What is EDR vs. XDR? | Palo Alto Networks
EDR (endpoint detection and response) and XDR (extended detection and response) are both cybersecurity solutions that help organizations detect, investigate, and respond to security incidents. However, they differ in their scope and capabilities.
Get the Full Audiobook to Boost Your XDR Knowledge
EDR and XDR Explained
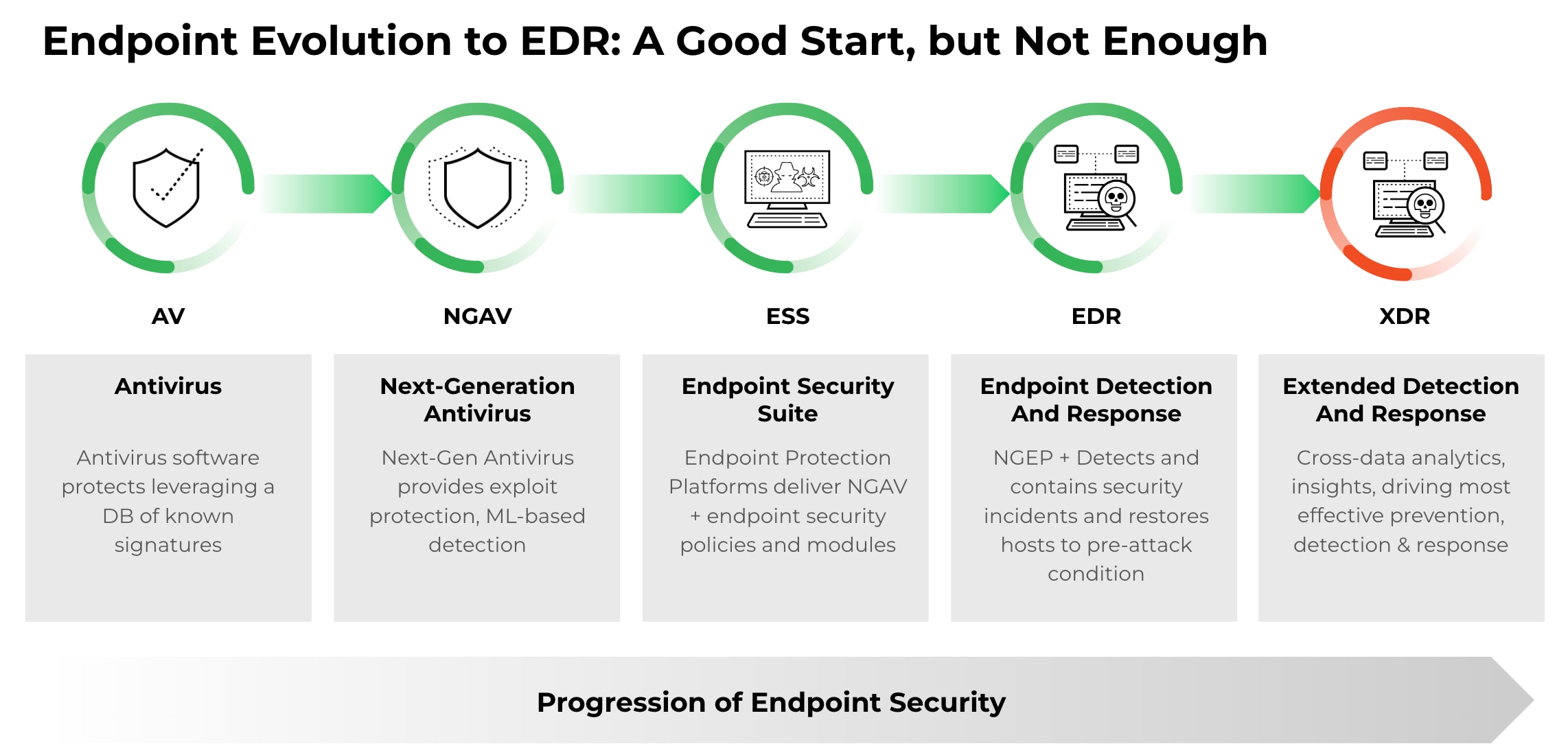
The number of endpoints continues to increase across organizations and no longer consists of just traditional end-user computing devices, such as laptops and workstations. The increase in remote work has also increased the need to secure and monitor various endpoints and endpoint-to-endpoint connections across the entire environment.
With endpoints continuing to be a main entry point for cyberattacks, endpoint security strategies have become a critical need for businesses. Antivirus alone is no longer enough to protect against sophisticated cyberthreats.
Endpoint detection and response (EDR) focuses on endpoint security and provides visibility and control over endpoints such as desktops, laptops, and mobile devices. EDR solutions monitor endpoint activities and behaviors to detect and respond to security incidents. They provide detailed information about each endpoint, such as process activity, file changes, network connections, and system events, which enable security teams to quickly identify and respond to threats.
On the other hand, extended detection and response (XDR) takes a broader enterprise approach and provides security teams with a holistic view of the organization's security posture to make fast informed detection and response decisions. XDR natively integrates data from multiple security products, including EDR, network security, cloud security, and email security, to provide a unified view of security threats across the organization.
Typically, these various security solutions are unified and offered by an XDR vendor, but XDR may support third-party technologies via partnerships or preconfigured seamless integrations. XDR solutions use advanced analytics and machine learning algorithms to identify and prioritize threats, automate incident response workflows, and provide actionable insights to improve security operations. XDR also applies continuously updated threat intelligence to add context and drive better detections.
Importance of EDR and XDR in Cybersecurity
EDR and XDR are both important components of a modern cybersecurity strategy. Here are some reasons why:
- Detect and respond to threats: Both solutions help organizations detect and respond to security threats. EDR solutions provide detailed visibility and control over endpoints, enabling security teams to quickly identify and respond to threats. XDR solutions provide a more comprehensive view of an organization's security posture, enabling security teams to detect and respond to threats across multiple security domains.
- Improve incident response: By providing detailed information about security incidents, EDR solutions enable security teams to quickly investigate and respond to incidents. XDR solutions can automate incident response workflows, enabling security teams to respond to incidents faster and more efficiently.
- Reduce risk: By providing continuous monitoring and detection capabilities, EDR, and XDR solutions can detect threats before they cause significant damage. This helps organizations mitigate the impact of security incidents and reduce the likelihood of a successful cyberattack.
- Enhance visibility: By collecting and analyzing security data from multiple sources, security teams can gain a better understanding of their organization's security strengths and weaknesses. This enables them to identify areas for improvement and make data-driven decisions about security investments.
EDR vs. XDR: Key Differences
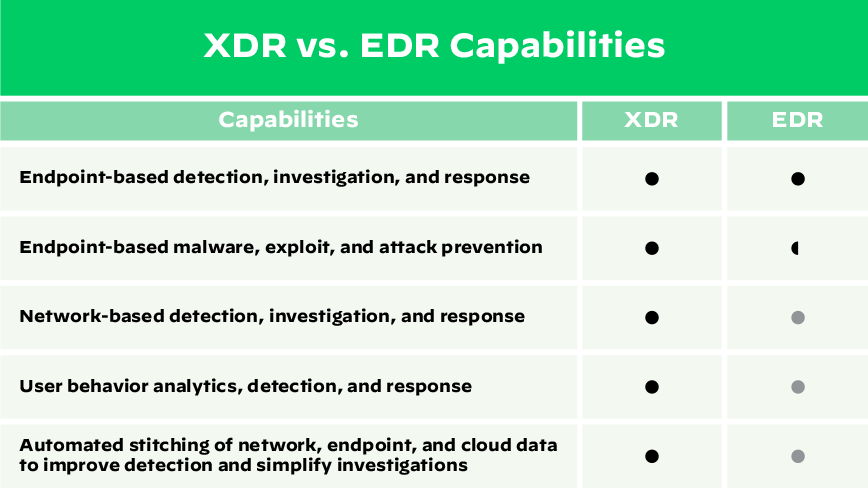
XDR is not the same as EDR. It represents a new and more evolved security solution that takes endpoint security to the next level by providing more robust capabilities than traditional EDR solutions.
While EDR provides necessary and effective protection against endpoint attacks, protection is limited to only what is analyzed from endpoint data. XDR is an evolution of EDR, extending protection beyond the endpoint by analyzing multiple sources of telemetry to protect and detect various attack techniques, combining the capabilities associated with separate SIEM, UEBA, NDR, and EDR tools. XDR correlates and stitches together this rich data and groups together related alerts in one consolidated web interface in order to simplify investigation and response.
Coverage
While XDR and EDR both provide detection and response, they differ in their coverage.
EDR solutions typically focus on endpoint security, meaning they monitor and protect individual endpoints (such as laptops, desktops, and servers) from potential cyberthreats. EDR may include features such as real-time threat detection, malware analysis, and incident response.
In contrast, XDR solutions are designed to provide a more comprehensive approach to cybersecurity by combining and correlating data from multiple sources beyond just endpoints, such as network traffic, cloud services, and email. This allows XDR solutions to identify and respond to threats that may not be apparent from a single endpoint. As such, XDR provides a more complete view of the security posture of an organization, enabling faster and more accurate threat detection and response.
Detection and Response Capabilities
EDR uses techniques such as signature-based detection, behavioral analysis, and machine learning algorithms to detect threats at the endpoint level. Once a threat is detected, EDR can initiate an appropriate response, such as isolating the infected endpoint, terminating a malicious process, or quarantining a file.
XDR expands on EDR by collecting and analyzing data from network traffic, identity, cloud services, and other sources. This allows XDR solutions to identify complex and advanced threats, such as those that involve lateral movement or data exfiltration that may be missed by traditional EDR solutions. XDR also offers a broader range of response capabilities beyond just endpoint isolation or process termination.
Data Aggregation and Correlation
The key differences in data aggregation and correlation between EDR and XDR are as follows:
Data Sources: EDR typically collects data only from endpoints, such as logs, events, and telemetry data generated by endpoint security tools. XDR collects and aggregates data from multiple sources, including EDR, network security devices, cloud services, identity, and email security solutions.
Data Correlation: EDR generally correlates data only from a single endpoint, using techniques such as behavioral analysis, machine learning algorithms, and threat intelligence feeds while XDR correlates data from multiple sources, using advanced analytics and machine learning techniques to identify patterns and anomalies that may indicate a potential threat.
Data Analysis: EDR typically analyzes data at the endpoint level, with limited visibility into the broader security environment. XDR analyzes data from multiple sources, providing a more holistic view of the security posture of an organization, enabling identification and response to complex and advanced threats that may involve multiple attack vectors.
Integration and Automation
The differences in integration and automation capabilities between XDR and EDR are as follows:
Integration: EDR typically integrates with other endpoint security tools, such as antivirus software, endpoint protection platforms, and security information and event management (SIEM) systems. EDR can also integrate with network security tools to provide a more complete view of an attack. XDR is designed to integrate with multiple security tools across the entire security stack, including network security, identity, cloud security, and email security.
Automation: EDR provides automation capabilities for common response actions, such as endpoint isolation, process termination, and file quarantine. When XDR is paired with a SOAR solution it can provide more advanced automation capabilities that span multiple security layers, such as network segmentation, access control, and cloud workload protection. XDR can automate complex response workflows that involve multiple security tools and teams, reducing the time to detect and respond to threats.
Orchestration: XDR provides orchestration capabilities that allow security teams to define and automate response workflows across multiple security tools and teams. XDR solutions can leverage artificial intelligence (AI) and machine learning (ML) algorithms to suggest and automate response actions based on the severity of a threat and the potential impact on the business, while EDR typically provides limited orchestration capabilities, primarily focused on automating response actions at the endpoint level.
Which Is Better: EDR or XDR?
EDR is a great solution to protect, detect, and respond to advanced attacks that target endpoints. But XDR takes endpoint protection to the next level to block more sophisticated threats that are able to bypass the endpoint.
For example, an attacker may use malware to infiltrate targeted networks by compromising an endpoint. Thanks to EDR, this malware was eventually detected and removed from the end-user device. However, what EDR solutions cannot see is that after the endpoint was initially compromised, the attacker was able to quietly move laterally through the network. If gone unnoticed, this stealthy type of attack provides adversaries with the ability to gain access to systems, user credentials, and sensitive data.
With XDR, these attack techniques can be quickly and accurately detected. XDR solutions ingest the broadest amount of data—including network, endpoint, cloud, and identity data—and stitch it together to build profiles of user and device behavior. If a normal user exhibits administrative behavior, such as managing remote machines or accessing systems normally not used, then the user’s machine might be compromised. This helps SOC teams quickly detect behavioral anomalies for further investigation and response.
Pros and Cons of EDR
EDR provides a targeted approach to endpoint security with the ability to quickly detect and respond to endpoint-specific threats. However, EDR has limitations in scope, may generate false positives, have a primarily reactive approach, and require skilled personnel to properly manage the solution. Some pros and cons include:
Pros:
- Focused on endpoint security: EDR solutions are specifically designed to detect and respond to threats at the endpoint level. This provides a targeted approach to endpoint security and enables quick identification and response to endpoint-specific threats.
- Behavioral analysis: EDR uses behavioral analysis to detect anomalies in endpoint activity that may indicate a potential threat. This approach is more effective than traditional signature-based detection, as it can detect new and unknown threats.
- Quick response: EDR can initiate a quick response to detected threats, such as isolating an infected endpoint, terminating a malicious process, or quarantining a file. This helps to prevent the spread of malware and minimize the impact of an attack.
- Integration: EDR can integrate with other security tools, such as antivirus software, endpoint protection platforms, and SIEM systems, to provide a more comprehensive view of an attack and a faster response.
Cons:
- Limited scope: EDR focuses primarily on endpoint security and may not provide a complete view of an attack that involves multiple vectors or targets.
- False positives: EDR may generate false positives, as they rely on behavioral analysis to detect threats. This can lead to unnecessary alerts and additional workload for security teams.
- Reactive approach: EDR is primarily reactive, detecting, and responding to threats after they occur. This may not be effective against advanced and persistent threats, which may require a more proactive approach.
- Skill requirements: EDR requires skilled personnel to properly configure and manage the solution, interpret and respond to alerts, and analyze data for threat detection.
Pros and Cons of XDR
XDR provides a comprehensive and holistic approach to threat detection and response, with advanced automation and orchestration capabilities. However, XDR solutions can be expensive and complex to implement and maintain, require skilled personnel to manage, and may generate false positives.
Pros of XDR:
- Comprehensive view: XDR provides a comprehensive view of an organization's security posture across multiple security layers, such as endpoint, identity, network, cloud, and email security, providing a holistic approach to threat detection and response.
- Correlation and context: XDR uses advanced correlation and context analysis to identify and prioritize potential threats, reducing the number of false positives and helps to focus the security team's efforts on the most critical threats.
- Automation and orchestration: XDR provides advanced automation and orchestration capabilities that span multiple security layers, enabling faster and more effective response to threats. This reduces the time to detect and respond to threats and minimizes the impact of an attack.
- Integration: XDR integrates with multiple security tools across the entire security stack.
Cons of XDR:
- Cost: XDR solutions can be expensive to implement and maintain, as they require integration with multiple security tools and ongoing support and management.
- Skill requirements: XDR requires skilled personnel to properly configure and manage the solution, interpret and respond to alerts, and analyze data for threat detection.
- Complexity: XDR can be complex to configure and manage, especially for organizations with limited security resources and expertise.
Factors to Consider When Choosing Between EDR and XDR
When choosing between EDR and XDR solutions, organizations should consider their security needs, budget, resources, complexity, integration capabilities, false positive rate, and compliance requirements:
Security Needs
Organizations should assess their security needs and determine whether a targeted approach to endpoint security (EDR) is sufficient, or if a more comprehensive approach that includes multiple security layers (XDR) is necessary.
Budget
XDR solutions are typically more expensive than EDR solutions due to the additional security layers and integration capabilities. Organizations should consider their budget and determine if the added cost of an XDR solution is justifiable.
Resources
XDR solutions require skilled personnel to properly configure and manage the solution, interpret and respond to alerts, and analyze data for threat detection. Organizations should assess their security resources and determine if they have the expertise to manage an XDR solution.
Complexity
XDR solutions can be complex to configure and manage, especially for organizations with limited security resources and expertise. Organizations should consider the complexity of an XDR solution and determine if they have the resources and expertise to manage the solution effectively.
Integration
XDR solutions integrate with multiple security tools across the entire security stack, providing a more comprehensive view of an organization's security posture and enabling faster response to threats. Organizations should assess their existing security tools and determine if integration with an XDR solution is necessary.
Compliance
Organizations in regulated industries may have specific compliance requirements that dictate the level of security required. Organizations should consider their compliance requirements and determine if an EDR or XDR solution meets those requirements.
Future Outlook for EDR and XDR
The future outlook for EDR and XDR solutions is positive, with a growing focus on convergence, AI and ML, automation and orchestration, cloud security integration, and managed services. These trends reflect the ongoing evolution of cyberthreats, and the need for organizations to adopt a more proactive and integrated approach to threat detection and response including the following:
Convergence of EDR and XDR
There is a growing trend toward the convergence of EDR and XDR solutions, as organizations seek a more comprehensive and integrated approach to threat detection and response. Vendors are increasingly offering solutions that combine endpoint, network, cloud, and email security in a single platform.
Adoption of AI and Machine Learning
EDR and XDR solutions are increasingly incorporating artificial intelligence (AI) and machine learning (ML) to improve threat detection and response. These technologies can automate the detection of advanced threats, reduce false positives, and improve incident response times.
Increased Focus on Automation and Orchestration
As the volume and complexity of threats continue to increase, EDR and XDR solutions are placing more emphasis on automation and orchestration. These capabilities can help organizations to respond faster and more effectively to threats, and reduce the workload of security teams.
Integration with Cloud Security
As organizations increasingly adopt cloud-based applications and infrastructure, EDR and XDR solutions are integrating with cloud security tools to provide a more comprehensive view of an organization's security posture. This includes integration with cloud access security brokers (CASBs), cloud security posture management (CSPM) tools, and cloud workload protection platforms (CWPPs).
Shift Toward Managed Services
As EDR and XDR solutions become more complex and resource-intensive to manage, some organizations are turning to managed service providers (MSPs) for support. MSPs can provide expertise and resources that organizations may not have in-house, and can help to reduce the burden of managing and maintaining these solutions.
Additional Resource
Listen to the XDR for Dummies Guide Audiobook
