- What Is Insecure System Configuration?
-
What Is SDLC Security?
- SDLC Security Overview
- Security Across the Classic SDLC Phases
- Common Vulnerabilities and Attack Vectors in the SDLC
- Foundational Secure-SDLC Practices
- Tooling and Automation Layers
- Frameworks and Standards for Secure SDLC
- DevSecOps Integration
- Metrics and Continuous Improvement
- Advancements in Software Supply Chain Defense
- Roadmap to Secure-SDLC Maturity
- SDLC Security FAQs
- What Is Inadequate Identity and Access Management?
- What Is Ungoverned Usage of Third-Party Services?
- What Is the CI/CD Pipeline?
-
What Is a Software Bill of Materials (SBOM)?
- Software Bill of Materials Explained
- Who Should Have a SBOM
- The Role of SBOMs in Cybersecurity and Compliance
- Why Is an SBOM Important?
- Software Composition Analysis and SBOMs
- How Does an SBOM Help Prevent Open-Source Supply Chain Attacks
- SBOM Formats
- Software Bill of Materials Best Practices
- SBOM FAQs
- What Is Software Composition Analysis (SCA)?
- What Is Static Application Security Testing (SAST)?
- What Is Code Security?
- What Is Container Runtime Security?
- What Is Poisoned Pipeline Execution (PPE)?
- What Is Insufficient Pipeline-Based Access Controls?
- What Is Insufficient Logging and Visibility?
-
What Is Insufficient Flow Control Mechanisms?
- CICD-SEC-1: Insufficient Flow Control Mechanisms Explained
- Importance of Robust Flow Control Mechanisms in CI/CD
- Preventing Insufficiency in Flow Control Mechanisms
- Best Practices to Ensure Sufficient Flow Control in CI/CD
- The Impact of New Technologies on Flow Control
- Insufficient Flow Control Mechanisms FAQs
- What Is Insufficient Credential Hygiene?
- What Is Improper Artifact Integrity Validation?
- How to Transition from DevOps to DevSecOps
- What Is Dependency Chain Abuse?
-
Anatomy of a Cloud Supply Pipeline Attack
What Is CI/CD Security?
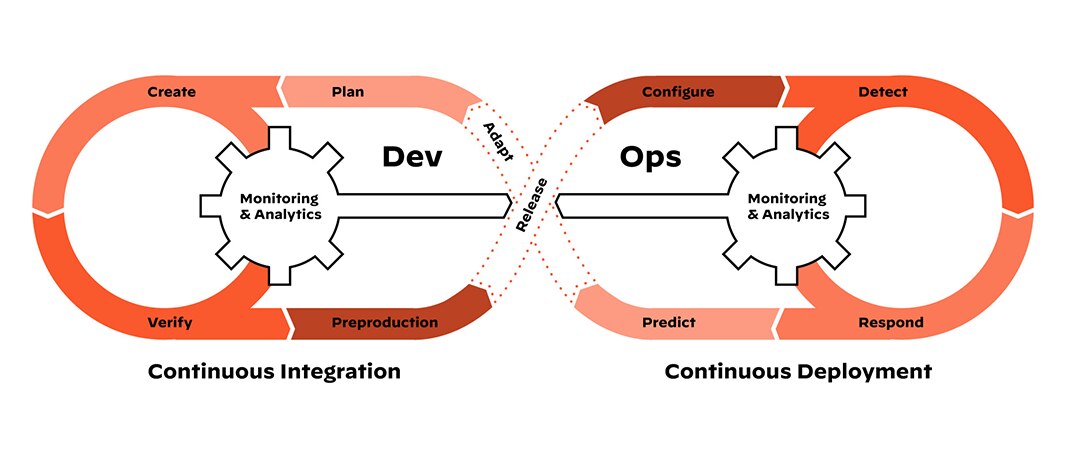
CI/CD security is the distribution of security practices and measures throughout the continuous integration and continuous delivery (CI/CD) pipeline. As a core component of DevSecOps, CI/CD security dismisses the idea that security is a distinct phase and instead ensures it is an inherent part of the software delivery lifecycle. The goal of CI/CD security is to detect and mitigate vulnerabilities, reduce risks, and promote secure coding practices.
CI/CD Security Explained
Continuous integration and continuous deployment (CI/CD) refers to the automated workflow that enables organizations to deliver software more efficiently by allowing rapid and frequent integration, testing, and deployment of code changes. Of importance to developers and enterprises alike, CI/CD security refers to the set of practices, processes, and technologies implemented to ensure the security and integrity of the CI/CD pipeline.
Components of CI/CD security include:
- Static application security testing (SAST) scans source code for known vulnerabilities early in the development process.
- Dynamic application security testing (DAST) checks running applications for vulnerabilities, typically toward the end of the CI/CD pipeline.
- Software composition analysis (SCA) inspects open-source components for vulnerabilities.
- Secrets management ensures sensitive data like API keys, credentials, and certificates are securely handled.
- Container security checks container configurations, dependencies, and runtime behaviors for vulnerabilities.
- Infrastructure as code (IaC) security analyzes infrastructure scripts for misconfigurations or violations of security policies.
CI/CD security encompasses managing secrets and sensitive data, implementing access controls, and conducting security testing throughout the CI/CD pipeline. It aims to protect against potential attacks that could compromise the integrity, confidentiality, or availability of the software developed and deployed by organizations.
Securing the pipeline serves as the backbone of the software development process. By ensuring the security of the pipeline, organizations maintain the trust of their users, safeguard sensitive information, and prevent security breaches.
Why CI/CD Security Is Critical
The CI/CD pipeline is an attractive target for attackers. As a centralized and automated process that handles code changes and deployments, any security flaws in the pipeline could lead to unauthorized access of the system. Bad actors know this and look for vulnerabilities. CI/CD security prevents attackers from injecting malicious code or creating backdoors and causing data loss and systems compromise.
The fast-paced nature of CI/CD and the continuous integration of code changes can amplify security risks. Without proper security controls, vulnerabilities can propagate quickly through the pipeline, making them challenging to identify and mitigate. Additionally, the reliance on open source and third-party components within the CI/CD process introduces security risks into the software supply chain.
As the axis of the application engineering ecosystem, the CI/CD pipeline must take top priority for organizations to ensure the confidentiality, integrity, and availability of their cloud-native applications. Failing to do so puts organizations at risk of financial loss, reputational damage, and regulatory noncompliance.
A secure CI/CD pipeline not only safeguards the organization’s intellectual property and sensitive data but also ensures the continuous deployment of high-quality software, cultivating a competitive edge in today's evolving digital landscape.
Related: Protecting Your Delivery Pipeline: Extensive CI/CD Security
CI/CD Security Threats
Understanding the threats that can exploit vulnerabilities — from insufficient flow control mechanisms to improper artifact integrity — informs the development of robust strategies to mitigate them. By preparing for the OWASP Top 10 CI/CD security risks, you can enhance your pipeline's security posture.
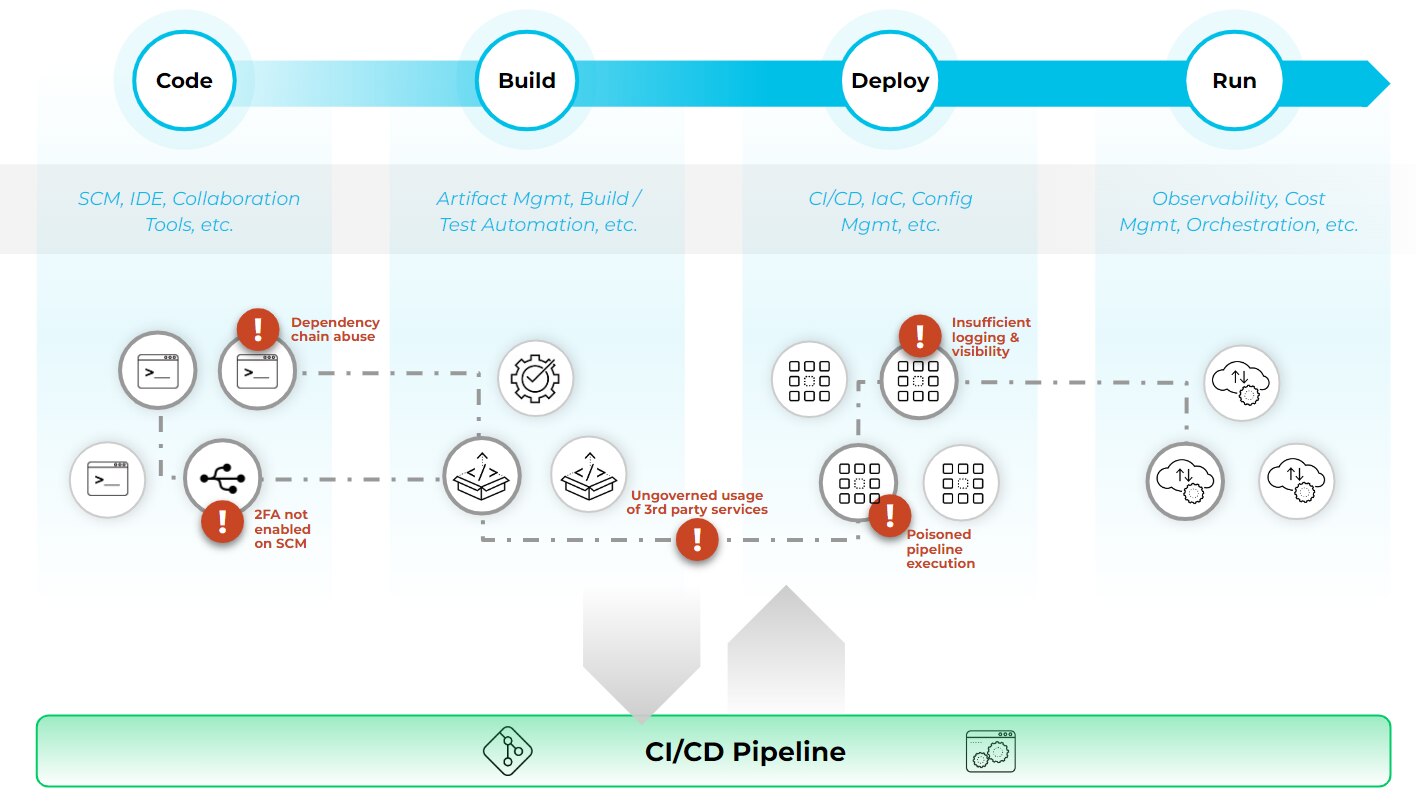
CICD-SEC-1: Insufficient Flow Control Mechanisms
Insufficient flow control mechanisms refer to the lack of proper checks and controls throughout the CI/CD pipeline. Without adequate validation and authorization mechanisms, attackers can manipulate the flow of code changes, inject malicious code, or bypass security measures, leading to unauthorized access or unauthorized deployments.
CICD-SEC-2: Inadequate Identity and Access Management
Inadequate identity and access management in the CI/CD pipeline can result in unauthorized individuals gaining access to critical resources, such as source code repositories, build servers, or deployment environments. Insufficient access controls can allow attackers to tamper with code, introduce vulnerabilities, or exfiltrate sensitive information.
CICD-SEC-3: Dependency Chain Abuse
Dependency chain abuse occurs when an attacker exploits flaws in how engineering workstations and build environments fetch code dependencies. This exploitation ultimately leads to fetching and locally executing malicious packages from public repositories, specifically targeting popular packages within CI/CD pipelines.
CICD-SEC-4: Poisoned Pipeline Execution (PPE)
Poisoned pipeline execution refers to an attack where a hacker compromises the CI/CD pipeline to execute malicious code during the build or deployment process. By injecting malicious scripts or tampering with the pipeline configuration, attackers can manipulate the software in build or deployment, leading to the introduction of malicious code, data breaches, or system compromise.
CICD-SEC-5: Insufficient Pipeline-Based Access Controls
Insufficient pipeline-based access controls refers to the lack of effective access controls within the CI/CD pipeline. Without proper authorization mechanisms, attackers can gain unauthorized access to critical components, modify pipeline configurations, or compromise the integrity of the software being built or deployed.
CICD-SEC-6: Insufficient Credential Hygiene
Insufficient credential hygiene involves improper management and protection of credentials used within the CI/CD pipeline. Hard-coded secrets, weakly stored or transmitted credentials, or the exposure of sensitive information can provide attackers with the means to escalate privileges, impersonate legitimate users, and compromise the security of the pipeline.
CICD-SEC-7: Insecure System Configuration
Insecure system configuration refers to the presence of misconfigured components or systems within the CI/CD pipeline. Misconfigurations can lead to security vulnerabilities, such as open ports, weak encryption, or unnecessary services — all of which attackers can exploit to gain unauthorized access or perform malicious activities.
CICD-SEC-8: Ungoverned Usage of Third-Party Services
The ungoverned usage of third-party services within the CI/CD pipeline introduces security risks. Integrating external services without proper oversight or vetting can expose the pipeline to vulnerabilities that compromise the integrity of the software. Attackers may target these services to gain unauthorized access, inject malicious code, or exfiltrate sensitive data.
CICD-SEC-9: Improper Artifact Integrity Validation
Improper artifact integrity validation involves insufficient checks to ensure the integrity and authenticity of software artifacts within the CI/CD pipeline. Without proper validation mechanisms, attackers can manipulate or replace artifacts, leading to the deployment of compromised or malicious software.
CICD-SEC-10: Insufficient Logging and Visibility
Insufficient logging and visibility hinder the ability to detect and respond to security incidents within the CI/CD pipeline. Without comprehensive logging, monitoring, and auditing, it becomes challenging to identify anomalous behavior, track changes, or investigate security events. When effectively executed, this CI/CD risk enables attackers to operate undetected and cover their tracks.
Securing the CI/CD Pipeline
Securing the CI/CD pipeline involves implementing a range of security practices and technologies to protect the integrity and confidentiality of the software development and deployment process.
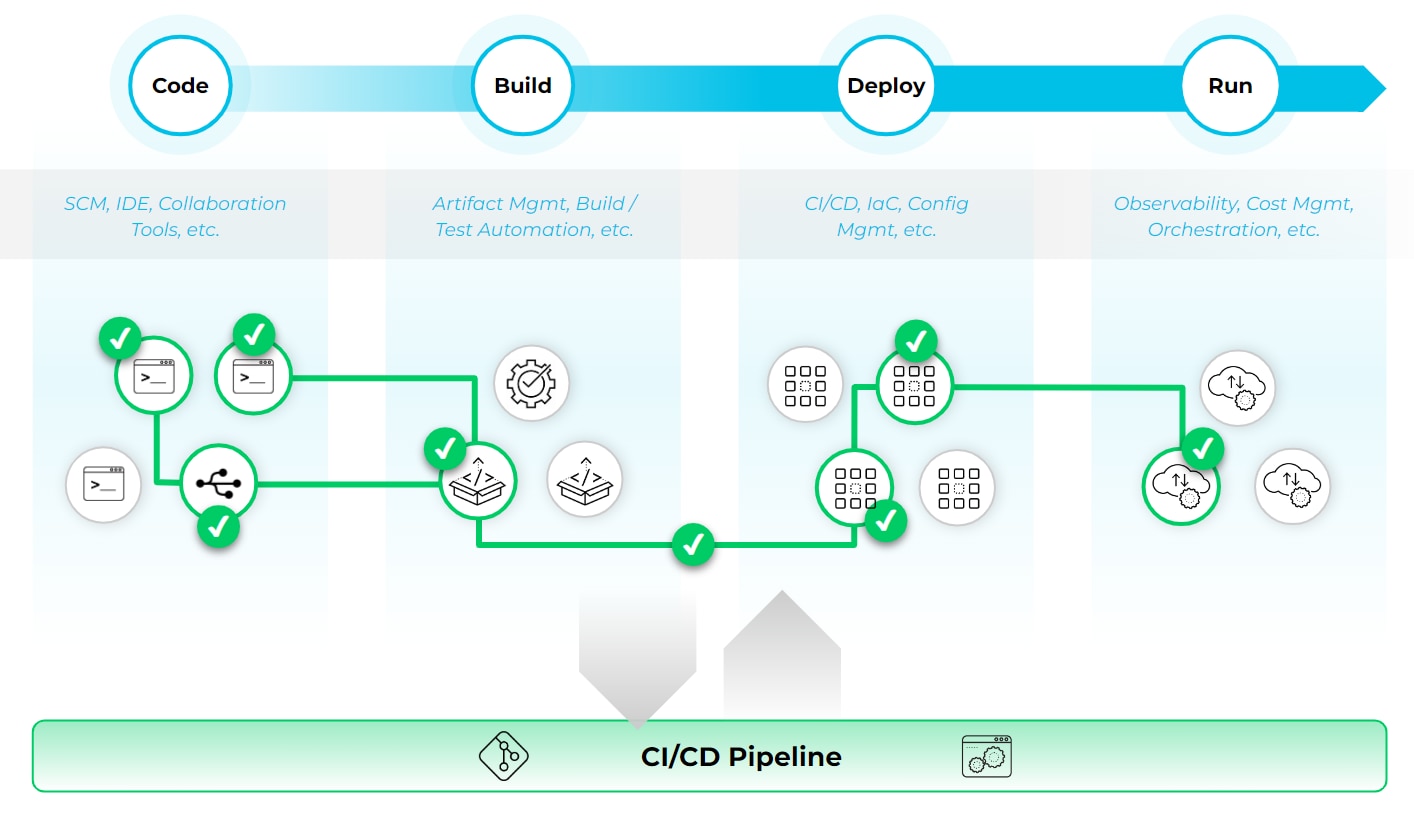
Source Composition Analysis
Source composition analysis (SCA) is a crucial security practice in the CI/CD pipeline. It involves analyzing and scanning the source code and dependencies to identify any known security vulnerabilities or open-source components with known vulnerabilities. By leveraging SCA tools and integrating them into the pipeline, organizations can identify and remediate potential security risks early in the development process.
Static Application Security Testing
Static application security testing (SAST) is another important security practice in CI/CD. Developers conducting SAST analyze the source code to identify security vulnerabilities, coding errors or insecure coding practices. SAST tools scan the codebase, searching for potential security flaws and providing developers with actionable insights to address these issues before deploying the code.
CI/CD Access Controls
Implementing strict access controls throughout the CI/CD pipeline is essential for maintaining security. This includes proper authentication and authorization mechanisms to control access to critical components, such as source code repositories, build servers, or deployment environments. Role-based access control (RBAC), multifactor authentication (MFA), and least privilege principles should be enforced to ensure that only authorized individuals can make changes or access sensitive resources.
Secrets Management and CI/CD
Managing secrets, such as API keys, passwords, or cryptographic keys, is crucial for CI/CD security. Secrets should never be hard-coded or stored in plaintext within the code or configuration files. Instead, DevOps should follow secure secret management practices, such as using a centralized secrets management system or leveraging secure key vaults. Secrets should be encrypted, rotated regularly, and accessed only when necessary.
Registry Scanning
Registry scanning involves analyzing container images used in the CI/CD pipeline to identify known vulnerabilities or misconfigurations. Container security tools can scan the container images for any known security issues or vulnerabilities and provide actionable insights for remediation. This helps ensure that only secure and trusted container images are deployed, reducing the risk of running containers with known vulnerabilities.
Runtime Security
Runtime security focuses on monitoring and protecting the application during its execution in the production environment. Implementing runtime security measures, such as web application firewalls (WAFs), runtime application self-protection (RASP), or behavioral analysis tools, allows organizations to detect and mitigate security threats in real time. By continuously monitoring the application's behavior and enforcing security controls at runtime, organizations can detect and respond to potential attacks promptly.
CI/CD Security Best Practices
By following industry best and DevSecOps practices, organizations can strengthen their overall security posture and ensure the integration of security throughout the software development and deployment process.
Implement Infrastructure as Code
Use infrastructure as code (IaC) principles to define and manage the infrastructure and configuration of the CI/CD pipeline. This approach ensures consistency, version control, and the ability to enforce security controls throughout the pipeline's infrastructure components.
Apply Secure Coding Practices
Secure coding practices — input validation, output encoding, proper error handling, and secure authentication and authorization mechanisms — are invaluable to development teams. Keeping software dependencies up to date and avoiding the use of deprecated or insecure functions also goes a long way toward preventing SQL injection, cross-site scripting (XSS), and buffer overflows. Security-focused code reviews and secure coding training can reinforce these practices.
Vulnerability Scanning
Vulnerability scanning plays a preemptive role in maintaining security by detecting and analyzing threats in CI/CD pipelines. Through regularly scanning code, dependencies, and infrastructure, organizations can identify and address vulnerabilities before they become exploitable.
Automate Security Testing
Integrate automated security testing tools, such as dynamic application security testing (DAST), into the CI/CD pipeline. These tools scan the application for vulnerabilities, misconfigurations, and other security issues, providing developers with timely feedback and enabling them to address security concerns.
Employ Continuous Monitoring
Implement continuous monitoring of the CI/CD pipeline and the deployed applications. This includes logging, log analysis, and intrusion detection systems to detect and respond to security incidents in real time. Monitoring can help identify unauthorized access attempts, unusual behavior, and indicators of compromise.
Enforce Separation of Duties
Implement separation of duties by ensuring that different individuals or teams assume responsibility for different stages of the CI/CD pipeline. This practice helps prevent unauthorized changes, reduces the risk of insider threats, and supports accountability.
Regularly Update Dependencies
Keep dependencies, including third-party libraries and frameworks, up to date. Regularly update and patch these dependencies to address any security vulnerabilities that may be discovered over time. Use dependency management tools to automate the update process and ensure the use of trusted and secure components.
Conduct Threat Modeling
Take a proactive approach to identifying, assessing, and mitigating potential security threats and vulnerabilities. This means analyzing the architecture, design, and functionality of the system or application to flesh out attack vectors and weak points lacking security controls.
By systematically evaluating threats and their potential impact, you can prioritize your security efforts and effectively allocate resources. Threat modeling will equip you to make informed decisions and ensure your security measures align with the needs and context of the system or application.
Practice Secure Secrets Handling
Implement secure secrets handling practices, such as encrypting secrets at rest and in transit, using strong encryption algorithms, and restricting access to secrets based on the principle of least privilege. Leverage secrets management tools and avoid hard-coding secrets in configuration files or source code.
Regularly Audit and Review Access Controls
Conduct audits to review access controls within the CI/CD pipeline. Ensure that access privileges are assigned based on job roles, remove unnecessary access rights and promptly revoke access for individuals who no longer require it.
Foster a Culture of Security
Embrace DevSecOps principles and promote a culture of security awareness and education among development teams. Provide training on secure coding practices, CI/CD security principles, and the importance of adhering to security policies. Encourage reporting of security issues or potential vulnerabilities.