Overview
As the world’s cybersecurity leader, our technologies give our enterprise customers the power to protect billions of people worldwide. Our products are designed with the highest security assurance standards in all aspects of a product lifecycle to help deliver highly trusted and secure products. Our product security assurance practices are based on recognized international standards such as ISO/IEC 29147:2018 (vulnerability disclosure), ISO/IEC 30111:2019 (vulnerability handling) and FIRST PSIRT Services Framework 1.0.
We are deeply committed to help ensure the safety and security of our customers. Our policies and practices are guided by our core corporate values of disruption, execution, collaboration, integrity, and inclusion.
Scope
Palo Alto Networks’ product security assurance practices cover all our products that have not reached the End-of-Life (EoL) milestone. These include hardware, software and SaaS products (cloud services) and products delivered by our wholly-owned subsidiaries. This policy also covers any open source project such as those hosted at https://github.com/PaloAltoNetworks, unless stated otherwise.
Product Security Incident Response Team
Reporting Vulnerabilities
Vulnerabilities in our products can be reported to our PSIRT in different ways:
We honor Traffic Light Protocol (TLP) labels when sensitive information is shared with us. Any sensitive non-public information about vulnerabilities is considered highly confidential, and only individuals from PSIRT and product engineering who have a legitimate need to know and may add value to the remediation processes get access to this information.
To help protect our customers, we request that you not post or share any information about a potential vulnerability in any public setting until we have researched, responded to, and addressed the reported vulnerability, and if needed, inform customers through a security advisory.
Please submit requests for adding signatures to detect or block new or variations of attacks or malware directly to customer support. We encourage security researchers and software vendors to send us vulnerability information that can help us provide better protections to customers faster. Palo Alto Networks is a member of the Microsoft Active Protections Program (MAPP).
Issues in Palo Alto Networks IT infrastructure should be reported to https://paloaltonetworks.responsibledisclosure.com
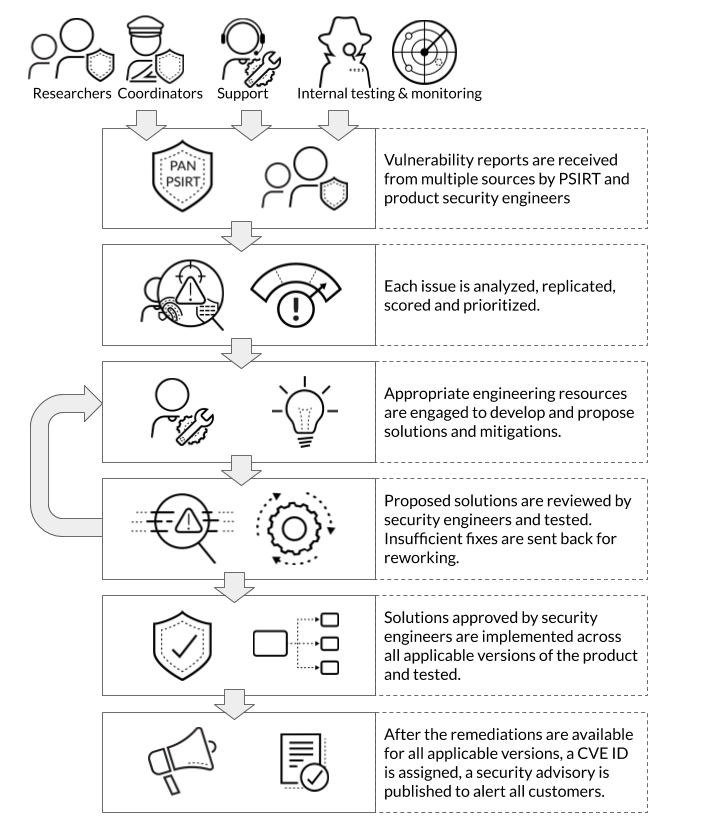
Palo Alto Networks PSIRT oversees the entire vulnerability response and remediation process from start to finish across all products. When remediation of an issue is completely in our hands, our SaaS products (cloud services) are fixed in a matter of hours or days. Our on-premise products that have a regular maintenance release and test schedules are completely resolved to the best of our ability well within 90 days for most issues.
Secure software development and maintenance
Security by Design: Palo Alto Networks applies secure by design principles throughout the software development lifecycle. Our comprehensive approach to securing our customers and our company including our products and services is detailed in our Trust 360 Program Document.
Response Prioritization
Any vulnerability with active exploitation (“0-day”) against Palo Alto Networks or publicly known vulnerabilities with high exploitation potential would be responded with utmost urgency.
We remediate and publish advisories for vulnerabilities irrespective of who found them. Issues may be discovered by external researchers, found during internal testing, encountered by customers or reported by other organizations and vendors.
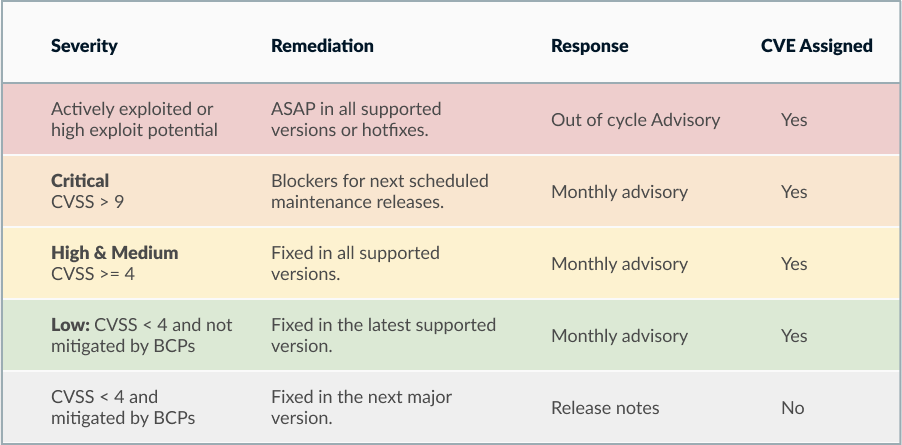
Any issues that have a low severity rating with CVSS base score less than 4.0 and can be easily mitigated with current best practices, or security improvements or defensive programming fixes with no real or proven impact to customers are usually addressed in future releases of our products and do not necessarily result in a security advisory. Such issues are documented in our informational bulletins or in product release notes.
There can be exceptional issues which cannot be sufficiently fixed or mitigated in a reasonable timeline. Such issues may require actions by standardization organizations, or depend on an upstream organization to deliver fixes or require inventing a new hardware architecture. In such cases, we may publish an advisory with possible mitigations and workarounds, but no remediations involving a product change.
Multiparty Vulnerability Coordination
Security Advisories
We publish security advisories to warn customers about security vulnerabilities in our products at https://security.paloaltonetworks.com/. Our advisories may include information about the affected versions, worst-case impact, required configurations, any available workarounds, fixed versions, CVE IDs, CWE IDs, CVSS scores, CPE Names, and acknowledgements to persons discovering the issue. We aim to avoid including information that may help miscreants exploit the vulnerabilities.
Except for critical issues with active exploitation, security advisories are published only after fixes are available for all supported releases of a product on a predetermined monthly schedule. Advisories are published on the second Wednesday of every month at 09:00 AM Pacific Standard Time.
When possible Palo Alto Networks Focused Services team is briefed about upcoming security advisories to provide personalized support, release review and upgrade planning assistance to customers. Partners leveraging Palo Alto Networks products to secure important critical infrastructure are proactively informed about product vulnerabilities.
Advisories for any critical issues with active exploitation are published out of cycle as soon as practicable.
We do not publish advisories for general security improvements and defensive programming fixes that do not have a proven security impact.
We do not publish advisories for vulnerabilities in our SaaS (cloud services) products when an issue can be completely resolved by Palo Alto Networks, without requiring any customer action. We may publish a maintenance log of resolved vulnerabilities that are updated when issues are resolved. For vulnerabilities affecting both our SaaS and on-premise products, we aim to upgrade all SaaS deployments before issuing an advisory to minimize customer risk.
![]() Palo Alto Networks is a CVE Numbering Authority (CNA). Our CVE assignment scope includes all Palo Alto Networks products and vulnerabilities discovered in any third-party product not covered by another CNA. We adhere to the CNA Operational Rules to identify, define, catalog, and share information about our disclosed vulnerabilities using CVE IDs and CVE Records.
Palo Alto Networks is a CVE Numbering Authority (CNA). Our CVE assignment scope includes all Palo Alto Networks products and vulnerabilities discovered in any third-party product not covered by another CNA. We adhere to the CNA Operational Rules to identify, define, catalog, and share information about our disclosed vulnerabilities using CVE IDs and CVE Records.
Customers can subscribe to email notifications of new security advisories and important updates. Customers can also subscribe to our security advisories RSS feed using their preferred RSS reader or any other software they use to receive RSS feed updates (eg: Slack). All published vulnerabilities get a CVE ID assigned and entered into the CVE corpus, as well as in the National Vulnerability Database.
Acknowledgement Policy