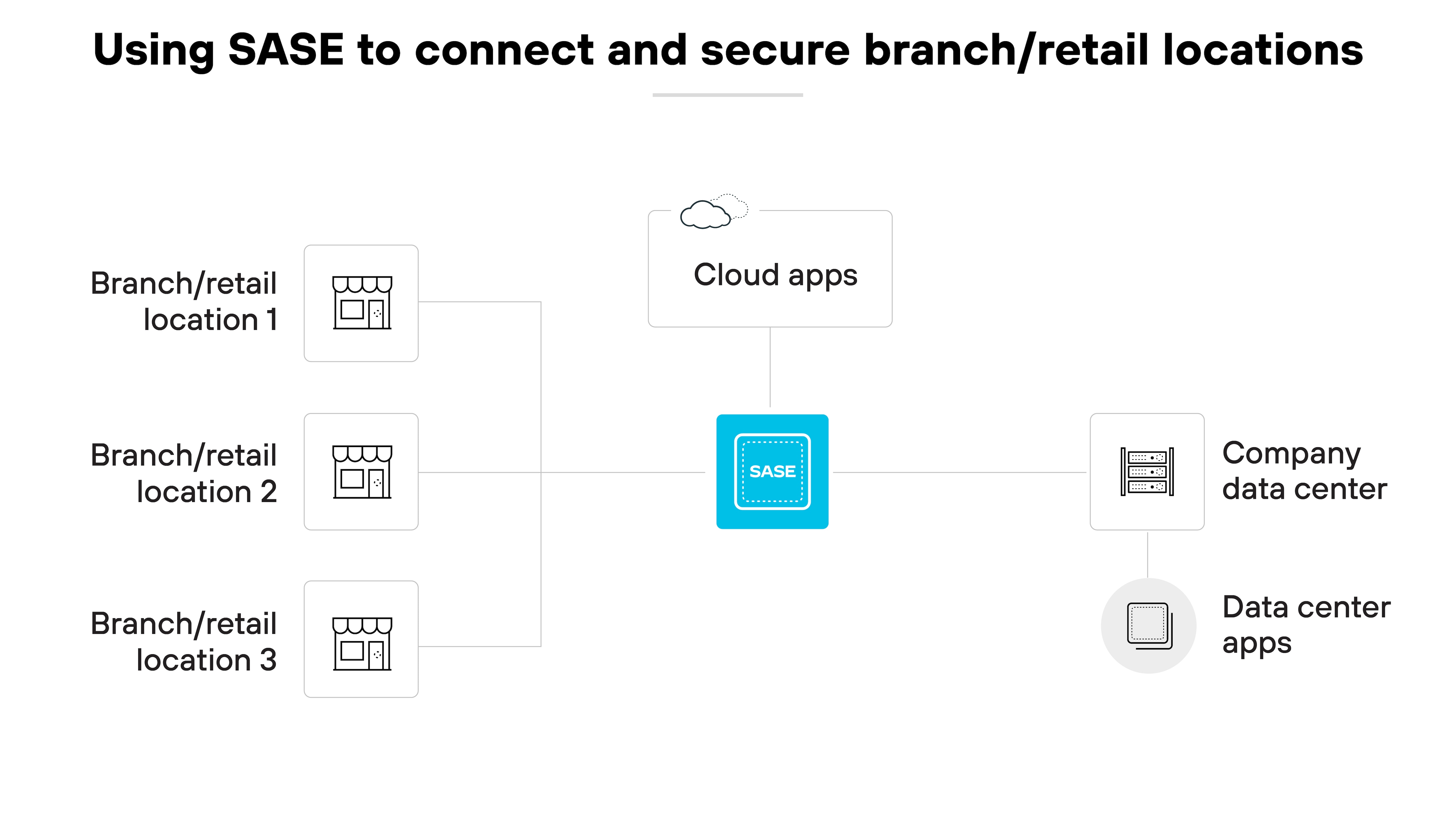
Secure access service edge also reduces network and security expenses. And streamlines vendor management.
Plus: Secure access service edge strengthens data security for branch and remote locations by enforcing consistent policies, simplifying management, and applying Zero Trust.
Which means applications and data are secure, regardless of where they’re located.
Supporting cloud and digital initiatives
SASE is pivotal for cloud and digital transformation. And as organizations lean into SaaS, seamless and secure connectivity is increasingly important.
Thanks to the security consolidation, secure access service edge eliminates the limitations of hardware-based approaches. Which means integrated services and optimized branch deployments.
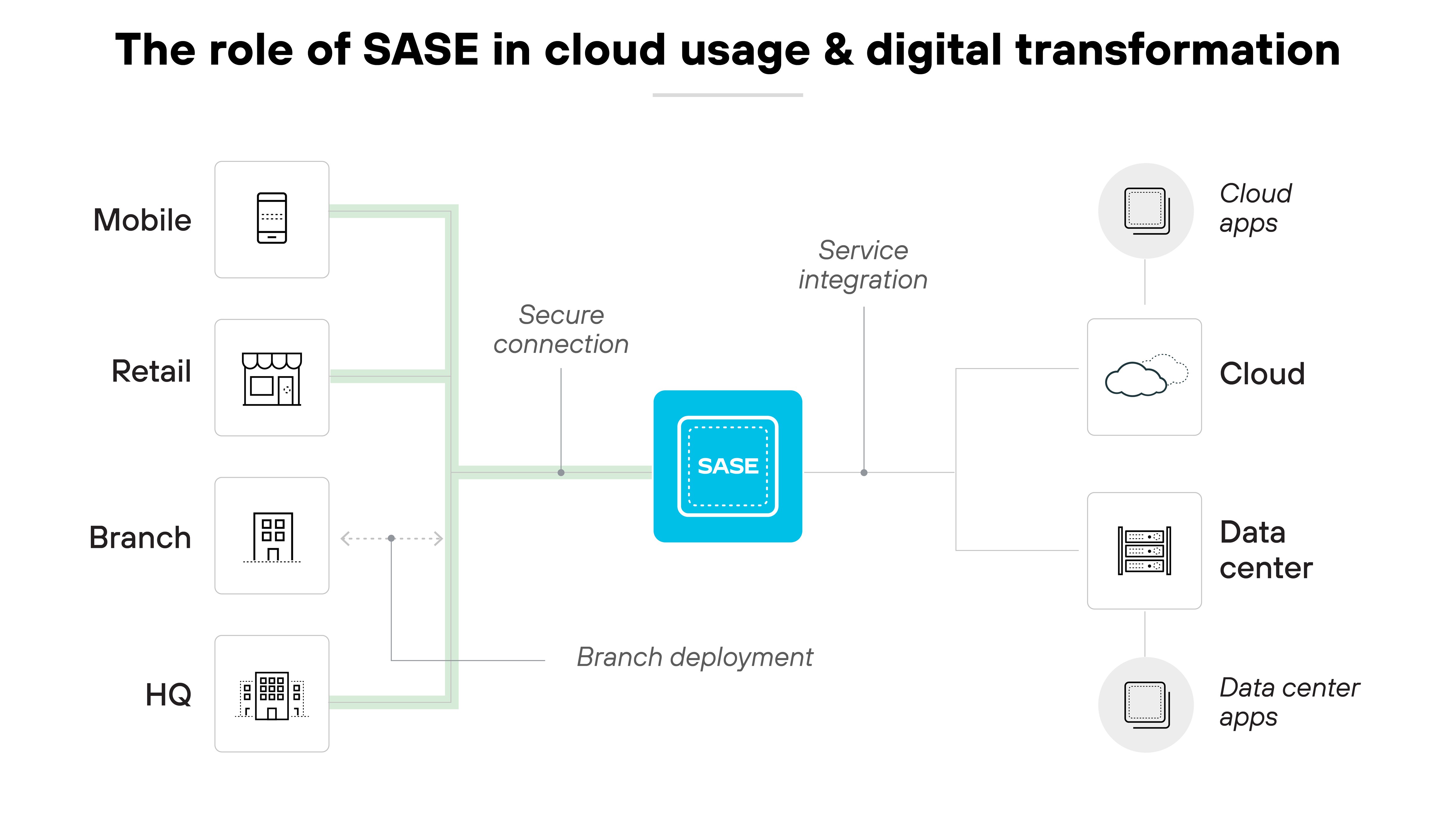
Also: Advanced SD-WAN techniques expand bandwidth and provide deeper network insights. And that leads to enhanced operations and application performance.
Also, AI and ML-based security features significantly improve threat detection.
Dynamic firewalls offer a comprehensive approach to content analysis.
And secure protocols adeptly manage the data streams from IoT devices.
Global connectivity
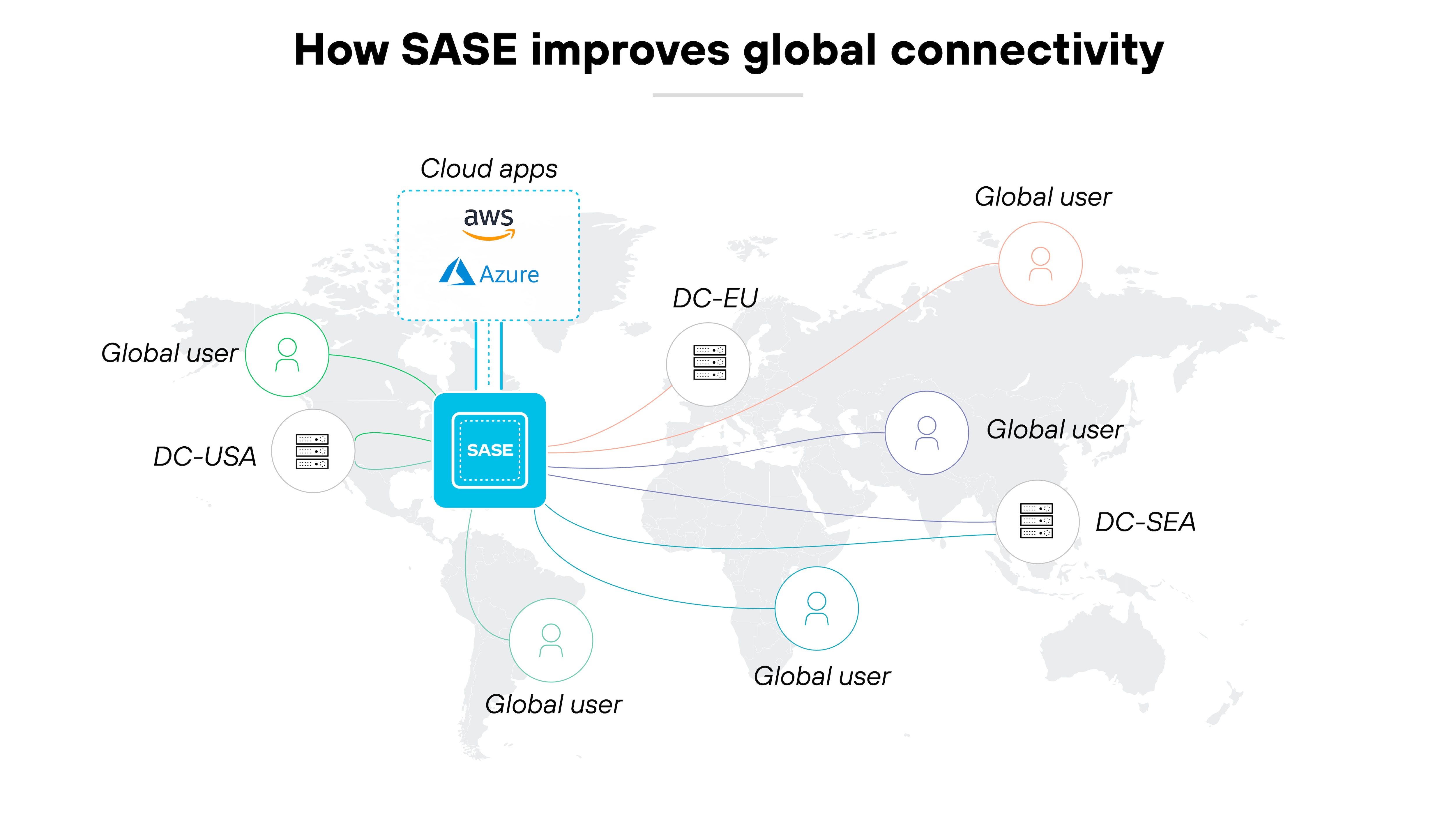
SASE enhances global connectivity. Its architecture is designed to link users directly to a global network, bypassing the need to route traffic through centralized data centers.
This approach reduces latency and improves access speeds. As a result, organizations enjoy a seamless connection experience for users worldwide.
Basically, secure access service edge relies on a distributed network of cloud-based points of presence (PoPs). These PoPs are strategically located around the world. Users connect to the nearest PoP, minimizing the distance data travels.
The setup speeds up connectivity and makes consistent network performance and reliability across all locations possible.
MPLS migration to SD-WAN
Migrating from MPLS to SD-WAN through SASE is a strategic move for many organizations.
Here’s why:
Traditional MPLS networks are known for their high cost and inflexibility. They require major capital investment and extended deployment periods that can hinder an organization's agility and scalability.
Fortunately, secure access service edge provides an efficient pathway from MPLS to a more scalable, cost-effective SD-WAN architecture.
Here’s how:
By using the internet to create secure, high-performance network connections.
The migration allows for the use of broadband internet connections, which are far less expensive and more flexible than MPLS links.
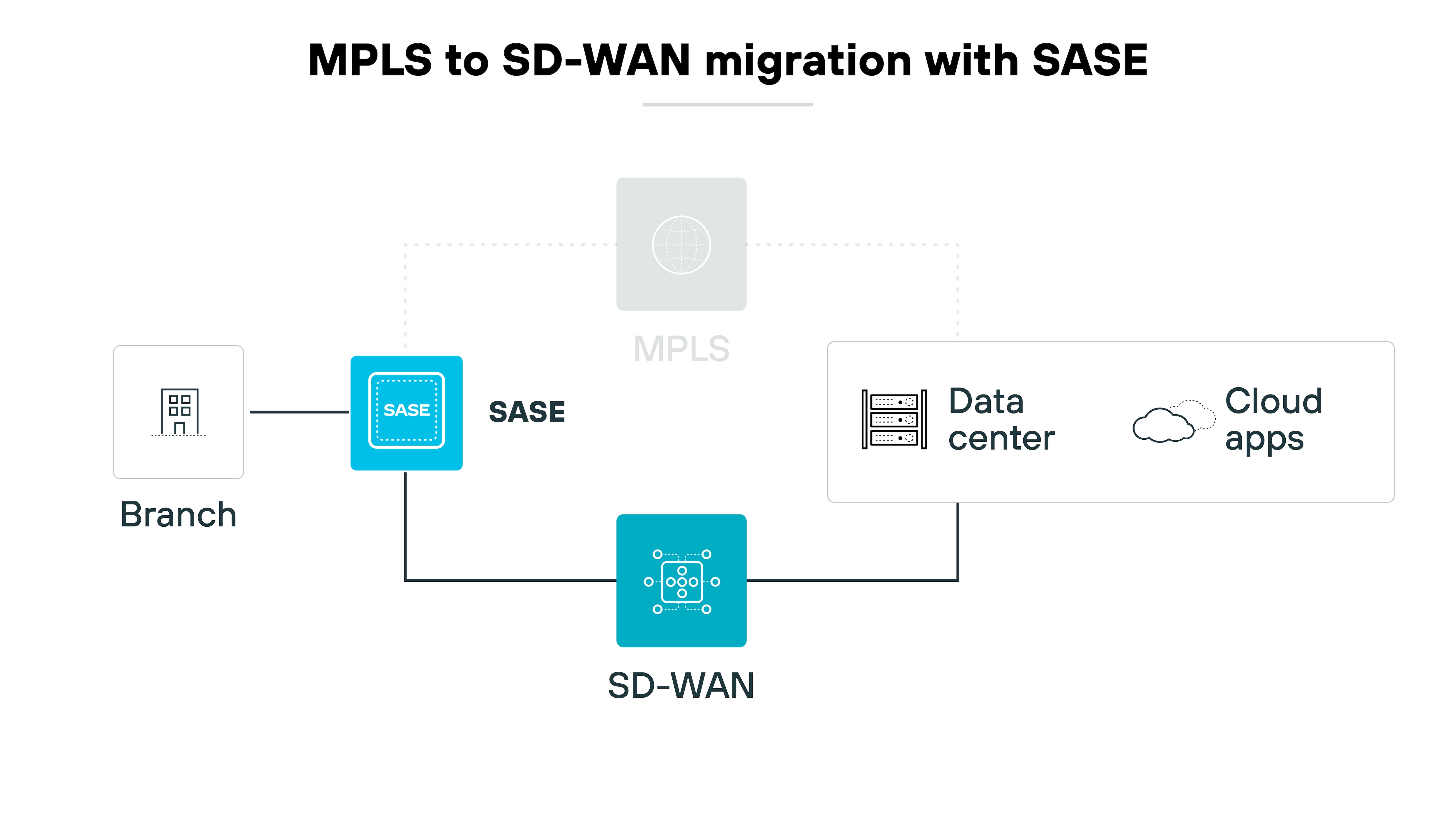
So, once an organization connects to the SASE architecture, it benefits immediately from increased network agility and improved resiliency.
That’s because it optimizes performance and maximizes throughput to on-premises applications and cloud services.
The deployment process is also faster and more streamlined compared to traditional MPLS, typically taking only a few days or even hours.
What are the benefits of SASE?
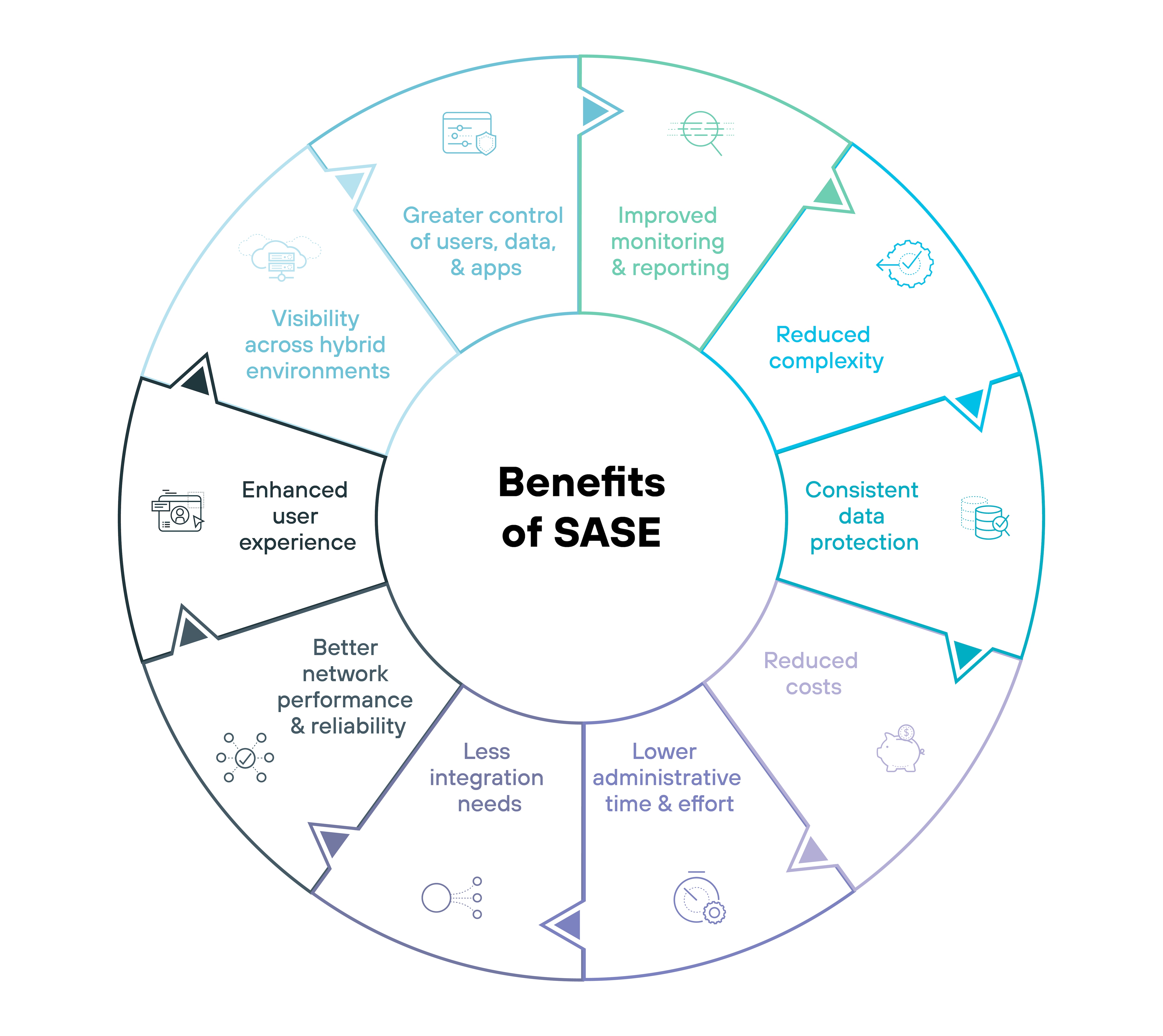
Visibility across hybrid environments: SASE provides visibility of hybrid enterprise network environments, including data centers, headquarters, branch and remote locations, and public and private clouds. This visibility extends to all users, data, and applications, accessible from a single pane of glass.
Greater control of users, data, and apps: By classifying traffic at the application layer (Layer 7), secure access service edge eliminates the need for complex port-application research and mapping, providing clear visibility into application usage and enhancing control.
Improved monitoring and reporting: Secure access service edge consolidates monitoring and reporting into one platform. This unification allows networking and security teams to correlate events and alerts more effectively, streamlining troubleshooting and accelerating incident response.
Reduced complexity: SASE simplifies networking and security by moving operations to the cloud, reducing the operational complexity and costs associated with maintaining multiple point solutions.
Consistent data protection: Secure access service edge prioritizes consistent data protection across all edge locations by streamlining data protection policies and addressing issues like security blind spots and policy inconsistencies.
Reduced costs: Secure access service edge enables organizations to extend their networking and security stack to all locations in a cost-effective manner, often reducing long-term administrative and operational costs.
Lower administrative time and effort: SASE's single-pane-of-glass management reduces the administrative burden, decreasing the time and effort required to train and retain networking and security staff.
Less integration needs: By combining multiple networking and security functions into a unified cloud-delivered solution, secure access service edge eliminates the need for complex integrations between different products from various vendors.
Better network performance and reliability: SASE improves network performance and reliability by integrating SD-WAN capabilities that support load balancing, aggregation, and failover configurations for various links.
- Enhanced user experience: Digital experience monitoring (DEM) facilitated by secure access service edge optimizes operations and enhances user experiences across locations, without the need for additional software or hardware installations.
What are the potential SASE implementation challenges?
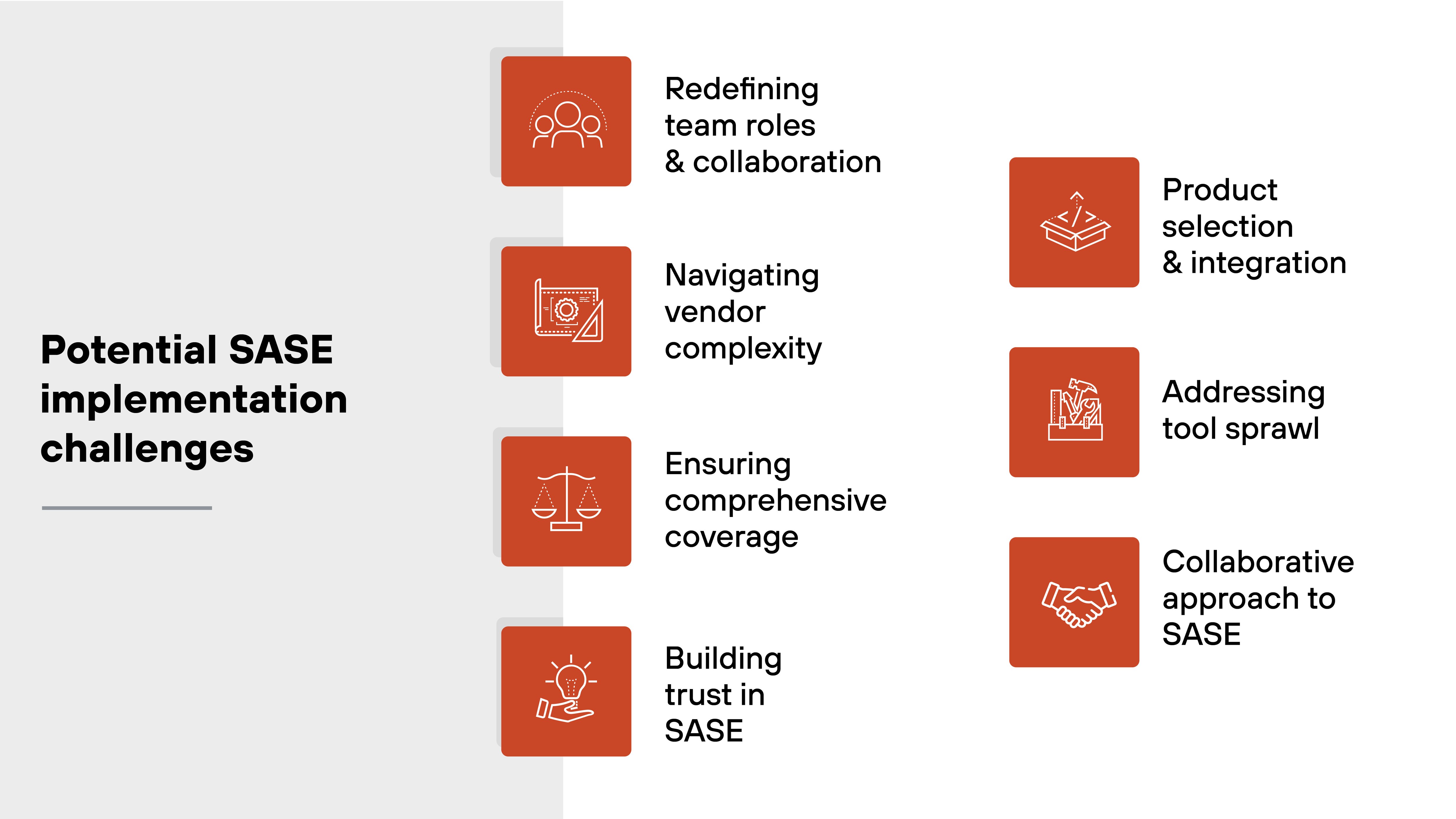
Redefining team roles and collaboration: The implementation of secure access service edge necessitates a re-evaluation of roles within the IT landscape, especially in hybrid cloud setups. Enhanced collaboration between networking and security teams is essential, which can challenge traditional role boundaries.
Navigating vendor complexity: With SASE's ability to combine various tools and methodologies, organizations can more effectively navigate the complex landscape of point products and security tools, aligning with their transformation goals.
Ensuring comprehensive coverage: Secure access service edge offers a consolidated approach, but certain scenarios, particularly in branch-heavy setups, may require a mix of cloud-driven and on-premises solutions to ensure seamless networking and security.
Building trust in SASE: Despite its benefits, some professionals remain wary of transitioning to secure access service edge, particularly in hybrid cloud scenarios. Engaging with reputable SASE providers who have established credibility is crucial.
Product selection and integration: For businesses with siloed IT teams, deploying SASE might involve selecting and integrating multiple products to cater separately to networking and security needs, ensuring complementary functionality for streamlined operations.
Addressing tool sprawl: Transitioning to a cloud-centric secure access service edge model may render certain existing tools redundant. Identifying and mitigating these redundancies is essential to prevent fragmented capabilities and ensure a cohesive technological infrastructure.
Collaborative approach to SASE: The success of a SASE implementation relies on the collaborative efforts of both security and networking professionals. Their combined expertise helps ensure that secure access service edge components align with broader organizational objectives, optimizing the technology's benefits.
How to choose a SASE provider and what to look for
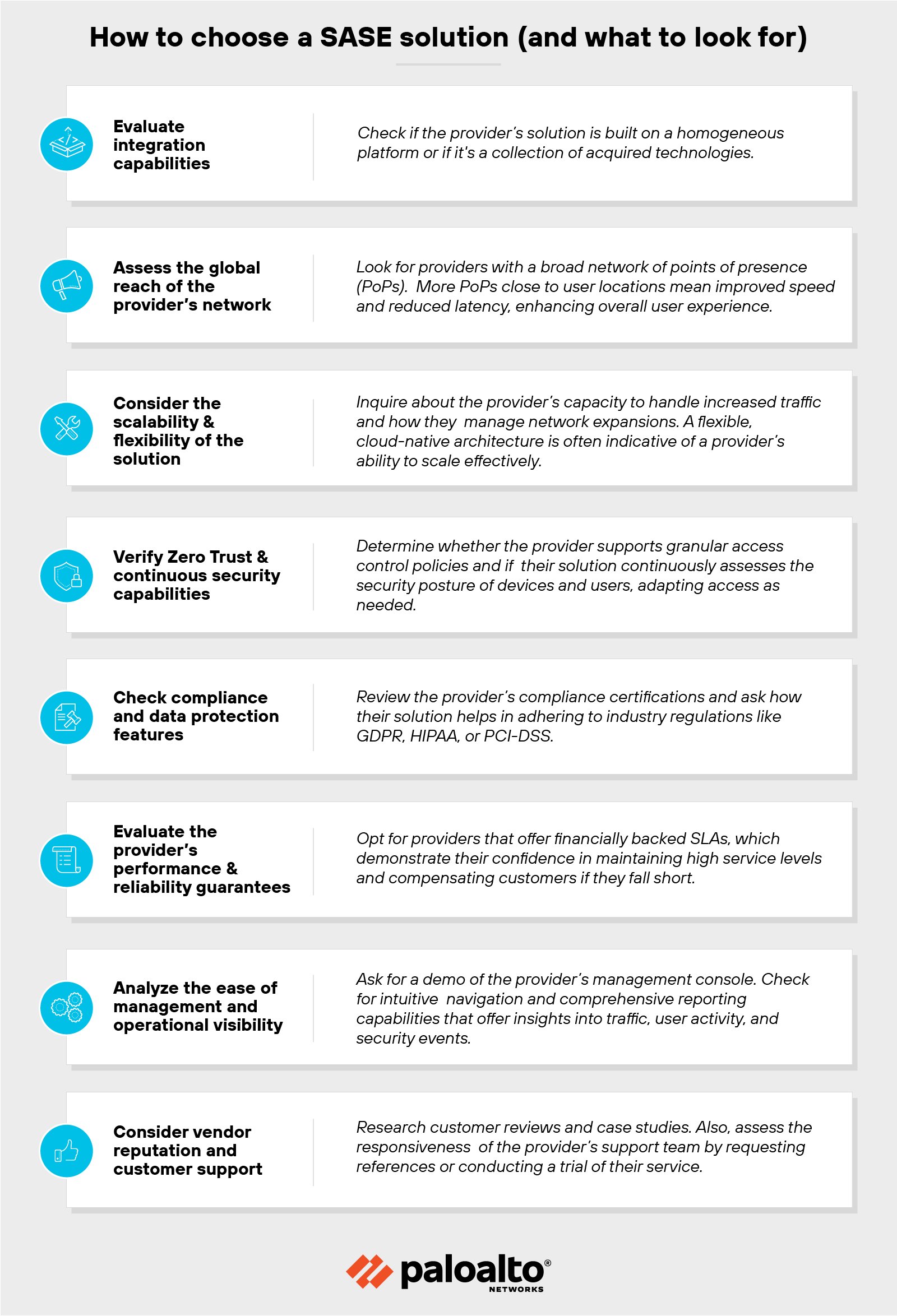
Choosing a SASE provider is a strategic decision that majorly impacts your organization's network security and operational agility.
Here’s how to make an informed choice:
Evaluate the integration capabilities
Because SASE combines numerous network and security functions into a single, unified cloud service, it’s essential to select a provider that offers a truly integrated solution—rather than a bundle of disparate services stitched together.
Integrated solutions offer smoother management and better security efficacy.
Assess the global reach of the provider’s network
SASE services are delivered through the cloud, making the provider’s global presence critical to reducing latency and ensuring users everywhere have reliable and fast access to network resources.
Consider the scalability and flexibility of the solution
As your business grows, your network needs will evolve. A SASE provider should offer scalable solutions that can grow with your business without requiring significant additional investments in hardware or changes to the existing infrastructure.
Verify Zero Trust and continuous security capabilities
Zero Trust is a foundational principle of SASE, focusing on continuous verification of trust before granting access to any resource. Ensure that the solution incorporates real-time, context-based policy enforcement.
Check compliance and data protection features
For businesses in regulated industries, compliance with relevant standards and regulations is non-negotiable. SASE providers should not only comply with these standards but also help you comply through robust data protection and security measures.
Evaluate the provider’s performance and reliability guarantees
Look into the service level agreements (SLAs) offered by the SASE provider. SLAs are a testament to the provider’s commitment to uptime, reliability, and performance.
Analyze the ease of management and operational visibility
Effective management and visibility across all network and security services are crucial. A good SASE solution offers a centralized dashboard for monitoring and managing the distributed network.
Consider vendor reputation and customer support
A provider’s reputation in the market can be a good indicator of their service quality and customer satisfaction. Also, responsive and knowledgeable customer support is vital, especially when deploying complex solutions like SASE.
How to execute a successful SASE implementation in 6 steps
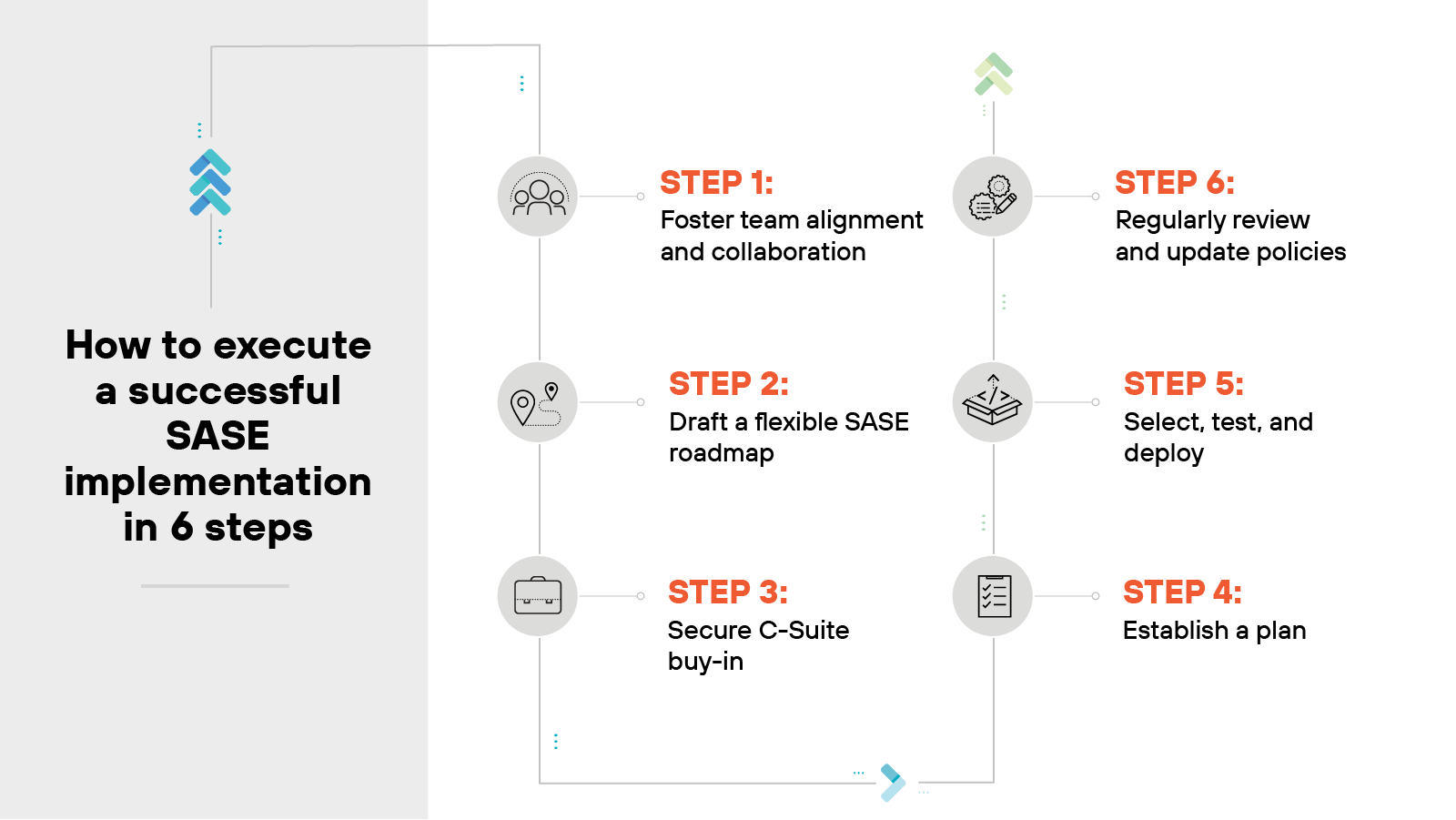
Implementing SASE effectively requires a structured approach and a keen focus on collaboration and strategic planning.
Let’s outline a six-step process to guide your organization through a successful deployment:
Step 1: Foster team alignment and collaboration
To effectively implement SASE, networking and security teams absolutely have to collaborate closely.
Historically, these teams have had differing priorities: networking focuses on speed, security emphasizes threat protection.
Using DevOps evolution as a model, combine these teams' strengths for a unified goal.
Rely on expert leadership and SASE vendors for education and training support to merge disciplines.
Step 2: Draft a flexible SASE roadmap
Adopting SASE doesn't mean you need to do an instant overhaul.
Integrate secure access service edge progressively, aligned with IT initiatives and business goals. And definitely collaborate with vendors or MSPs in developing a roadmap so you can be sure it’s adaptable to dynamic business needs.
Whether you’re modernizing SD-WAN or enhancing security, use SASE as a vehicle for both convergence and progression.
Step 3: Secure C-Suite buy-in
Achieving executive support for SASE is vital.
Highlight the benefits akin to cloud-based applications, stress the ROI, and underscore the reduced need for multiple vendors.
Important: Emphasize the comprehensive security the model brings, particularly in the face of escalating threats.
As projects progress, measure and report successes across various metrics.
Step 4: Establish a plan
Start by clearly determining SASE objectives tailored to your organization's unique challenges.
Then analyze the existing network setup, identify areas of improvement, and conduct a skills and technology audit to make sure your team is prepared for the transition.
Step 5: Select, test, and deploy
Identify and onboard apt SASE solutions that are compatible with existing technologies.
Prioritize solutions that seamlessly integrate with your current tools.
Don’t forget: Before full-scale deployment, test them in a controlled environment to guarantee efficiency.
Step 6: Monitor, optimize, and evolve
Once deployed, maintain strong support mechanisms. Continuously evaluate the SASE setup, adjusting based on feedback, emerging tech trends, and the organization's shifting needs.
What are the most common SASE myths?

For all of its benefits, there are still plenty of misconceptions and myths about SASE.
Probably because it’s still relatively new, so the concept is evolving. Also, traditional network and security models are typically more compartmentalized, making SASE's comprehensive and converged approach seem unfamiliar and sometimes overly broad.
The confusion is often compounded by aggressive marketing that may stretch or oversimplify what secure access service edge actually encompasses.
So—let’s clarify a few common SASE myths and provide a clearer picture of what SASE really offers:
SASE is a cloud-based VPN.
SASE is just a slight improvement on SD-WAN.
Only large corporations benefit from SASE.
SASE solutions are exclusive to remote environments.
SASE compromises on-premises security for cloud advantages.
Adopting SASE means foregoing other security technologies.
SASE is a cloud-based VPN.
SASE provides a comprehensive suite of network and security services beyond the scope of a traditional VPN.
Since it incorporates various functionalities, SASE offers a unified platform for extensive security and network needs. Which far surpasses the capabilities of a standard VPN.
SASE is just a slight improvement on SD-WAN.
SASE is definitely not just an upgrade to SD-WAN with a few security features.
In reality, secure access service edge marks a fundamental change in integrating cloud networking and security. By merging scalable networking with role-based security into one service, it removes the need to manage several systems and vendors.
The approach really does represent a significant transformation. It moves businesses toward a more unified, easily managed network security model. And the change is revolutionary because it introduces a scalable, agile framework.
Only large corporations benefit from SASE.
Businesses of all sizes can harness the advantages of SASE. Even for small to medium-sized organizations, SASE can absolutely simplify network and security management.
Plus: Its scalability ensures that organizations can adapt it to their unique requirements and growth trajectory.
SASE solutions are exclusive to remote work environments.
While SASE is often associated with facilitating remote work because of its secure access capabilities, it's equally beneficial for in-office infrastructures.
Secure access service edge ensures that both remote users and in-office workers have consistent secure access to cloud resources. It defends against threats regardless of physical location.
SASE compromises on-premises security for cloud advantages.
A SASE architecture doesn't mandate an exclusive cloud-centric approach.
Actually, organizations can integrate SASE solutions with on-premises systems—like next-generation firewall appliances—and optimize performance and security based on specific requirements.
Adopting SASE means foregoing other essential security technologies.
Although secure access service edge offers a broad spectrum of security solutions, it doesn't eliminate the need for complementary technologies like endpoint detection and response or cloud workload protection.
Implementing SASE doesn't mean sidelining other crucial security components. It’s about integrating them for a holistic security stance.
How SASE works with complementary technologies
Since SASE has such a flexible architecture, it’s versatile across various applications and environments.
Secure access service edge integrates particularly well with systems that support cloud-based and distributed network architectures.
It can easily work alongside technologies like cloud services, mobile networks, and IoT systems—which benefit from SASE’s ability to provide centralized security management across diverse environments.
Let’s take a look at how SASE works with 5G, IoT, and DLP solutions.
How SASE and 5G work together
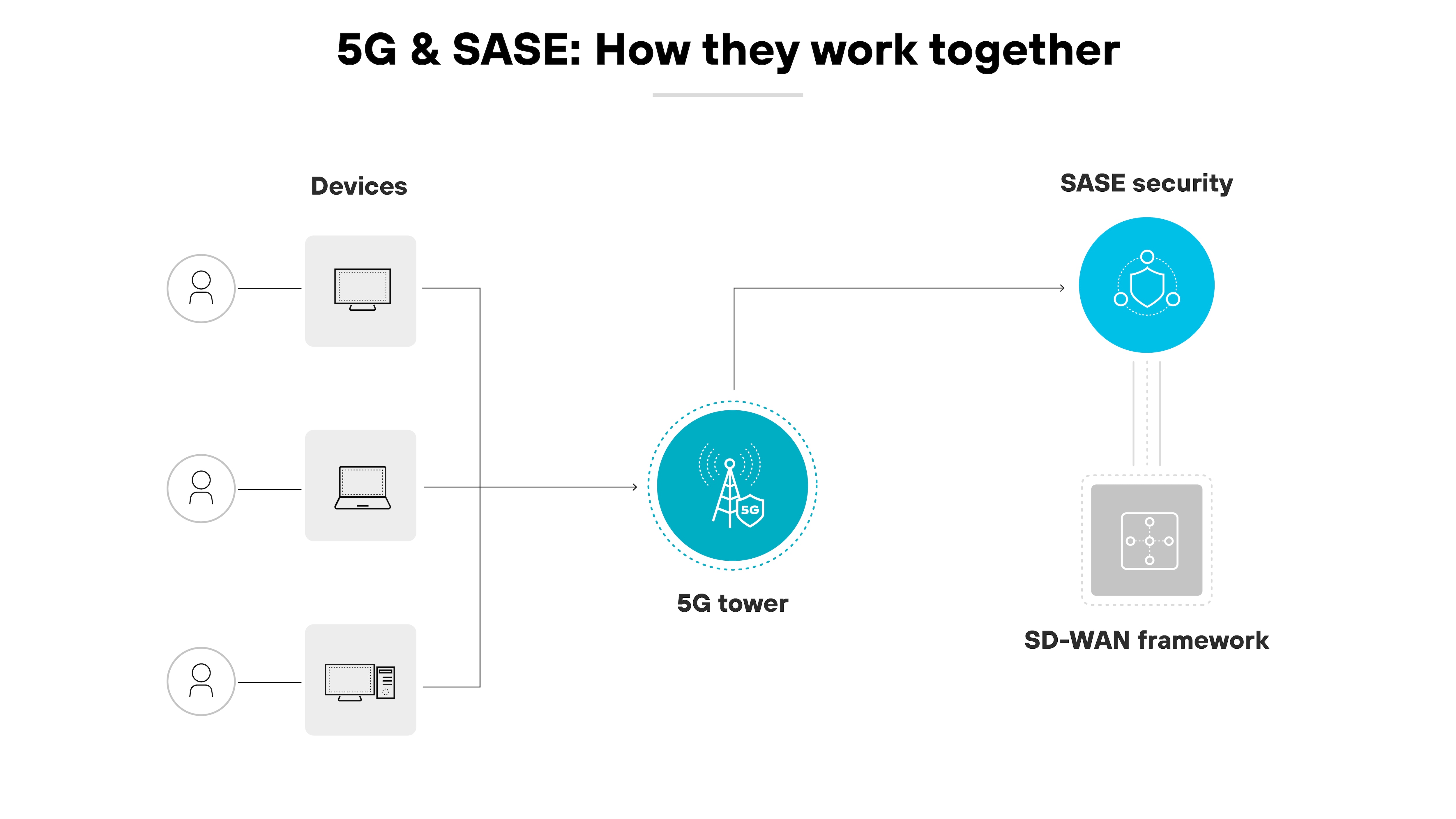
5G revolutionizes mobile networks with speed and reduced latency. And as 5G networks evolve beyond traditional architectures, there's a pressing need to address new security challenges.
SASE is a potential solution because it offers a centralized security framework that’s tailored for the dynamic nature of modern networks.
When integrated with 5G, SASE optimizes the potential of the network without compromising security. By routing 5G traffic through a SASE platform, businesses can enforce consistent security measures and achieve improved operational efficiency.
This way, users can access corporate resources from diverse locations. And each connection undergoes rigorous validation.
The SD-WAN component of SASE further augments this effect.
5G and SASE combine to provide a secure, high-performance framework that facilitates swift, safe communication across extended networks.
How IoT integrates with SASE
Legacy IoT systems rely heavily on centralized service provider networks, which leads to intricate routing and the potential for higher latency.
The extensive spread of IoT devices and data across multi-region clouds exacerbates these issues.
Fortunately, secure access service edge is adept at handling IoT's distributed nature.
By converging virtualized networking and security services, SASE offers centralized policy control. It streamlines data routing and safeguards it regardless of origin or destination.
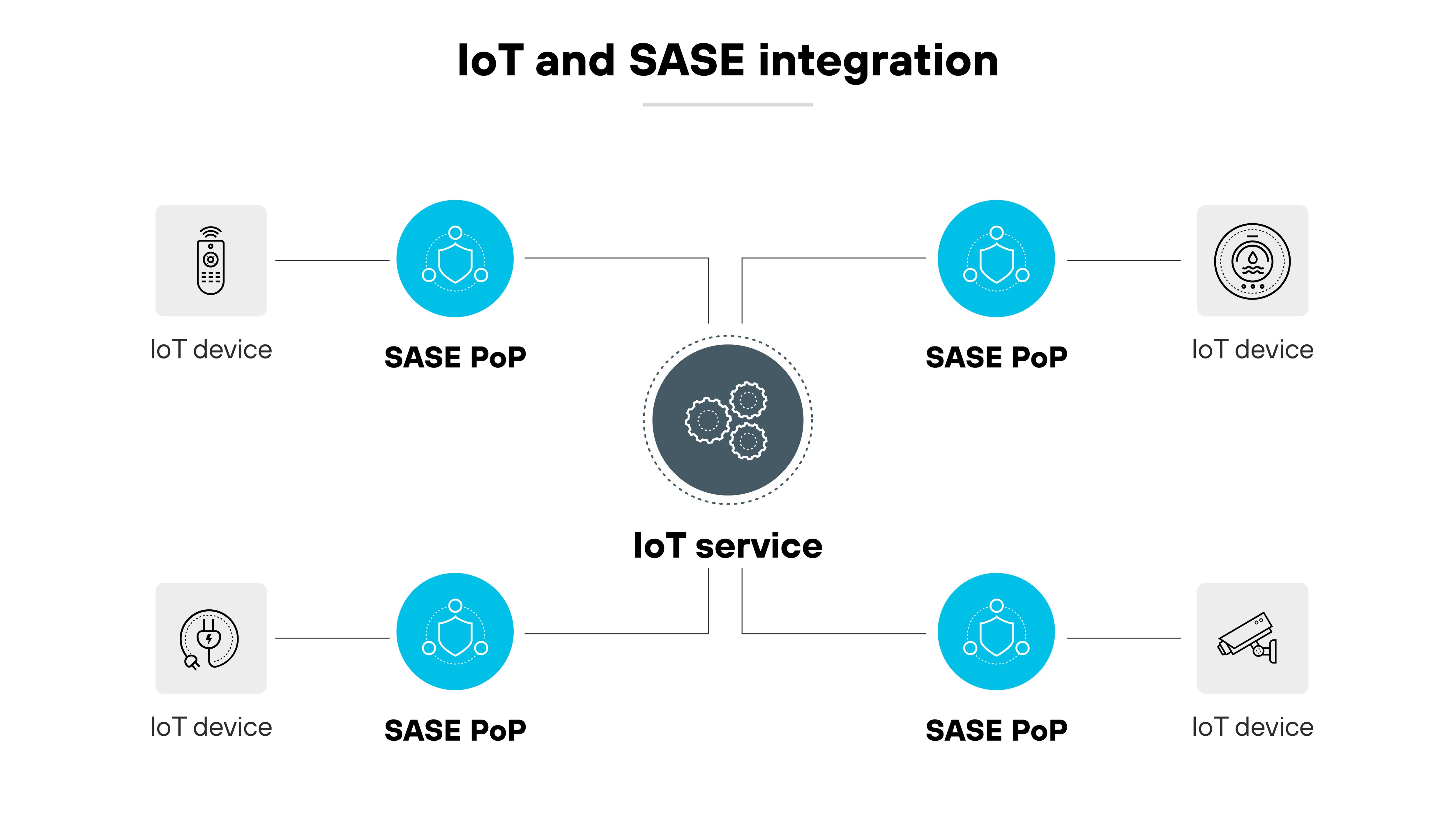
Shifting security closer to data sources, SASE uses distributed points of presence (PoP) to authenticate access based on distinct device attributes. And the decentralized stance enhances IoT security, trims latency, and aligns with regional data regulations.
Protecting data with SASE and DLP
Data resides everywhere—from cloud storages to mobile devices.
And traditional data loss prevention (DLP) methods don’t provide sufficient protection for modern, highly distributed IT environments.
They’re often not agile enough to manage the dispersed nature of data. Which can make the identification and classification of sensitive information challenging.
Here’s where SASE comes in.
It combines DLP and advanced security within a unified cloud-native framework. This setup allows precise security policies to be applied directly to data as it moves across networks.
Not to mention, SASE enhances visibility and control over sensitive data. Which leads to robust protection that adapts seamlessly to complex IT infrastructures and evolving cyber threats.
Comparing SASE with other security and technology solutions
| Feature | SD-WAN | SASE | CASB | ZTE | ZTNA | SSE | Traditional network security | Firewall | Zero Trust | VPN |
|---|---|---|---|---|---|---|---|---|---|---|
| Integration of networking and security | Limited; primarily focuses on connectivity | Comprehensive; integrates networking with a broad range of security services | Limited to cloud applications | Integrates networking with cloud-centric security | Part of the broader SASE framework | Focuses on security, less on networking | Separate; traditional setups do not integrate both | Limited; mainly filters traffic | Security approach that can be part of broader solutions | Primarily provides secure network access |
| Deployment focus | Branch office connectivity | Seamless connectivity across various environments | Security for SaaS applications | Amalgamation of network features and cloud-centric security | Specific security model focusing on access control within SASE | Security services like SWG, CASB, and ZTNA without networking elements | Based on a fixed, secure perimeter typically within physical premises | Acts as a network gatekeeper | Ensures that every access request is authenticated and authorized | Secure connections through centralized servers |
| Primary benefit | Optimizes and manages distributed network connections | Secure and optimized connectivity for diverse environments including mobile and cloud | Extends security to cloud-based deployments | Focus on Zero Trust as a comprehensive service | Ensures rigorous validation of access requests | Streamlines various security measures under one control | Relies on physical hardware and location-based defenses | Controls traffic based on predefined rules | No implicit trust; rigorous continuous verification | Encrypts connections to protect data in transit |
| Suitability for modern work environments | Suitable for traditional office setups | Highly suitable for remote and dispersed teams | Suitable for organizations heavily using SaaS | Suitable for organizations adopting a Zero Trust framework | Integral to secure remote access in modern work environments | Addresses security in edge and remote environments | Less suitable due to fixed perimeter becoming redundant | Basic traffic filtering less suitable for complex digital landscapes | Essential for ensuring security in decentralized networks | Suitable but can introduce latency due to central server reliance |
- SASE vs. CASB: What Is the Difference?
- SASE vs. SSE: What Is the Difference?
- SASE vs. Firewall: What Is the Difference?
- SASE vs. VPN: What Is the Difference?
- How Zero Trust and SASE Can Work Together
- SASE vs. ZTE: What Is the Difference?
- SD-WAN vs. SASE: What’s the Difference?
- SASE and Secure Web Gateway: How Are They Related?
- SD-WAN vs. SASE vs. SSE: What Are the Differences?
What is the history of SASE?
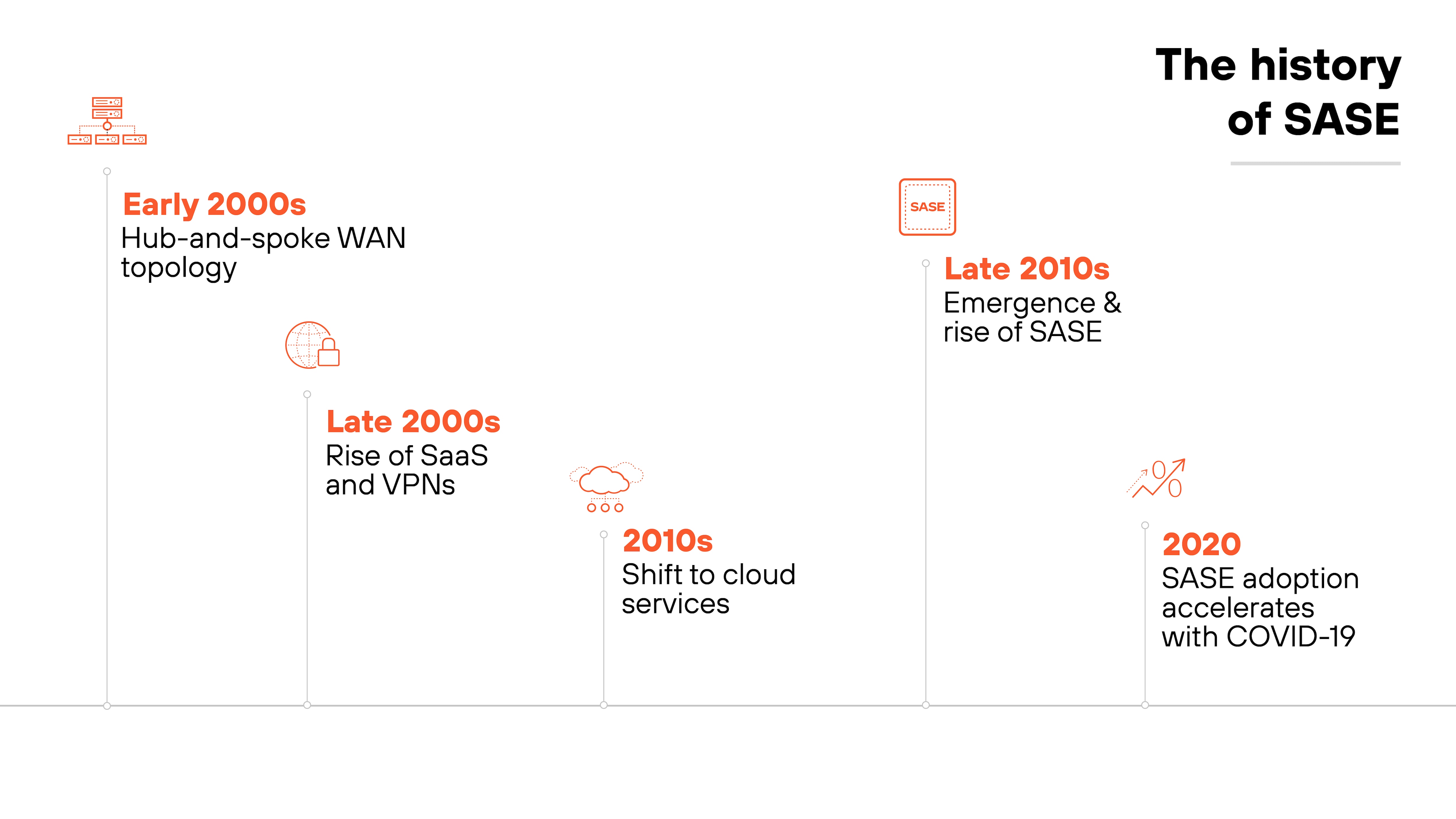
Historically, companies relied on a hub-and-spoke wide area network (WAN) topology, with centralized servers and costly lines connecting remote offices.
As software-as-a-service (SaaS) applications and virtual private networks (VPNs) became popular, businesses transitioned applications to the cloud.
Firewalls in branch offices began enforcing security policies while optimizing traffic.
With the growth of cloud services, the dependency on on-premises resources diminished. Which meant that the inefficiencies of traditional network access became evident.
To address these challenges, SASE technology emerged, integrating multiple network and security technologies into one solution.
The shift towards integrated network and security solutions became crucial as key SaaS applications, such as Microsoft Office 365, moved to Azure, driving the need for more effective traffic management and inspection.
The COVID-19 pandemic accelerated the adoption of SASE as remote work surged and secure networking became paramount.
- SD-WAN
- SWG
- CASB
- FWaaS
- ZTNA

